
DM are welcome for any questions.
--
Website: https://hg8.sh
Post history on Twitter: @_hg8_
An attacker can leverage sudo's -R (--chroot) option to run
arbitrary commands as root, even if they are not listed in the sudoers file.
Sudo versions 1.9.14 to 1.9.17 affected.
www.openwall.com/lists/oss-se... #infosec #cve
An attacker can leverage sudo's -R (--chroot) option to run
arbitrary commands as root, even if they are not listed in the sudoers file.
Sudo versions 1.9.14 to 1.9.17 affected.
www.openwall.com/lists/oss-se... #infosec #cve
Old technique but good writeup
splint.gitbook.io/cyberblog/se... #ctf #tensorflow #ai #infosec
Old technique but good writeup
splint.gitbook.io/cyberblog/se... #ctf #tensorflow #ai #infosec
w4ke.info/2025/06/18/f... #infosec
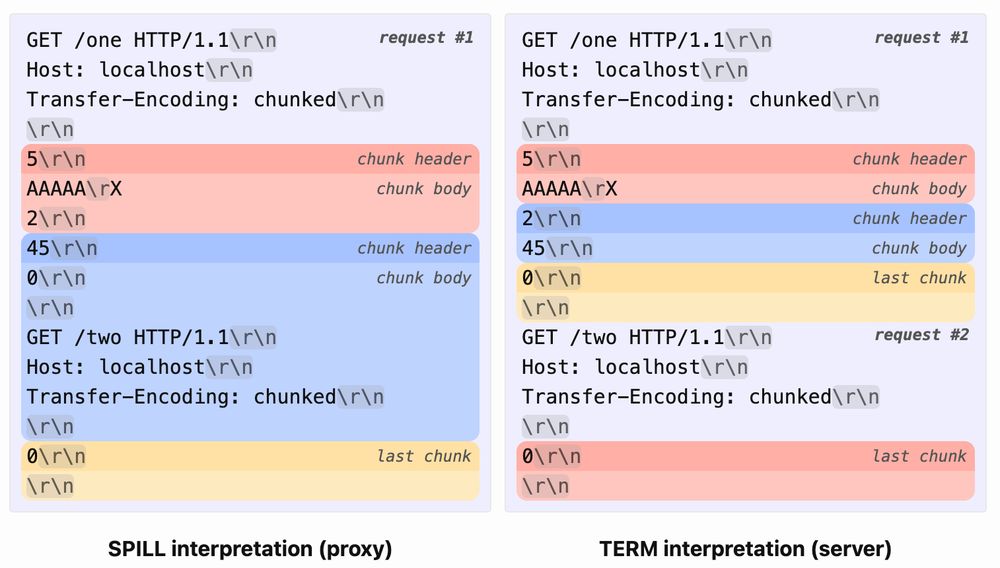
w4ke.info/2025/06/18/f... #infosec
Cool finding. This would make a cool CTF challenge 👍
swap.gs/posts/monero... #rce #ctf
Cool finding. This would make a cool CTF challenge 👍
swap.gs/posts/monero... #rce #ctf
Another good potential for a CTF challenge! 👀
karmainsecurity.com/riding-the-t... #infosec #rce #ctf
Another good potential for a CTF challenge! 👀
karmainsecurity.com/riding-the-t... #infosec #rce #ctf
TL;DR: Through "Confused Deputy" attacks Dependabot (and other GitHub bots), can be tricked into merging malicious code. It can escalate to full command injection via crafted branch names.
boostsecurity.io/blog/weaponi... #infosec
TL;DR: Through "Confused Deputy" attacks Dependabot (and other GitHub bots), can be tricked into merging malicious code. It can escalate to full command injection via crafted branch names.
boostsecurity.io/blog/weaponi... #infosec
Bit outdated (DirectX9) but still some very valuable info and a great writeup 👍
adminions.ca/books/articl... #infosec #re
Bit outdated (DirectX9) but still some very valuable info and a great writeup 👍
adminions.ca/books/articl... #infosec #re
That will make a nice CTF challenge ^
www.8com.de/cyber-securi... #infosec #cve #rce
That will make a nice CTF challenge ^
www.8com.de/cyber-securi... #infosec #cve #rce
invariantlabs.ai/blog/mcp-git...

invariantlabs.ai/blog/mcp-git...
0x44.xyz/blog/cve-202... #infosec #cve #privesc
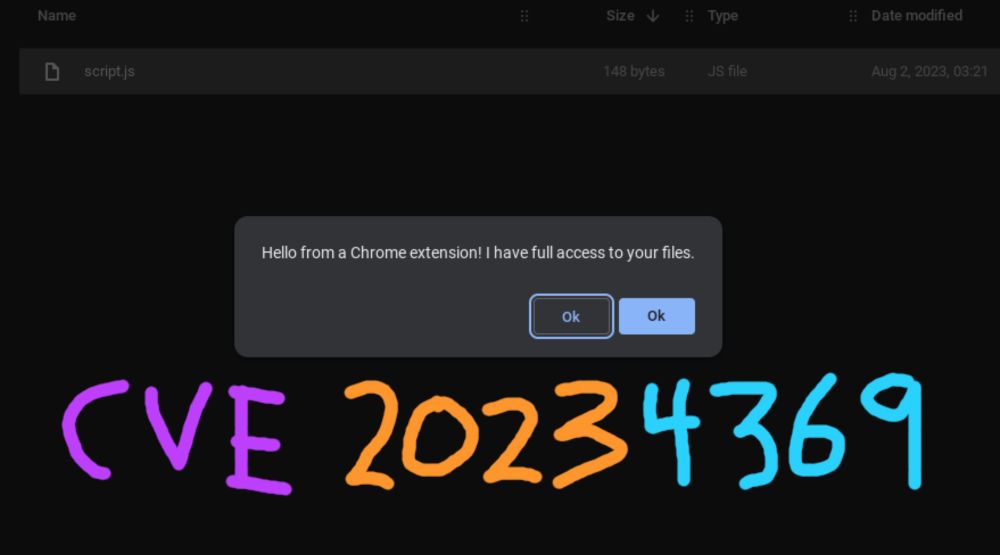
0x44.xyz/blog/cve-202... #infosec #cve #privesc
arxiv.org/abs/2411.03346 #infosec #ai #fuzzing #oss-fuzz

arxiv.org/abs/2411.03346 #infosec #ai #fuzzing #oss-fuzz
karmainsecurity.com/dont-call-th... #infosec #rce #vbulletin
karmainsecurity.com/dont-call-th... #infosec #rce #vbulletin
github.com/ZathuraDbg/Z... #infosec
github.com/ZathuraDbg/Z... #infosec
arxiv.org/pdf/2302.12173
arxiv.org/pdf/2302.12173
blog.castle.io/what-a-binan... #infosec #captcha

blog.castle.io/what-a-binan... #infosec #captcha
Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆
Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆
micahflee.com/ddosecrets-p...

micahflee.com/ddosecrets-p...
something.fromnothing.blog/posts/dolla-... #infosec #reverseengineering

something.fromnothing.blog/posts/dolla-... #infosec #reverseengineering
blog.zsec.uk/commit-stomp... #infosec #redteam

blog.zsec.uk/commit-stomp... #infosec #redteam
Tl;Dr: Writeup reviews the technique for establishing a full stateful TCP connection with a spoofed source IP address from the same subnet using ARP poisoning.
tastypepperoni.medium.com/stateful-con... #infosec
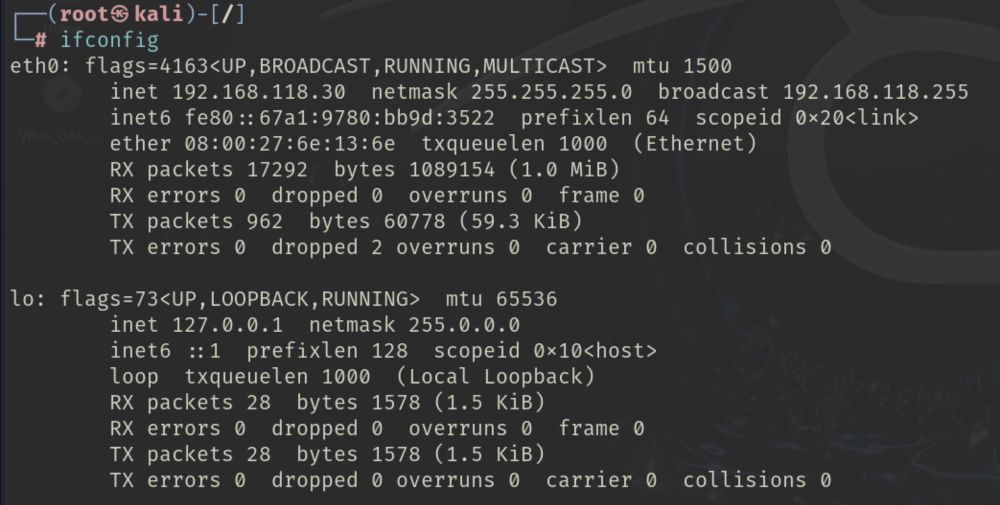
Tl;Dr: Writeup reviews the technique for establishing a full stateful TCP connection with a spoofed source IP address from the same subnet using ARP poisoning.
tastypepperoni.medium.com/stateful-con... #infosec


