

#Windows Security event log being swamped by 4703 "A token right was adjusted" events? Disable "Audit Authorization Policy Change" by local or group policy. Common with #SCCM
learn.microsoft.com/en-us/previo...

#Windows Security event log being swamped by 4703 "A token right was adjusted" events? Disable "Audit Authorization Policy Change" by local or group policy. Common with #SCCM
learn.microsoft.com/en-us/previo...

"DC=$(($env:USERDNSDOMAIN -split '\.') -join ',DC=')"

"DC=$(($env:USERDNSDOMAIN -split '\.') -join ',DC=')"
I had 4 with me last night although they are smaller & my bed is bigger

I had 4 with me last night although they are smaller & my bed is bigger
github.com/PowerShell/P...

github.com/PowerShell/P...


Get-WinEvent -ListLog * -EA 0 -PipelineVariable log | %{ $log.LogName ; wevtutil.exe clear-log "$($log.LogName)" }


Get-WinEvent -ListLog * -EA 0 -PipelineVariable log | %{ $log.LogName ; wevtutil.exe clear-log "$($log.LogName)" }
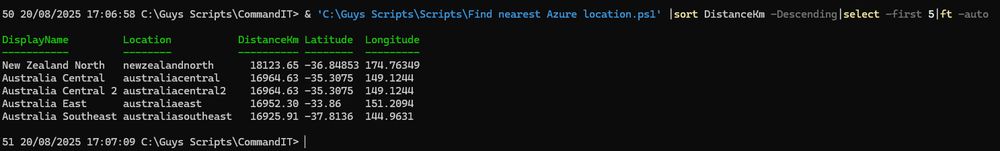
Guess which of these I ran from a Windows 365/Cloud PC instance? 😂
Will prompt for login if not connected which may need tenant or subscription parameters
github.com/guyrleech/Az...


Guess which of these I ran from a Windows 365/Cloud PC instance? 😂
Will prompt for login if not connected which may need tenant or subscription parameters
github.com/guyrleech/Az...
github.com/guyrleech/Mi...


github.com/guyrleech/Mi...

(Get-CimInstance -ClassName win32_userprofile -filter "sid = 'S-1-5-18'").LocalPath
Profiles for other special accounts also available that way


(Get-CimInstance -ClassName win32_userprofile -filter "sid = 'S-1-5-18'").LocalPath
Profiles for other special accounts also available that way



But I'm young yet so will probably grow out of it.
It adds a story to an otherwise boring and dull device

But I'm young yet so will probably grow out of it.
It adds a story to an otherwise boring and dull device



-Filter only takes 1 argument but -Include can be an array *.jpg,*.jpeg


-Filter only takes 1 argument but -Include can be an array *.jpg,*.jpeg





