
Read and subscribe to October’s edition of the DomainTools Investigations Newsletter here: https://www.linkedin.com/newsletters/dt-investigations-news-7289801727560630273/

Read and subscribe to October’s edition of the DomainTools Investigations Newsletter here: https://www.linkedin.com/newsletters/dt-investigations-news-7289801727560630273/


bsidesnova-2025.sessionize.com/session/1001...

bsidesnova-2025.sessionize.com/session/1001...

#Cybersecurity #ThreatIntelligence #Splunk #Phishing

#Cybersecurity #ThreatIntelligence #Splunk #Phishing
https://bit.ly/46w63on
#ThreatIntel #PoisonSeed #SCATTEREDSPIDER
https://bit.ly/46w63on
#ThreatIntel #PoisonSeed #SCATTEREDSPIDER
![Screenshot of a spreadsheet with columns labeled 'time 1', 'timestamp 1', 'domain 1', and 'appx_domain 1'. Each column lists various entries including times, dates, and website URLs such as ups[.]com, chick-fil-a[.]com, and best-rate[.]site.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:jk5cjbjmnbl2dnx24zurqn23/bafkreielu7ausbrsjavfi2efxnay6p5tfsfezzmgegw3zb3xf6senhuhgq@jpeg)
![Diagram showing web domains and their connections: koala-app[.]com linked to mofa.go[.]kr, webcloud-notice.com linked to spo.go[.]kr, nid-security[.]com linked to dcc.mil[.]kr, and jeder97271@wuzak[.]com linked to wuzak[.]com.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:jk5cjbjmnbl2dnx24zurqn23/bafkreib6erzsk5chlxvzdznqqobmox6f7esho3zbwn5oxojgj6knse6voy@jpeg)
Learn more: https://thecyberwire.com/podcasts/research-saturday/390/notes

Learn more: https://thecyberwire.com/podcasts/research-saturday/390/notes
https://dti.domaintools.com/spynote-malware-part-2/

https://dti.domaintools.com/spynote-malware-part-2/
https://dti.domaintools.com/spynote-malware-part-2/

https://dti.domaintools.com/spynote-malware-part-2/
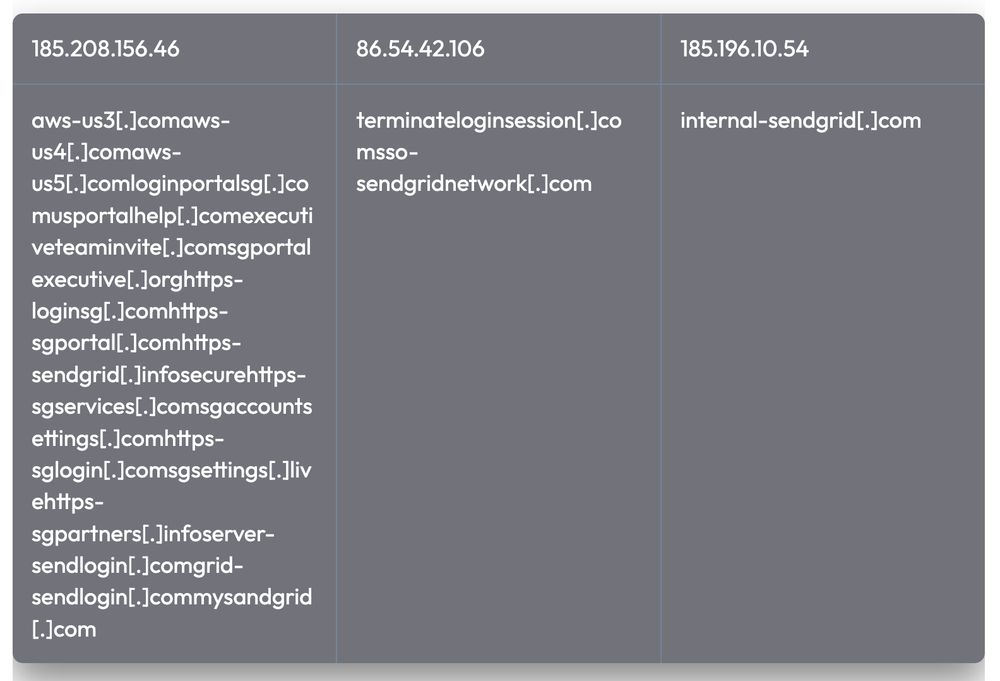
Read the full report: https://dti.domaintools.com/hunting-for-malware-networks/
#Cybersecurity #ThreatIntel #Malware #BlueTeam

Read the full report: https://dti.domaintools.com/hunting-for-malware-networks/
#Cybersecurity #ThreatIntel #Malware #BlueTeam

