
🔗My blog https://gelu.chat/
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
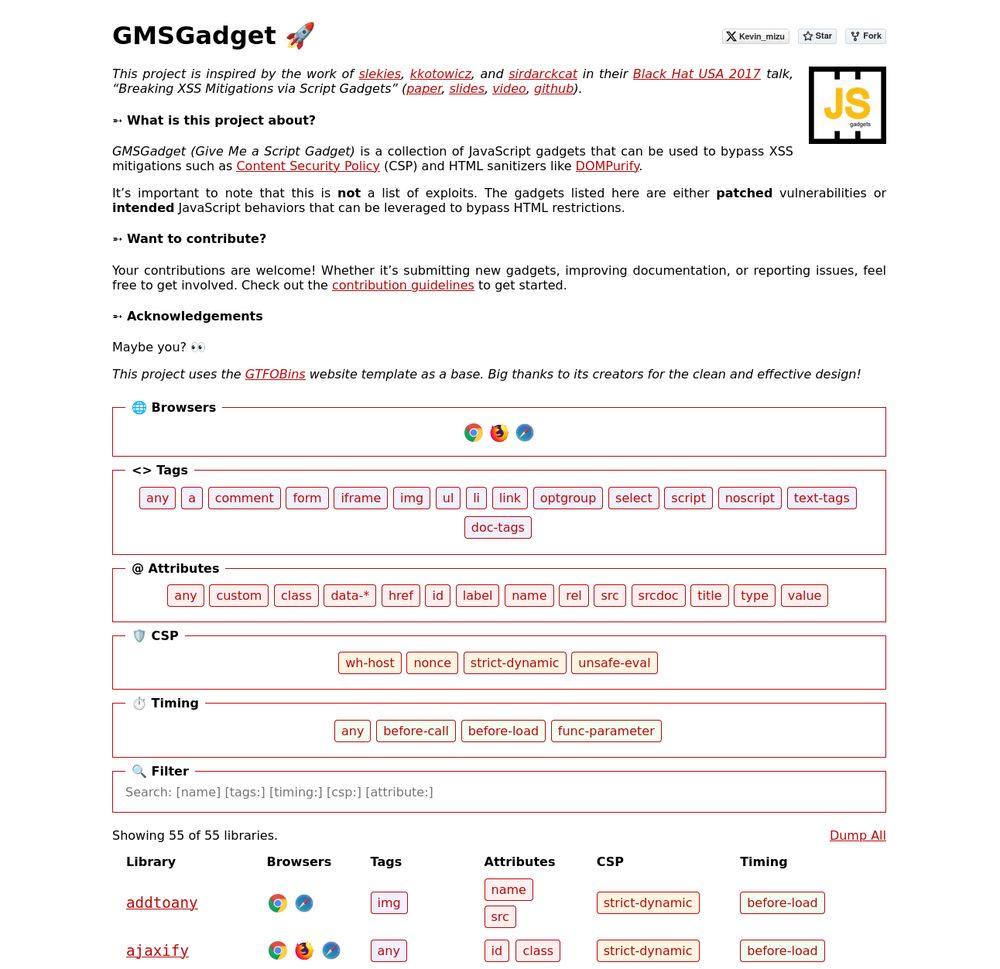
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4

If you have some time this weekend, give it a try! 👀
👉 pwnme.phreaks.fr

If you have some time this weekend, give it a try! 👀
👉 pwnme.phreaks.fr
x.com/icesfont2/st...

x.com/icesfont2/st...
bsky.app/profile/jori...
If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this!
jorianwoltjer.com/blog/p/hacki...
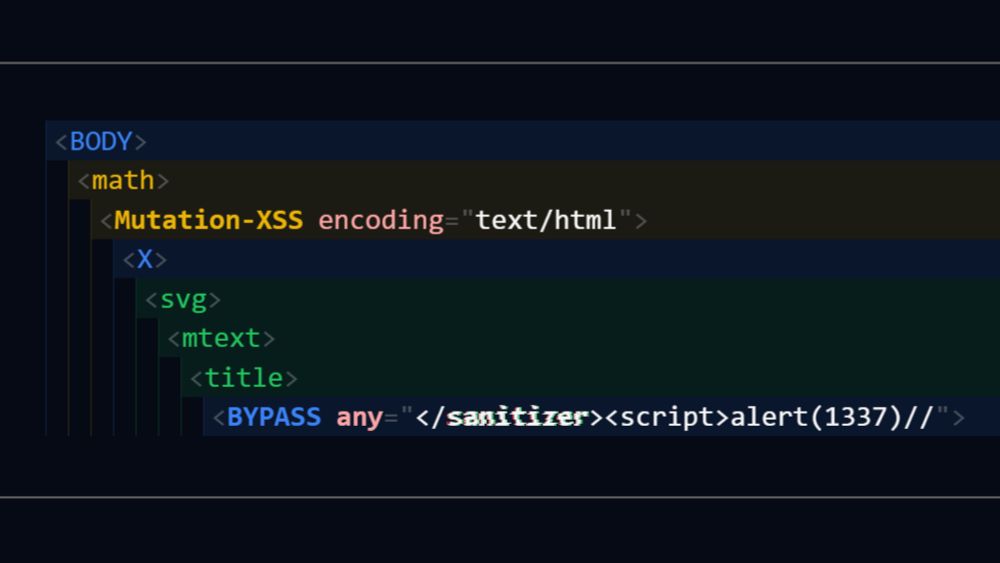
bsky.app/profile/jori...

Read how to send a cross-site POST without including a Content-Type header (without CORS). It even works with navigator.sendBeacon
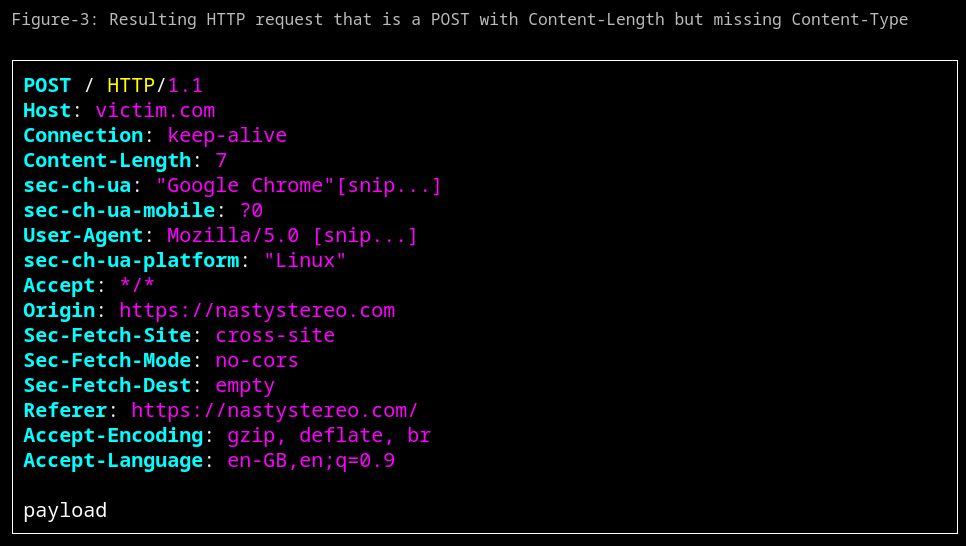
Read how to send a cross-site POST without including a Content-Type header (without CORS). It even works with navigator.sendBeacon

Order of operations bugs are one of my favorite types of bugs :) Write up and exploit script here: assetnote.io/resources/re...
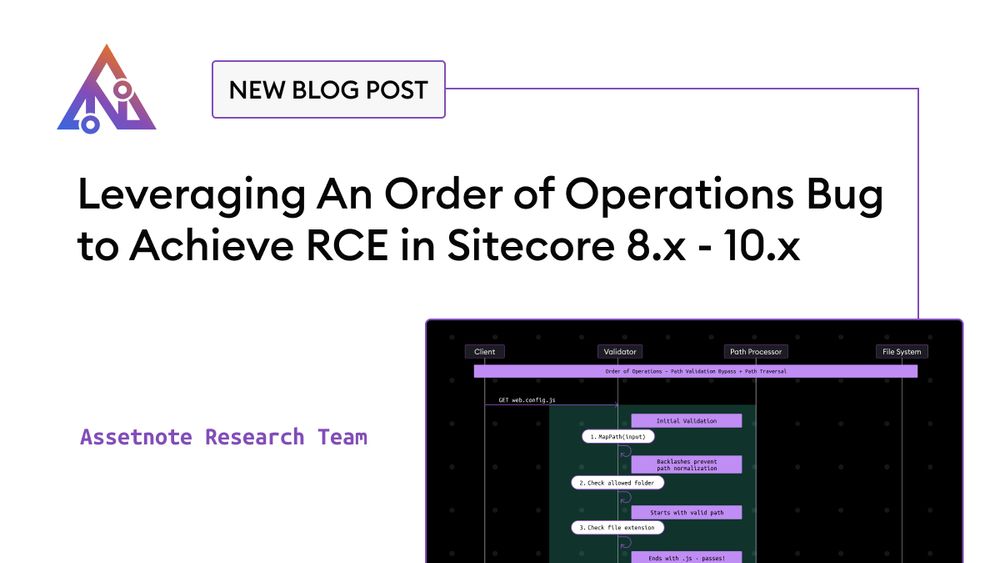
Order of operations bugs are one of my favorite types of bugs :) Write up and exploit script here: assetnote.io/resources/re...
www.youtube.com/watch?v=fnYS...

www.youtube.com/watch?v=fnYS...
https://portswigger.net/research/smashing-the-state-machine
https://portswigger.net/research/smashing-the-state-machine

