


👉 blog.scrt.ch/2025/02/18/r...
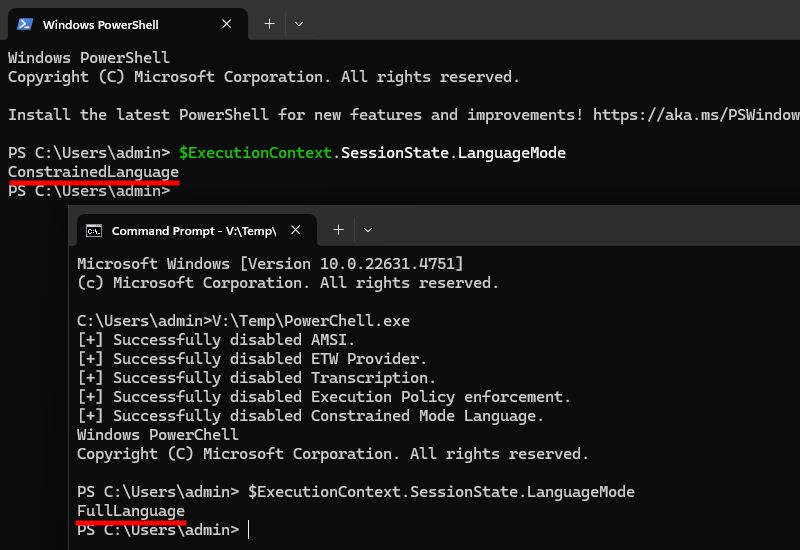
👉 blog.scrt.ch/2025/02/18/r...
www.synacktiv.com/publications...
www.synacktiv.com/publications...
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...

"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
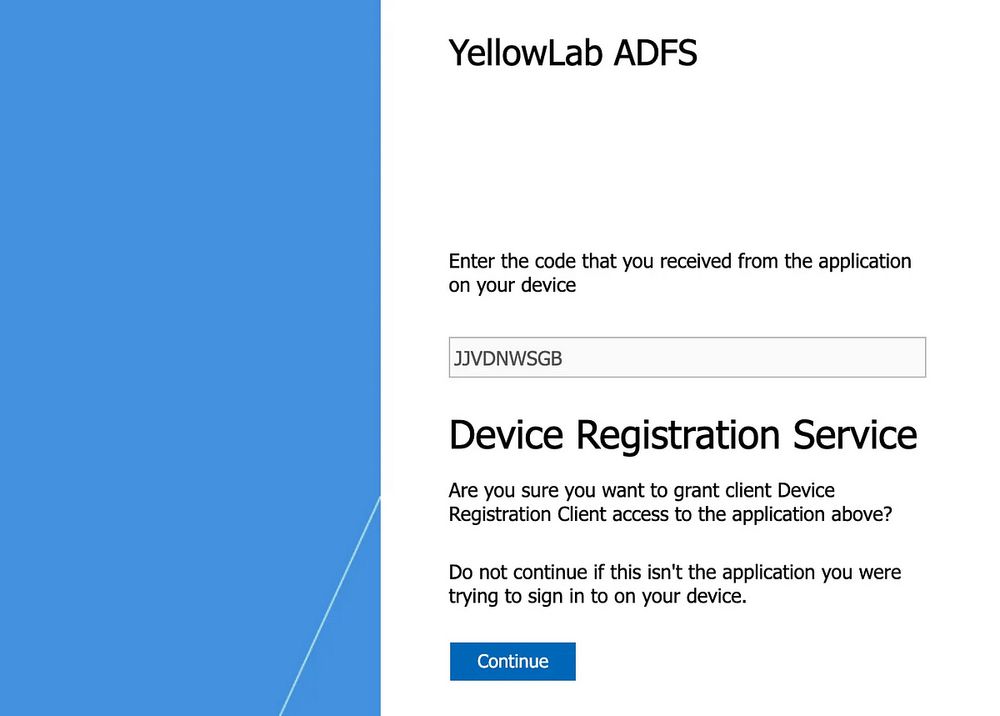
Here is an example with ldeep using relayed authentication from HTTP to LDAPs :

Here is an example with ldeep using relayed authentication from HTTP to LDAPs :

Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
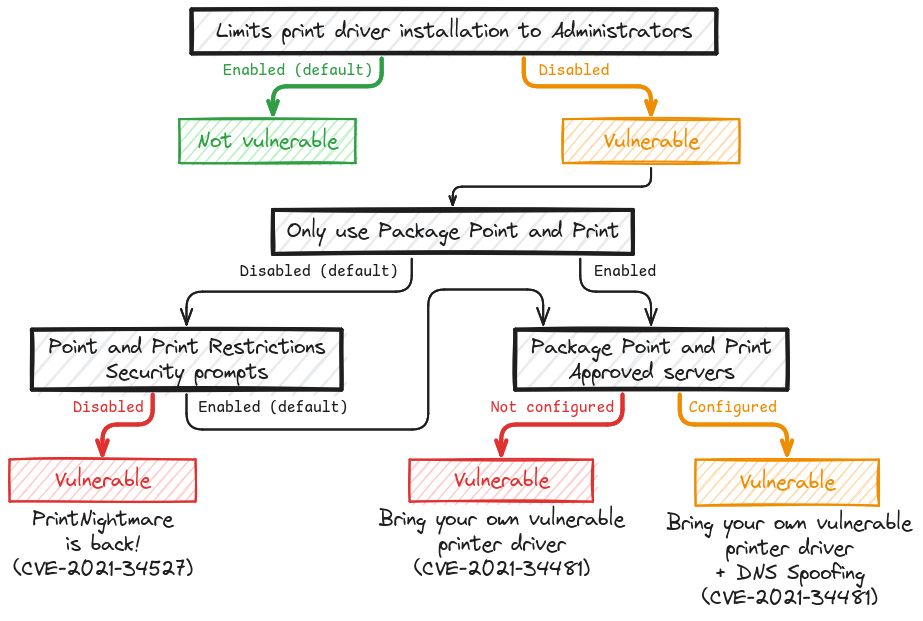
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞

▪ Moved endpoint related stuff to new module: AADInternals-Endpoints
▪ Added blue team stuff
▪ Added red team stuff
See full change log at: aadinternals.com/aadinternals...

▪ Moved endpoint related stuff to new module: AADInternals-Endpoints
▪ Added blue team stuff
▪ Added red team stuff
See full change log at: aadinternals.com/aadinternals...
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...


