Calls to this function are then inserted in various places that (legitimately) access the private key.


Calls to this function are then inserted in various places that (legitimately) access the private key.

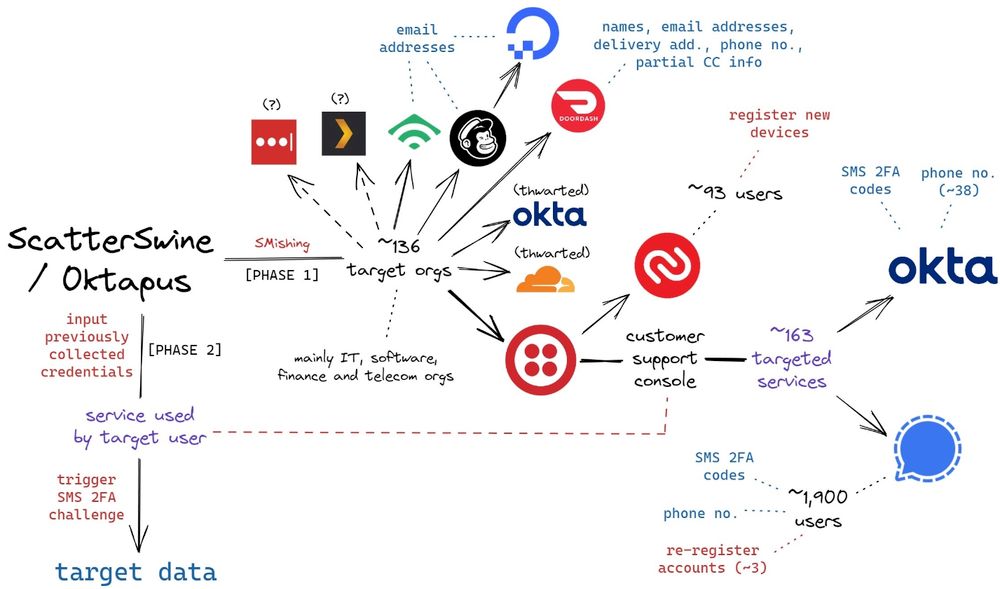


#threat #cybersecurity #iam #identity #itdr

#threat #cybersecurity #iam #identity #itdr

#threat #cybersecurity #iam #identity #itdr
#threat #cybersecurity #iam #identity #itdr

#threat #cybersecurity #iam #identity #itdr
IBM’s identity threat detect and response. ITDR/ISPM solution provides you with end-to-end visibility into user activity across the hybrid landscape of silo’d IAM tools used across cloud, SaaS, and on-prem applications
#threat #cybersecurity
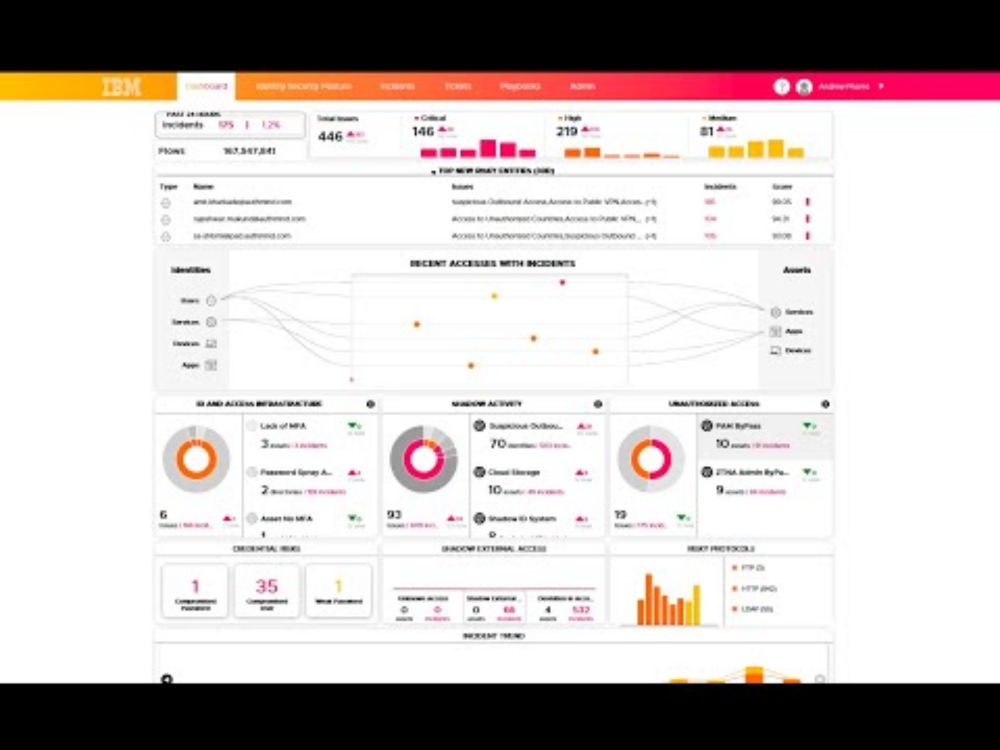
IBM’s identity threat detect and response. ITDR/ISPM solution provides you with end-to-end visibility into user activity across the hybrid landscape of silo’d IAM tools used across cloud, SaaS, and on-prem applications
#threat #cybersecurity

