
We use math to ensure your code has no vulnerabilities
For Rust, Solidity, zk circuits. We use Rocq.
https://formal.land/
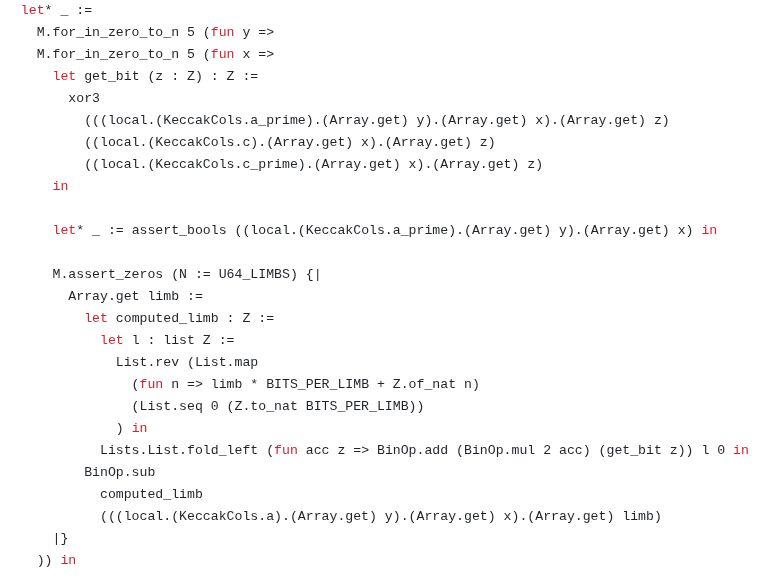
Frequent intermediate operations are showing that arrays hold boolean field elements, as well as manipulations of limbs of binary integers.
Frequent intermediate operations are showing that arrays hold boolean field elements, as well as manipulations of limbs of binary integers.
The main property we show is that the circuit is deterministic (no under-constraints).
The main property we show is that the circuit is deterministic (no under-constraints).
A few logical tricks are used in the definition of Keccak to replace some XOR operations by equivalent additions.

A few logical tricks are used in the definition of Keccak to replace some XOR operations by equivalent additions.
Our base definitions are in github.com/formal-land/...

Our base definitions are in github.com/formal-land/...
For arrays, we use the total function of their indices, returning a default value when out of bounds
For arrays, we use the total function of their indices, returning a default value when out of bounds
It will be simpler to reason about loops rather than a larger number of equations. In addition, the loops are rather simple here in terms of invariants.
It will be simpler to reason about loops rather than a larger number of equations. In addition, the loops are rather simple here in terms of invariants.
For now, we translate it by hand to the corresponding constraints in Rocq in the Garden project github.com/formal-land/...
We will ensure later with "coq-of-rust" that it corresponds to the original implementation.
For now, we translate it by hand to the corresponding constraints in Rocq in the Garden project github.com/formal-land/...
We will ensure later with "coq-of-rust" that it corresponds to the original implementation.
This amounts to encoding boolean operations like XOR or shift using equations over polynomials of integers modulo a prime number.
This amounts to encoding boolean operations like XOR or shift using equations over polynomials of integers modulo a prime number.
Happy to discuss the proof strategy/choices of representation!

Happy to discuss the proof strategy/choices of representation!

2. Show that this functional definition is equivalent to a semantics for the EVM in Rocq. There is at least one such project that we could show as equivalent to a reference implementation.
2. Show that this functional definition is equivalent to a semantics for the EVM in Rocq. There is at least one such project that we could show as equivalent to a reference implementation.
From there, we can go in two directions:
From there, we can go in two directions:
Otherwise, we pop one element from the stack and ask for a reference to the next one. If there are not enough elements, we return "StackUnderflow".
Otherwise, we pop one element from the stack and ask for a reference to the next one. If there are not enough elements, we return "StackUnderflow".
Output.Success tt
says that there can be no runtime failures (no panics!), assuming none of the provided methods panic. This is an important safety property.
The rest describes how the ADD instruction behaves.
Output.Success tt
says that there can be no runtime failures (no panics!), assuming none of the provided methods panic. This is an important safety property.
The rest describes how the ADD instruction behaves.
We need to specify them somehow to say they admit a functional specification.
We need to specify them somehow to say they admit a functional specification.

