May the Encryption be with you
#cybersecurityAwareness


#cybersecurity #ethicalhacking #ethicalhacker #linux #cybersecurityawareness
#cybersecurity #ethicalhacking #ethicalhacker #linux #cybersecurityawareness

- userID
- user_ID
- UserID
- userId
- user-id
- userID
- user_ID
- UserID
- userId
- user-id


#TeachersDay2025
#TeachersDay2025
#TeachersDay2025
#TeachersDay2025
#TeachersDay2025
#TeachersDay2025
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
#CapCut #PrivacyWarning #Cybersecurity #DataPrivacy #DigitalSafety
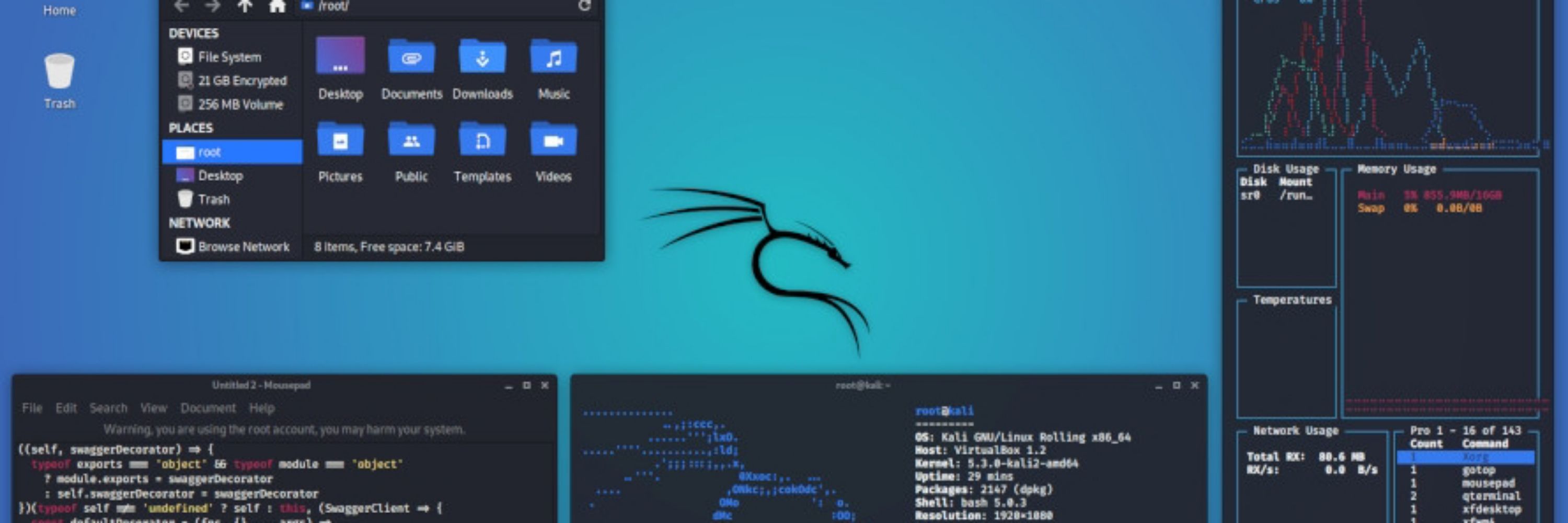
When your system can't locate the necessary boot files, GRUB Rescue Mode is activated. It's a troubleshooting environment that helps manually fix issues like missing or corrupted operating system files.
#CyberSecurity #ethicalhacking #linux
@ishowcybersecurity
When your system can't locate the necessary boot files, GRUB Rescue Mode is activated. It's a troubleshooting environment that helps manually fix issues like missing or corrupted operating system files.
#CyberSecurity #ethicalhacking #linux
@ishowcybersecurity
Next.js is a React framework for building full-stack web applications. Prior to 14.2.25 and 15.2.3, it is possible to bypass authorization checks within a Next.js application, if the authorization check occurs in middleware.
nvd.nist.gov/vuln/detail/...
Next.js is a React framework for building full-stack web applications. Prior to 14.2.25 and 15.2.3, it is possible to bypass authorization checks within a Next.js application, if the authorization check occurs in middleware.
nvd.nist.gov/vuln/detail/...


