Founder of WPScan (acquired by Automattic)
Check out my new project! https://kevintel.com
• CVE-2025-48827
• CVE-2025-48828
These vulnerabilities were detected being exploited in the wild by the KEVIntel sensors on May 26th.

• CVE-2025-48827
• CVE-2025-48828
These vulnerabilities were detected being exploited in the wild by the KEVIntel sensors on May 26th.
If you have a Pro API subscription, these all have the "wordpress" tag.
Also, have you noticed CISA's next incremental number? Who's betting they only add just one new KEV next time? 😅

If you have a Pro API subscription, these all have the "wordpress" tag.
Also, have you noticed CISA's next incremental number? Who's betting they only add just one new KEV next time? 😅

Two new KEVs this morning:
- CVE-2024-6047
- CVE-2024-11120
Both Unauthenticated OS Command Injection affecting GeoVision EOL devices.
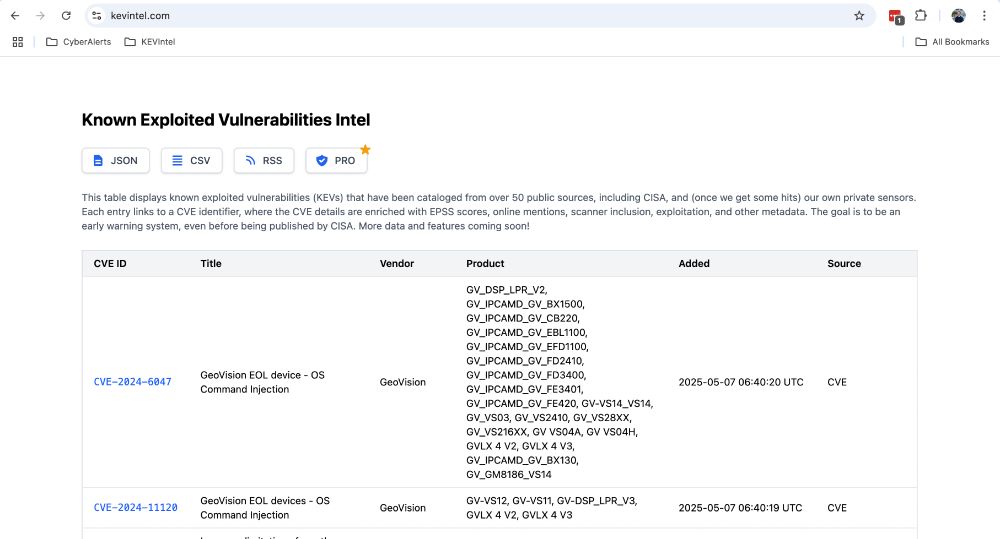
Two new KEVs this morning:
- CVE-2024-6047
- CVE-2024-11120
Both Unauthenticated OS Command Injection affecting GeoVision EOL devices.
What I would consider the most likely to be exploited (not including the prevalence of the product, which would make a big difference).
You should definitely patch these!
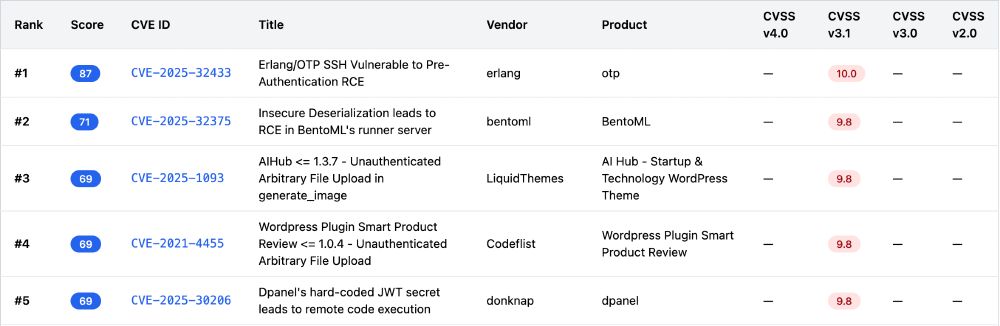
What I would consider the most likely to be exploited (not including the prevalence of the product, which would make a big difference).
You should definitely patch these!
- CVE-2024-38475 (Apache Software Foundation)
- CVE-2023-44221 (SonicWall)
kevintel.com
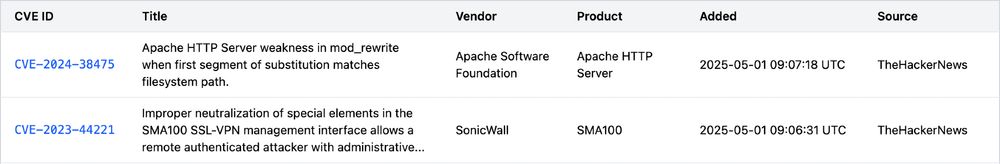
- CVE-2024-38475 (Apache Software Foundation)
- CVE-2023-44221 (SonicWall)
kevintel.com
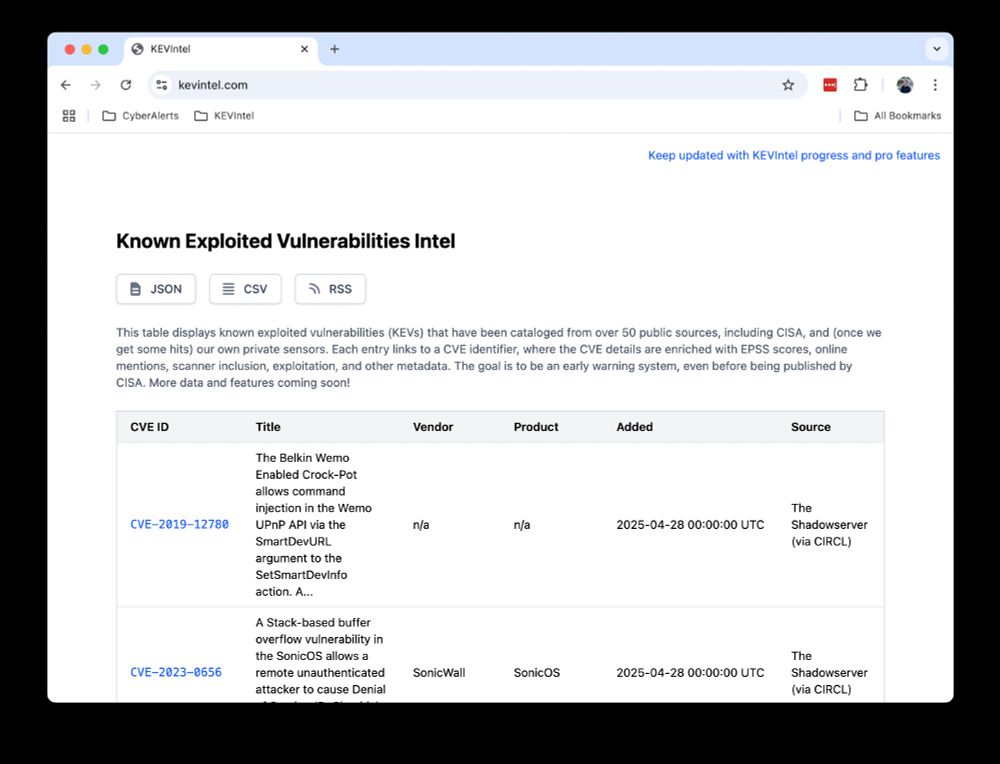



In this case, we alerted our users 14 hours before CISA KEV, to an actively exploited Apple iOS vulnerability.
We’ve also made changes so that this will be even earlier in the future!
cyberalerts.io/vulnerabilit...
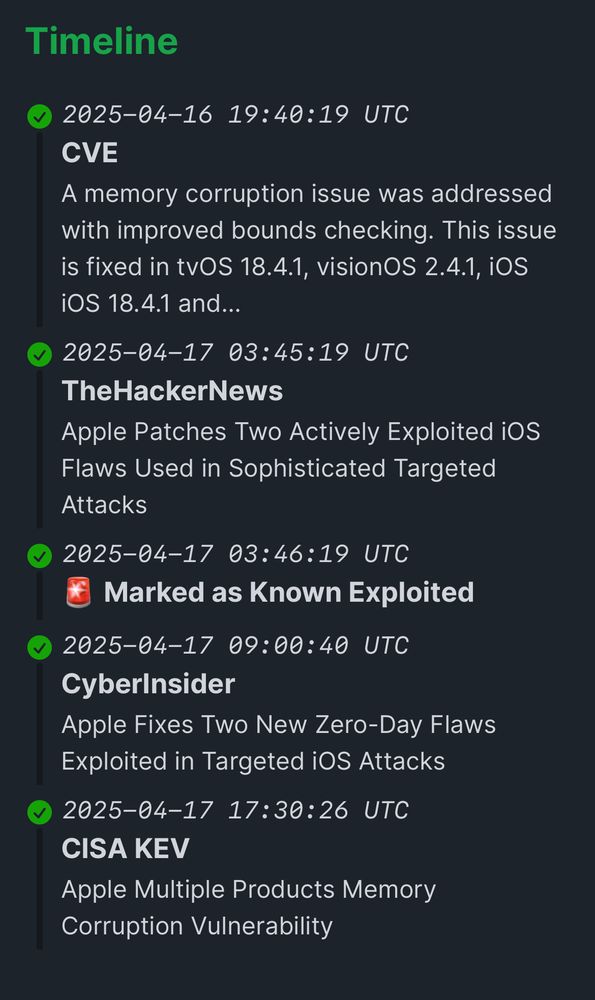
In this case, we alerted our users 14 hours before CISA KEV, to an actively exploited Apple iOS vulnerability.
We’ve also made changes so that this will be even earlier in the future!
cyberalerts.io/vulnerabilit...



The "worst of the worst" in terms of risk?
👉 cyberalerts.io/vulnerabilit...

The "worst of the worst" in terms of risk?
👉 cyberalerts.io/vulnerabilit...
🇨🇭 Switzerland - Brack.CH
User Dulnex claims to be selling the full database of brack.ch, one of the most well-known online stores in Switzerland.
The database allegedly contains phone number, email, firstname, lastname, invoice, item purchased, unpaid item, and more.

🇨🇭 Switzerland - Brack.CH
User Dulnex claims to be selling the full database of brack.ch, one of the most well-known online stores in Switzerland.
The database allegedly contains phone number, email, firstname, lastname, invoice, item purchased, unpaid item, and more.
Got to a Github repository, click:
Watch->Custom->Security Alerts->Apply

Got to a Github repository, click:
Watch->Custom->Security Alerts->Apply
This one is at the military museum in Menorca. And in immaculate condition.

This one is at the military museum in Menorca. And in immaculate condition.
I thought they were dead dead.

I thought they were dead dead.
• You can filter by "known exploited" in your dashboard.
• You can mark issues as "seen" and filter by them in your dashboard.
• Descriptions shown in dashboard.
• We now include images of the sources in your personalised dashboard.

• You can filter by "known exploited" in your dashboard.
• You can mark issues as "seen" and filter by them in your dashboard.
• Descriptions shown in dashboard.
• We now include images of the sources in your personalised dashboard.

From his consultancy, HispaSec, to VirusTotal’s acquisition by Google, it’s full of business insights and hacking lore.

From his consultancy, HispaSec, to VirusTotal’s acquisition by Google, it’s full of business insights and hacking lore.
tools.enisa.europa.eu/topics/incid...

tools.enisa.europa.eu/topics/incid...

