
🎥Presentation: youtu.be/_ODdwpxXRR4?...
#Security #Pentest #WindowsInternals

🎥Presentation: youtu.be/_ODdwpxXRR4?...
#Security #Pentest #WindowsInternals
See changelog: emanuelduss.ch/posts/create...
#pentest #network #tls #mitm

See changelog: emanuelduss.ch/posts/create...
#pentest #network #tls #mitm
Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Curious how web filters are evaded? Read his blog series: blog.compass-security.com/2025/03/bypa...
#cve #pentest #bypass
Curious how web filters are evaded? Read his blog series: blog.compass-security.com/2025/03/bypa...
#cve #pentest #bypass
www.youtube.com/playlist?lis...

www.youtube.com/playlist?lis...

RBCD opens new attack paths in Kerberos. Learn how misconfigs enable privilege escalation and how to defend.
youtu.be/l97RDnzdrXY?...
#Kerberos #ActiveDirectory

RBCD opens new attack paths in Kerberos. Learn how misconfigs enable privilege escalation and how to defend.
youtu.be/l97RDnzdrXY?...
#Kerberos #ActiveDirectory
youtu.be/rnhr02eKU0I?...
#Kerberos #ActiveDirectory

youtu.be/rnhr02eKU0I?...
#Kerberos #ActiveDirectory

youtu.be/56BjmyOTN5o?...
#Kerberos #ActiveDirectory

youtu.be/56BjmyOTN5o?...
#Kerberos #ActiveDirectory
Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting

Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting
Kerberoasting lets attackers steal AD service account credentials. See how it works and how to protect your systems: youtu.be/PhNspeJ0r-4?...
#Kerberos #ActiveDirectory

Kerberoasting lets attackers steal AD service account credentials. See how it works and how to protect your systems: youtu.be/PhNspeJ0r-4?...
#Kerberos #ActiveDirectory

Starts today → blog.compass-security.com/2025/09/tami... → Subscribe to our channel!
#Kerberos #ActiveDirectory

Starts today → blog.compass-security.com/2025/09/tami... → Subscribe to our channel!
#Kerberos #ActiveDirectory
In our latest blog, we go hands-on: real-life setups, plus tips for recovery and avoiding pitfalls.
blog.compass-security.com/2025/08/into...
#Passkeys #CyberSecurity #Authentication

In our latest blog, we go hands-on: real-life setups, plus tips for recovery and avoiding pitfalls.
blog.compass-security.com/2025/08/into...
#Passkeys #CyberSecurity #Authentication
Updates include:
✅ Golden dMSA Attack
✅ Full LAPS support
✅ Trust password & BitLocker recovery key extraction
✅ Read-only domain controller database compatibility
Read more from Michael Grafnetter: ghst.ly/412rZ7F

Updates include:
✅ Golden dMSA Attack
✅ Full LAPS support
✅ Trust password & BitLocker recovery key extraction
✅ Read-only domain controller database compatibility
Read more from Michael Grafnetter: ghst.ly/412rZ7F
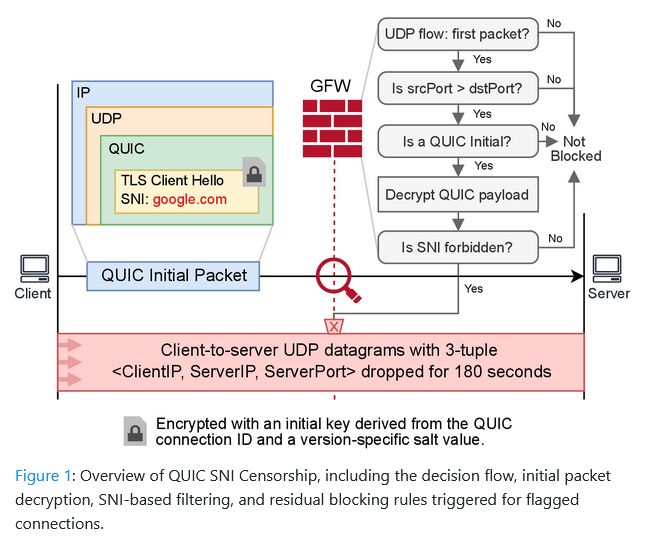
The filtering started in April last year.
The Great Firewall now decrypts QUIC packets at scale and uses a separate blocklist for QUIC traffic, separate from its main filters
gfw.report/publications...
The filtering started in April last year.
The Great Firewall now decrypts QUIC packets at scale and uses a separate blocklist for QUIC traffic, separate from its main filters
gfw.report/publications...
sensepost.com/blog/2025/a-...
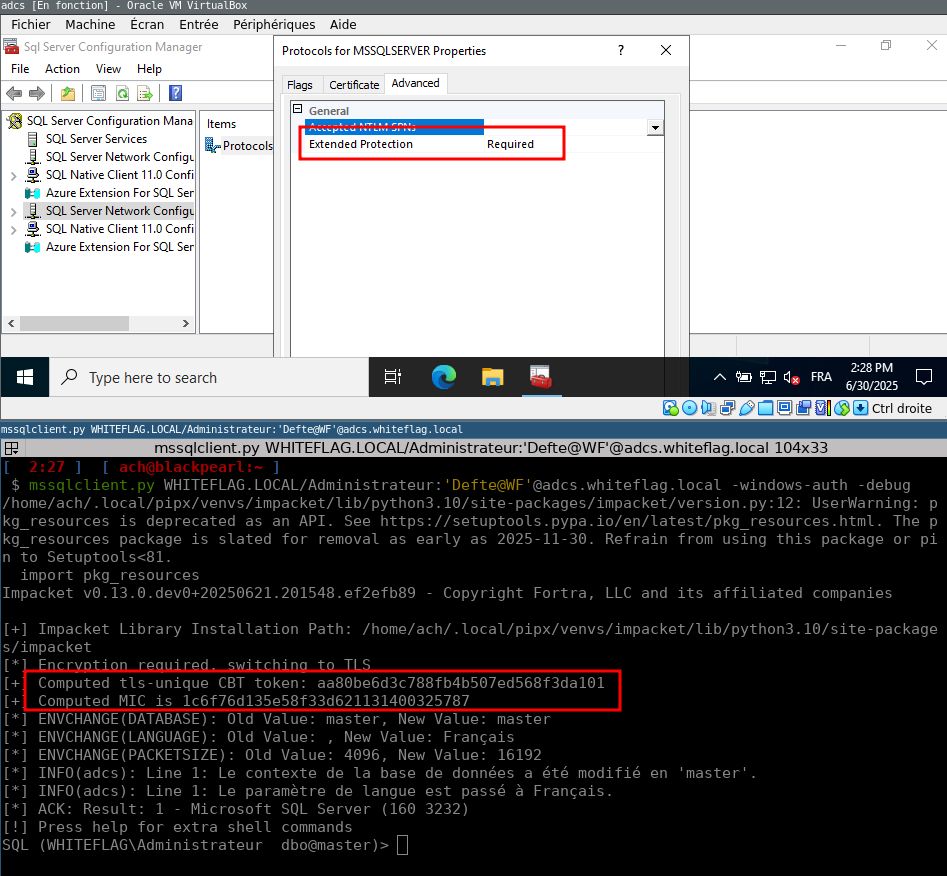
sensepost.com/blog/2025/a-...
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
- Watch the livestream from #DEFCON at 16:30 PT on the 8th
- Read the whitepaper on our website
- Grab the HTTP Request Smuggler update & WebSecAcademy lab
Follow for updates & links. It's nearly time!

- Watch the livestream from #DEFCON at 16:30 PT on the 8th
- Read the whitepaper on our website
- Grab the HTTP Request Smuggler update & WebSecAcademy lab
Follow for updates & links. It's nearly time!
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9

@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9

