
It lets attackers steal machine keys & access system files, leading to RCE. Exploitation has already been seen in the wild.
Get the full analysis: cvemon.intruder.io/cves/CVE-202...

It lets attackers steal machine keys & access system files, leading to RCE. Exploitation has already been seen in the wild.
Get the full analysis: cvemon.intruder.io/cves/CVE-202...

With knowledge of your entire Intruder account, he helps you validate and prioritize issues, remediate with confidence, create clear stakeholder updates, and more.
Learn more: www.intruder.io/blog/greg-ai...
With knowledge of your entire Intruder account, he helps you validate and prioritize issues, remediate with confidence, create clear stakeholder updates, and more.
Learn more: www.intruder.io/blog/greg-ai...
Available on GitHub, Autoswagger is our free, open‑source tool that finds unauthenticated #APIs leaking sensitive data like credentials or PII.
Learn more: www.intruder.io/research/bro...
#APISecurity
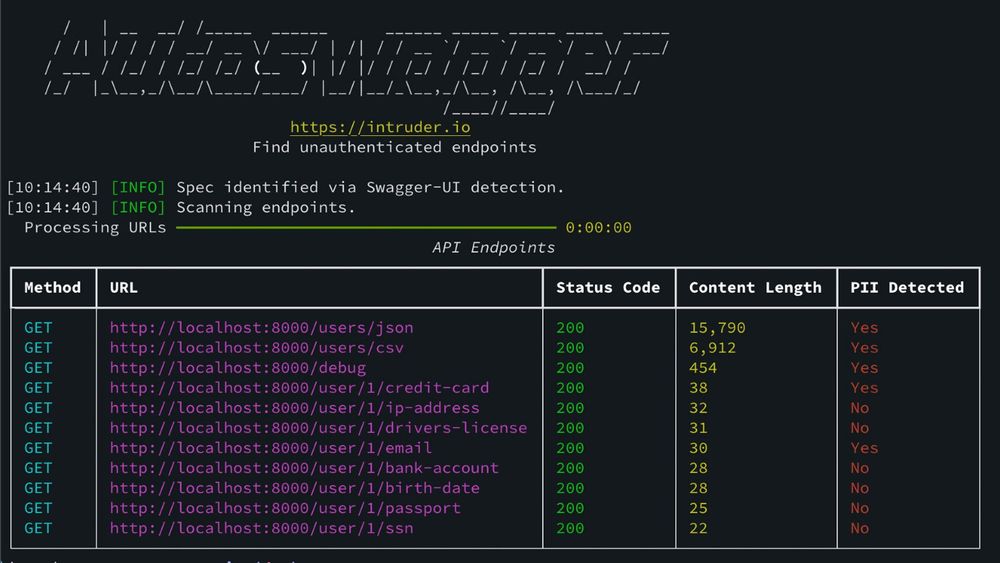
Available on GitHub, Autoswagger is our free, open‑source tool that finds unauthenticated #APIs leaking sensitive data like credentials or PII.
Learn more: www.intruder.io/research/bro...
#APISecurity
📖 Read more: www.helpnetsecurity.com/2025/07/24/a...
#cybersecurity #cybersecuritynews #opensource #APIsecurity @intruder-io.bsky.social

📖 Read more: www.helpnetsecurity.com/2025/07/24/a...
#cybersecurity #cybersecuritynews #opensource #APIsecurity @intruder-io.bsky.social
Intruder is the first VM solution we’re aware of to release an active check.
👉 Start a free trial to detect vulnerable SharePoint instances: portal.intruder.io/free_trial

Intruder is the first VM solution we’re aware of to release an active check.
👉 Start a free trial to detect vulnerable SharePoint instances: portal.intruder.io/free_trial
Get our latest guidance: cvemon.intruder.io/cves/CVE-202...

Get our latest guidance: cvemon.intruder.io/cves/CVE-202...
Our active check is live, so you can find out fast if you're at risk.
👉 Sign up for free to scan your environment today: portal.intruder.io/free_trial

Our active check is live, so you can find out fast if you're at risk.
👉 Sign up for free to scan your environment today: portal.intruder.io/free_trial
The issue is caused by the installer using hardcoded values for the validation and decryption key.
Get the latest from our security team: intel.intruder.io/cves/CVE-202...

The issue is caused by the installer using hardcoded values for the validation and decryption key.
Get the latest from our security team: intel.intruder.io/cves/CVE-202...
🔴 CVSS: Critical (9.1)
📈 intel.intruder.io hype score: 99 ("it's getting all log4shell")
The advice? Patch now. Get the latest commentary from Intruder’s security team: intel.intruder.io/cves/CVE-202...

🔴 CVSS: Critical (9.1)
📈 intel.intruder.io hype score: 99 ("it's getting all log4shell")
The advice? Patch now. Get the latest commentary from Intruder’s security team: intel.intruder.io/cves/CVE-202...
With SSL certificate expirations making headlines, it’s a reminder of how important it is to have a reliable way to track renewals.
Want to see how easy it is with Intruder? Try it for free:
portal.intruder.io/free_trial
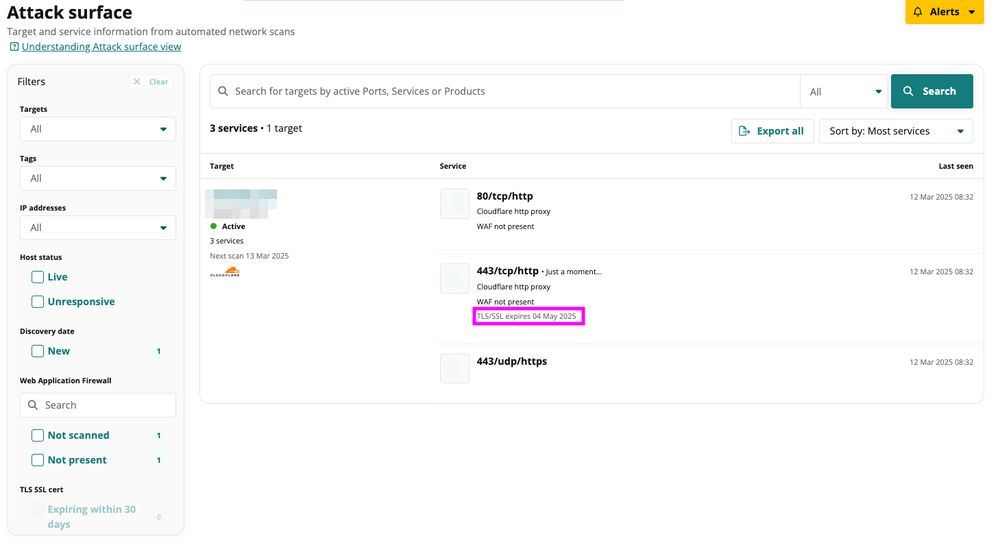
With SSL certificate expirations making headlines, it’s a reminder of how important it is to have a reliable way to track renewals.
Want to see how easy it is with Intruder? Try it for free:
portal.intruder.io/free_trial
Our research shows broken authentication issues in APIs are far more common than you’d think, with some bugs going undetected for years.
Read more: www.intruder.io/research/oct...

Our research shows broken authentication issues in APIs are far more common than you’d think, with some bugs going undetected for years.
Read more: www.intruder.io/research/oct...
But how will this compare to #AWS security services like GuardDuty, Inspector, and Config?
Learn more and signup to be the first to know when cloud security launches: www.intruder.io/blog/aws-sec...

But how will this compare to #AWS security services like GuardDuty, Inspector, and Config?
Learn more and signup to be the first to know when cloud security launches: www.intruder.io/blog/aws-sec...
Read the full breakdown:
intruder.io/research/sim...

Read the full breakdown:
intruder.io/research/sim...
👉 See our latest analysis on Intel: hubs.li/Q036zXVf0

👉 See our latest analysis on Intel: hubs.li/Q036zXVf0
Check it out👉 intel.intruder.io
#VulnerabilityIntelligence #CVE #CyberSecurity
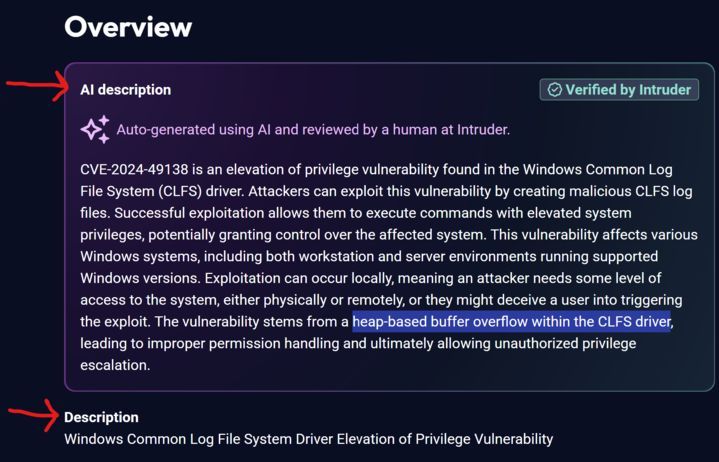
Check it out👉 intel.intruder.io
#VulnerabilityIntelligence #CVE #CyberSecurity
We quickly assessed the threat and developed an active check - before one was available from our underlying scanners.
Stay ahead of the latest developments: intel.intruder.io/cves/CVE-202...

We quickly assessed the threat and developed an active check - before one was available from our underlying scanners.
Stay ahead of the latest developments: intel.intruder.io/cves/CVE-202...
The #vulnerability allows unauthenticated attackers to create administrative accounts. #Fortinet has released IoCs to help identify suspicious activity.
intel.intruder.io/cves/CVE-202...

The #vulnerability allows unauthenticated attackers to create administrative accounts. #Fortinet has released IoCs to help identify suspicious activity.
intel.intruder.io/cves/CVE-202...
We recommend prioritizing it over other criticals, but due to its complexity, don't expect widespread exploitation.
Get the latest from our Security Team: intel.intruder.io/cves/CVE-202...
#CyberSecurity #InfoSec

We recommend prioritizing it over other criticals, but due to its complexity, don't expect widespread exploitation.
Get the latest from our Security Team: intel.intruder.io/cves/CVE-202...
#CyberSecurity #InfoSec
Find out more: intel.intruder.io/cves/CVE-202...
#CyberSecurity #CVE202449112 #InfoSec #Microsoft

Find out more: intel.intruder.io/cves/CVE-202...
#CyberSecurity #CVE202449112 #InfoSec #Microsoft
☁️ Auto-discovered the system via our cloud connector
✅ Deployed a check before our underlying scanners
🚨 Notified the customer so they could fix the issue
Learn more: shorturl.at/lf8wW

☁️ Auto-discovered the system via our cloud connector
✅ Deployed a check before our underlying scanners
🚨 Notified the customer so they could fix the issue
Learn more: shorturl.at/lf8wW
It was initially thought that the patch was insufficient due to ongoing exploitation, but it turns out there is a second unauthenticated RCE.
More info: intel.intruder.io/cves/CVE-202...

It was initially thought that the patch was insufficient due to ongoing exploitation, but it turns out there is a second unauthenticated RCE.
More info: intel.intruder.io/cves/CVE-202...
CVE-2024-42327, a critical vulnerability in #Zabbix, has received the most buzz in the last 24hrs. But with a hype score of 9/100, it's looking like a calm day in the threat landscape so far.
Check it out: intel.intruder.io
#CVE #CyberSecurity
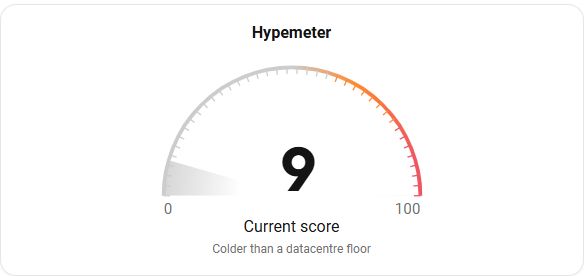
CVE-2024-42327, a critical vulnerability in #Zabbix, has received the most buzz in the last 24hrs. But with a hype score of 9/100, it's looking like a calm day in the threat landscape so far.
Check it out: intel.intruder.io
#CVE #CyberSecurity
CVE-2024-5921, a high-severity flaw in the #PaloAlto Networks GlobalProtect app, has received the most buzz in the last 24hrs. But with a hype score of 5 / 100, it's pretty quiet out there.
Stay ahead with Intel: intel.intruder.io/trends
#CVE #CyberSecurity
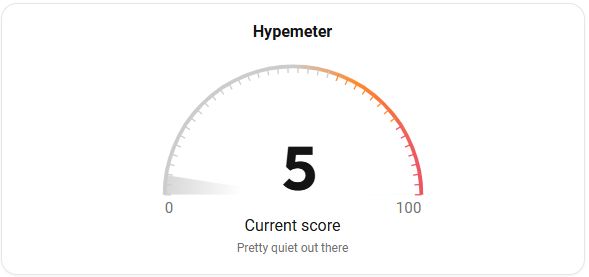
CVE-2024-5921, a high-severity flaw in the #PaloAlto Networks GlobalProtect app, has received the most buzz in the last 24hrs. But with a hype score of 5 / 100, it's pretty quiet out there.
Stay ahead with Intel: intel.intruder.io/trends
#CVE #CyberSecurity

