
Deputy CTO at @onyphe.io | http://onyphe.io
Managing your attack surface... from Europe 👀
Opinions : all mine
Special skill : machine empathy

<goes back to day job>
<goes back to day job>
- get phones out of bedrooms
- ensure teens go out with charged devices
- never have to look for a charger

- get phones out of bedrooms
- ensure teens go out with charged devices
- never have to look for a charger
Thanks iPhone for the ALT text
Thanks iPhone for the ALT text
😨 that's a national telecom network dying of thirst for power

😨 that's a national telecom network dying of thirst for power
I just tried *new* Outlook on Windows. What have you done?
+ve : multithreading
-ve : significantly slower
-ve : uses +5x the amount of RAM
-ve : WebView2? seriously? I wanted a serious desktop app not a browser plugin for a website.
nevermind ... I'll just use OWA on Linux

I just tried *new* Outlook on Windows. What have you done?
+ve : multithreading
-ve : significantly slower
-ve : uses +5x the amount of RAM
-ve : WebView2? seriously? I wanted a serious desktop app not a browser plugin for a website.
nevermind ... I'll just use OWA on Linux
Should we also add Ivanti ConnectSecure to this list?

Should we also add Ivanti ConnectSecure to this list?
We get it. You're trying.
Yet the number of open IOS XE WebUI interfaces just keeps going up. The message isn't getting through.

We get it. You're trying.
Yet the number of open IOS XE WebUI interfaces just keeps going up. The message isn't getting through.
www.imf.org/en/Blogs/Art...

www.imf.org/en/Blogs/Art...
This is unique IPs by hosting organization.

This is unique IPs by hosting organization.
I especially like "open source enthusiast" with commit permissions on an apache project. Also a "dubious C2 enthusiast" on the side, yet doesn't mention cyber as an interest. Odd.

I especially like "open source enthusiast" with commit permissions on an apache project. Also a "dubious C2 enthusiast" on the side, yet doesn't mention cyber as an interest. Odd.
i) the github followers list is an eye-opener
ii) Oracle the leading public cloud for once
details below 👇

i) the github followers list is an eye-opener
ii) Oracle the leading public cloud for once
details below 👇
IP 101[.]99.93.144 exposing DCE/RPC protocol on 8th Oct 2024
for the record it also exposed winrm and smb around and before that date
![IP 101[.]99.93.144 exposing DCE/RPC protocol on 8 Oct 2024](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:ufgm36h7cjyxosgqinjysb6z/bafkreihmmc6qqvwfuqgglwcmdnajgbed2a36x2wmeosu7p63fpjrulymv4@jpeg)
IP 101[.]99.93.144 exposing DCE/RPC protocol on 8th Oct 2024
for the record it also exposed winrm and smb around and before that date
first ip I'm looking at : 101[.]99.93.108
B-I-N-G-O
+1000 points in my rigorous CTI methodology
![IP 101[.]99.93.108 exposing dce/rpc protocol on 28 september 2024](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:ufgm36h7cjyxosgqinjysb6z/bafkreigjjgd3zxcecdmssyxuzshflsnys3ygahegjv5dz3grvp4cmy565i@jpeg)
first ip I'm looking at : 101[.]99.93.108
B-I-N-G-O
+1000 points in my rigorous CTI methodology
a Windows box with RPC exposed - well that and everything else. Behind a Mikrotik router by the looks of it
RPC hypothesis rigorous CTI methodology analysis ^^ :
-1 on first IP
+1 on 2nd IP
![a Windows box on IP 185[.]158.248.104 exposing protocols btest, dce/rpc, rdp, smb, ssh and winrm](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:ufgm36h7cjyxosgqinjysb6z/bafkreigzkaugxwcuobv3tn242ehgjuasikkjzxznv2a2sp5pg3q34q5vx4@jpeg)
a Windows box with RPC exposed - well that and everything else. Behind a Mikrotik router by the looks of it
RPC hypothesis rigorous CTI methodology analysis ^^ :
-1 on first IP
+1 on 2nd IP
there are 2.2M results for Windows RPC boxes
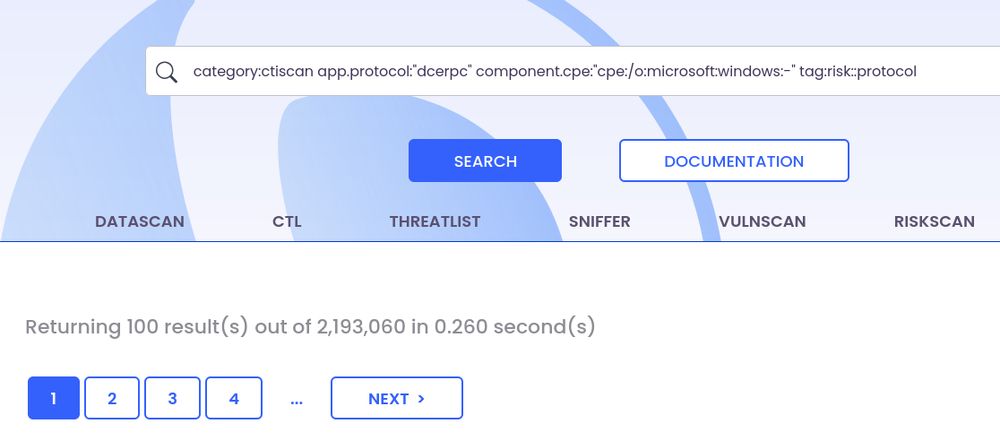
there are 2.2M results for Windows RPC boxes
it's another windows box with SMB 🤦♂️ exposed and based on the IIS version it's an out-of-support Windows Server 2012 R2.
It's still up.
The interesting data point is that it also has dcerpc exposed hmm.
![onyphe screenshot showing ip 65[.]21.245.7 exposing port 445 with smb on the 28 dec 2024. also exposing ports 135 and 80 and showing IIS version 8.5](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:ufgm36h7cjyxosgqinjysb6z/bafkreibw4pl2mhsw25du27ikmt3ne3skttk5mzsi77llautr4l2owephbe@jpeg)
it's another windows box with SMB 🤦♂️ exposed and based on the IIS version it's an out-of-support Windows Server 2012 R2.
It's still up.
The interesting data point is that it also has dcerpc exposed hmm.
nothing currently up but looking back in historical data we've got an RDP box with dcerpc also exposed going back to Sep 24
![onyphe screenshot showing result for IP 111[.]90.140.76 on port 3389 exposing RDP, dated to 3 nov 2024. Also exposing port 135 dcerpc](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:ufgm36h7cjyxosgqinjysb6z/bafkreibi7y6dw2vjqb6g5rjwyovsq6lomwpwr4jl2jih3lvp3x6whc2kem@jpeg)
nothing currently up but looking back in historical data we've got an RDP box with dcerpc also exposed going back to Sep 24

The threat actor gets knocked down, but they get up again ...
#ciscoiosxe

The threat actor gets knocked down, but they get up again ...
#ciscoiosxe
blogs.cisco.com/developer/io...
Meanwhile ... someone else has automated over half of them
This chart is unique IPs.

blogs.cisco.com/developer/io...
Meanwhile ... someone else has automated over half of them
This chart is unique IPs.
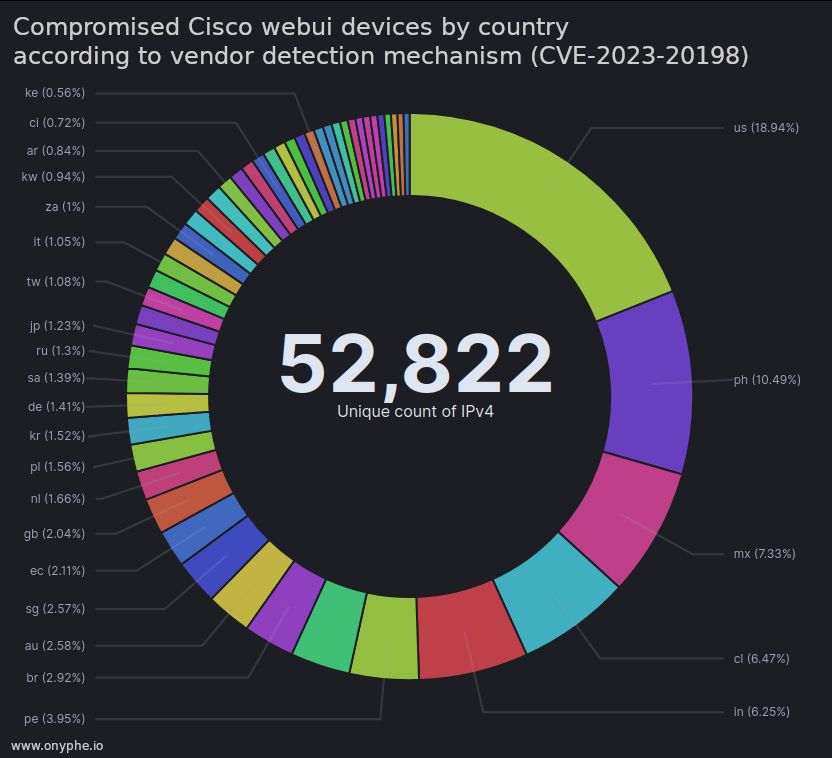
• A MikroTik router in Venezuela
• A hosted linux box in Canada with SSH exposed
The usual suspects

• A MikroTik router in Venezuela
• A hosted linux box in Canada with SSH exposed
The usual suspects

- compromises router/gateway devices
- not doing ransomware
- doesn't run away quietly when discovered
- doubles down and tries to leverage as much as possible
sounds familiar
- compromises router/gateway devices
- not doing ransomware
- doesn't run away quietly when discovered
- doubles down and tries to leverage as much as possible
sounds familiar


