HD Moore
@hdm.io
CEO and founder of runZero.com, previously the founder and lead developer of Metasploit, a CSO, a consultant, and the head of various security research teams. Contact info, presentations, and more at https://hdm.io/
JawnCon (jawncon.org) 0x02 just wrapped! I wish I could make it this year, but settled for catching the talks on the live stream:
Main Stage Day 1: www.youtube.com/live/Cvf-mAd...
Man Stage Day 2: www.youtube.com/watch?v=bcr6...
Classroom Day 2: www.youtube.com/watch?v=1aML...
Main Stage Day 1: www.youtube.com/live/Cvf-mAd...
Man Stage Day 2: www.youtube.com/watch?v=bcr6...
Classroom Day 2: www.youtube.com/watch?v=1aML...

October 13, 2025 at 8:43 PM
JawnCon (jawncon.org) 0x02 just wrapped! I wish I could make it this year, but settled for catching the talks on the live stream:
Main Stage Day 1: www.youtube.com/live/Cvf-mAd...
Man Stage Day 2: www.youtube.com/watch?v=bcr6...
Classroom Day 2: www.youtube.com/watch?v=1aML...
Main Stage Day 1: www.youtube.com/live/Cvf-mAd...
Man Stage Day 2: www.youtube.com/watch?v=bcr6...
Classroom Day 2: www.youtube.com/watch?v=1aML...
@SectorCa 2025 is fantastic! I last attended in 2008 and holy cow has it grown. Great to see Brian and Bruce still involved. Excellent talks, really sharp crowd, zero attitude, and everyone is incredibly friendly. You can find the slides from my morning keynote at hdm.io/decks/Sector...

October 2, 2025 at 4:13 PM
@SectorCa 2025 is fantastic! I last attended in 2008 and holy cow has it grown. Great to see Brian and Bruce still involved. Excellent talks, really sharp crowd, zero attitude, and everyone is incredibly friendly. You can find the slides from my morning keynote at hdm.io/decks/Sector...
Looking forward to seeing all you hackers in meatspace! I'm bouncing between tracks and sharing slides (Unconference today + Track 2 tomorrow) on the Discord. If you're at @blueteamcon.com this weekend, please say hi, I look like this:

September 6, 2025 at 7:13 PM
Looking forward to seeing all you hackers in meatspace! I'm bouncing between tracks and sharing slides (Unconference today + Track 2 tomorrow) on the Discord. If you're at @blueteamcon.com this weekend, please say hi, I look like this:
If you missed this talk at BH/DC last week, it's worth a read: "From Spoofing to Tunneling: New Red Team's Networking Techniques for Initial Access and Evasion". Awesome work from Shu-Hao, Tung (123ojp) covering practical attacks on GRE and VxLAN tunnels: media.defcon.org/DEF%20CON%20...

August 13, 2025 at 1:57 AM
If you missed this talk at BH/DC last week, it's worth a read: "From Spoofing to Tunneling: New Red Team's Networking Techniques for Initial Access and Evasion". Awesome work from Shu-Hao, Tung (123ojp) covering practical attacks on GRE and VxLAN tunnels: media.defcon.org/DEF%20CON%20...
Thank you to everyone who made it out for my DEF CON 33 presentation, "Shaking Out Shells With SSHamble", you can find the materials online at hdm.io/decks/MOORE%...
This deck includes some lightly-censored zero-day (more decks @ hdm.io)
This deck includes some lightly-censored zero-day (more decks @ hdm.io)

August 10, 2025 at 9:14 PM
Thank you to everyone who made it out for my DEF CON 33 presentation, "Shaking Out Shells With SSHamble", you can find the materials online at hdm.io/decks/MOORE%...
This deck includes some lightly-censored zero-day (more decks @ hdm.io)
This deck includes some lightly-censored zero-day (more decks @ hdm.io)
Hello DEF CON! Tomorrow (Saturday/August 9th) I'll be speaking with Nicole Schwartz on Forging Strong Cyber Communities in Uncertain Times at 1pm in W205 (TDI) and then shortly after on Shaking Out Shells with SSHamble at 3pm in Track 2 (LV1), with even more shells. Hope to see you there!
August 9, 2025 at 6:36 AM
Hello DEF CON! Tomorrow (Saturday/August 9th) I'll be speaking with Nicole Schwartz on Forging Strong Cyber Communities in Uncertain Times at 1pm in W205 (TDI) and then shortly after on Shaking Out Shells with SSHamble at 3pm in Track 2 (LV1), with even more shells. Hope to see you there!
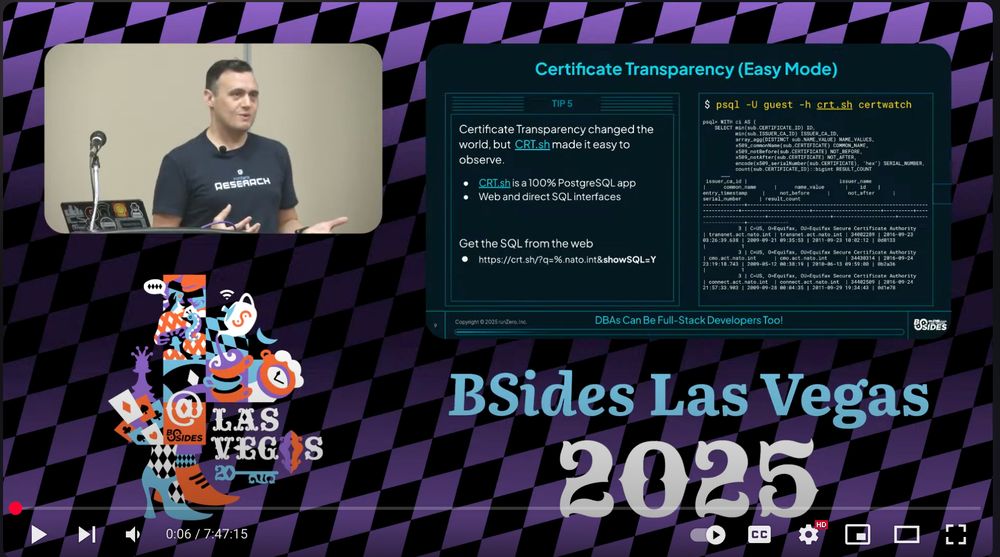
BSides Las Vegas 2025 is incredible. Amazing turn-out, fantastic staff, and the sheer variety of content, speakers, and activities sets the bar for what a hacker con should be. You can find the slides from my talk, "Turbo Tactical Exploitation: 22 Tips for Tricky Targets" at hdm.io/decks/BSides...
August 5, 2025 at 6:02 AM
BSides Las Vegas 2025 is incredible. Amazing turn-out, fantastic staff, and the sheer variety of content, speakers, and activities sets the bar for what a hacker con should be. You can find the slides from my talk, "Turbo Tactical Exploitation: 22 Tips for Tricky Targets" at hdm.io/decks/BSides...
Hello Austin Gophers! The July ATX Go Meetup is TONIGHT (July 9th). The meetup includes lightning talks, pizza, beverages, and general discussion. Have a neat idea? A quick talk related to Go? Something to show-and-tell? www.meetup.com/atxgolang/ev...

July 9, 2025 at 7:45 PM
Hello Austin Gophers! The July ATX Go Meetup is TONIGHT (July 9th). The meetup includes lightning talks, pizza, beverages, and general discussion. Have a neat idea? A quick talk related to Go? Something to show-and-tell? www.meetup.com/atxgolang/ev...
Do you enjoy guzzling real-time TLS certificate allocations, but don't want to use a third-party service (crt.sh, CertStream, etc.)? Drink straight from the Certificate Transparency log firehose using ctail:
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
June 21, 2025 at 5:57 AM
Do you enjoy guzzling real-time TLS certificate allocations, but don't want to use a third-party service (crt.sh, CertStream, etc.)? Drink straight from the Certificate Transparency log firehose using ctail:
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
Tired of using boring web browsers to manage your exposure with runZero? Nostalgic for the days of clean, MS-DOS terminal graphics? Ditch your modern trappings and visualize your network map using the best visualization tool of all time, ToneLoc:
www.runzero.com/blog/subnet-...
www.runzero.com/blog/subnet-...

April 1, 2025 at 1:42 PM
Tired of using boring web browsers to manage your exposure with runZero? Nostalgic for the days of clean, MS-DOS terminal graphics? Ditch your modern trappings and visualize your network map using the best visualization tool of all time, ToneLoc:
www.runzero.com/blog/subnet-...
www.runzero.com/blog/subnet-...
Hoping this helps someone else. When setting up a Supermicro AS-1015A-MT 1U w/H13SAE-MF & Ryzen processor, trying to boot Debian 12 or Proxmox 8.3 media results in "Welcome to Grub" and the machine stalling. The fix? Disconnect the display and use the IPMI KVM (!) forum.proxmox.com/threads/inst...

March 25, 2025 at 10:52 PM
Hoping this helps someone else. When setting up a Supermicro AS-1015A-MT 1U w/H13SAE-MF & Ryzen processor, trying to boot Debian 12 or Proxmox 8.3 media results in "Welcome to Grub" and the machine stalling. The fix? Disconnect the display and use the IPMI KVM (!) forum.proxmox.com/threads/inst...
Today, Wiz (Woogle?) released an advisory detailing an attack chain they’ve dubbed IngressNightmare, which, if left exposed and unpatched, can be exploited to achieve remote code execution by unauthenticated attackers. Read more at www.runzero.com/blog/ingress...

March 25, 2025 at 12:23 AM
Today, Wiz (Woogle?) released an advisory detailing an attack chain they’ve dubbed IngressNightmare, which, if left exposed and unpatched, can be exploited to achieve remote code execution by unauthenticated attackers. Read more at www.runzero.com/blog/ingress...
Good morning from Bootstrap`25[1] in Austin, Texas! Haroon Meer kicks us off with "Security Products Don't Have To Suck", which makes many great points, but among those that most security industry "awards" are hot garbage play-to-win trophies:
1. cfp.ringzer0.training/ringzer0-boo...
1. cfp.ringzer0.training/ringzer0-boo...

March 22, 2025 at 2:57 PM
Good morning from Bootstrap`25[1] in Austin, Texas! Haroon Meer kicks us off with "Security Products Don't Have To Suck", which makes many great points, but among those that most security industry "awards" are hot garbage play-to-win trophies:
1. cfp.ringzer0.training/ringzer0-boo...
1. cfp.ringzer0.training/ringzer0-boo...
Pat Gray, Founder of Risky Business, Joins Decibel as Founder Advisor. Great interview at
www.decibel.vc/articles/pat...
www.decibel.vc/articles/pat...

March 18, 2025 at 4:26 PM
Pat Gray, Founder of Risky Business, Joins Decibel as Founder Advisor. Great interview at
www.decibel.vc/articles/pat...
www.decibel.vc/articles/pat...
Congratulations to Charles Blas for winning the runZero hacktop raffle at CruiseCon 2025! This is a GPD Pocket 3 running Ubuntu Mate, preloaded with a fully licensed, offline version of the runZero Platform. You can find pictures and Charle's take at: https://buff.ly/4b6w0vz

February 20, 2025 at 7:44 PM
Congratulations to Charles Blas for winning the runZero hacktop raffle at CruiseCon 2025! This is a GPD Pocket 3 running Ubuntu Mate, preloaded with a fully licensed, offline version of the runZero Platform. You can find pictures and Charle's take at: https://buff.ly/4b6w0vz
This is still one of my favorite photos from DEF CON 9 (2001). It was taken with an actual film camera from behind the security desk (and about a foot from the staff) in the Imperial Palace. The "diskette" warning is about the Keno machine, the 3.5" floppy contained the random seed for the day.

February 7, 2025 at 3:04 AM
This is still one of my favorite photos from DEF CON 9 (2001). It was taken with an actual film camera from behind the security desk (and about a foot from the staff) in the Imperial Palace. The "diskette" warning is about the Keno machine, the 3.5" floppy contained the random seed for the day.
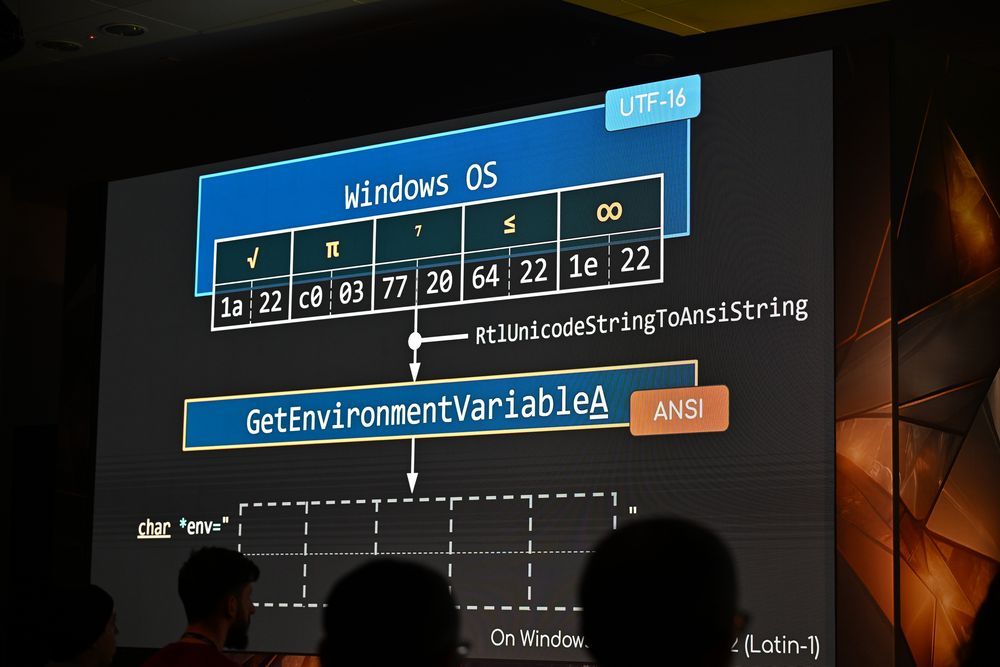
Orange Tsai & splitline's "WorstFit" research into Windows unicode "BestFit" encoding is 🔥 🔥 🔥 (and mostly unpatched)!
https://buff.ly/3PQNT81
This work brings back memories of IIS and ASP (classic) unicode exploit-dev.
https://buff.ly/3PQNT81
This work brings back memories of IIS and ASP (classic) unicode exploit-dev.

January 10, 2025 at 8:26 PM
Orange Tsai & splitline's "WorstFit" research into Windows unicode "BestFit" encoding is 🔥 🔥 🔥 (and mostly unpatched)!
https://buff.ly/3PQNT81
This work brings back memories of IIS and ASP (classic) unicode exploit-dev.
https://buff.ly/3PQNT81
This work brings back memories of IIS and ASP (classic) unicode exploit-dev.
It was much easier to replace my ESXi lab servers with Proxmox than to download a security update[1. see alt text] for ESXi post-Broadcom. Now ESXi runs as a scan target inside of Proxmox and all is well.

December 1, 2024 at 6:28 PM
It was much easier to replace my ESXi lab servers with Proxmox than to download a security update[1. see alt text] for ESXi post-Broadcom. Now ESXi runs as a scan target inside of Proxmox and all is well.
Hello Austin hackers! Tonight is the November AHA meetup (shifted back a week to avoid holiday overlap). Same place and time as usual (Mister Tramps, talks start at 7:00pm). Haven't been to an AHA before? Check out the meeting info (and bring a ~5-10m lightning talk): https://takeonme.org/

November 21, 2024 at 10:39 PM
Hello Austin hackers! Tonight is the November AHA meetup (shifted back a week to avoid holiday overlap). Same place and time as usual (Mister Tramps, talks start at 7:00pm). Haven't been to an AHA before? Check out the meeting info (and bring a ~5-10m lightning talk): https://takeonme.org/
Secure your IoT devices by (accidentally) encasing them in concrete. Fortunately this is a POE doorbell and doesn't require battery changes. It does prevent someone from easily getting to the reset button under the bottom lip; does this count as embedded security?

November 12, 2024 at 1:51 AM
Secure your IoT devices by (accidentally) encasing them in concrete. Fortunately this is a POE doorbell and doesn't require battery changes. It does prevent someone from easily getting to the reset button under the bottom lip; does this count as embedded security?
If the NSA[1], GrapheneOS[2], and Apple[3] all believe that rebooting your mobile phone regularly is something that protects your data, you might consider automating it.
1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0
1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0

November 12, 2024 at 1:02 AM
If the NSA[1], GrapheneOS[2], and Apple[3] all believe that rebooting your mobile phone regularly is something that protects your data, you might consider automating it.
1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0
1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0

