
Schedule www.zerodayinitiative.com/blog/2025/20...

Schedule www.zerodayinitiative.com/blog/2025/20...
RBCD opens new attack paths in Kerberos. Learn how misconfigs enable privilege escalation and how to defend.
youtu.be/l97RDnzdrXY?...
#Kerberos #ActiveDirectory

RBCD opens new attack paths in Kerberos. Learn how misconfigs enable privilege escalation and how to defend.
youtu.be/l97RDnzdrXY?...
#Kerberos #ActiveDirectory
youtu.be/rnhr02eKU0I?...
#Kerberos #ActiveDirectory

youtu.be/rnhr02eKU0I?...
#Kerberos #ActiveDirectory
youtu.be/_6FYZRTJQ-s?...
#Kerberos #ActiveDirectory

youtu.be/_6FYZRTJQ-s?...
#Kerberos #ActiveDirectory
youtu.be/56BjmyOTN5o?...
#Kerberos #ActiveDirectory

youtu.be/56BjmyOTN5o?...
#Kerberos #ActiveDirectory
Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting

Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting
Kerberoasting lets attackers steal AD service account credentials. See how it works and how to protect your systems: youtu.be/PhNspeJ0r-4?...
#Kerberos #ActiveDirectory

Kerberoasting lets attackers steal AD service account credentials. See how it works and how to protect your systems: youtu.be/PhNspeJ0r-4?...
#Kerberos #ActiveDirectory
Starts today → blog.compass-security.com/2025/09/tami... → Subscribe to our channel!
#Kerberos #ActiveDirectory

Starts today → blog.compass-security.com/2025/09/tami... → Subscribe to our channel!
#Kerberos #ActiveDirectory

In our latest blog, we go hands-on: real-life setups, plus tips for recovery and avoiding pitfalls.
blog.compass-security.com/2025/08/into...
#Passkeys #CyberSecurity #Authentication

In our latest blog, we go hands-on: real-life setups, plus tips for recovery and avoiding pitfalls.
blog.compass-security.com/2025/08/into...
#Passkeys #CyberSecurity #Authentication
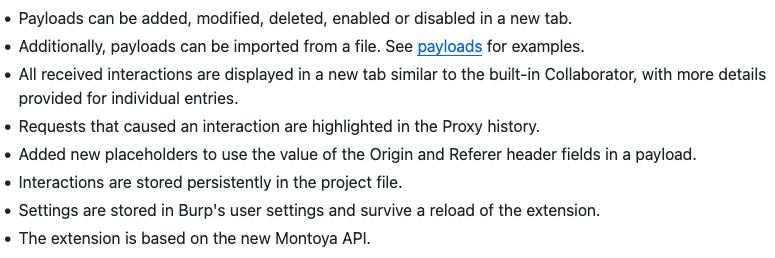
blog.compass-security.com/2025/07/xvul...

blog.compass-security.com/2025/07/xvul...

But persistence paid off. Our detailed blog post is now live: blog.compass-security.com/2025/06/pwn2...
#penetrationtest #pentest #iot #embedded #cybersecurity
www.compass-security.com/en/services/...

But persistence paid off. Our detailed blog post is now live: blog.compass-security.com/2025/06/pwn2...
#penetrationtest #pentest #iot #embedded #cybersecurity
www.compass-security.com/en/services/...
Talk: troopers.de/troopers25/t...
Compass pentest: www.compass-security.com/en/services/... #cybersecurity #iot #hw #fw #ot

Talk: troopers.de/troopers25/t...
Compass pentest: www.compass-security.com/en/services/... #cybersecurity #iot #hw #fw #ot

blog.compass-security.com/2025/05/reno...

blog.compass-security.com/2025/05/reno...
#EntraID #IAM

#EntraID #IAM
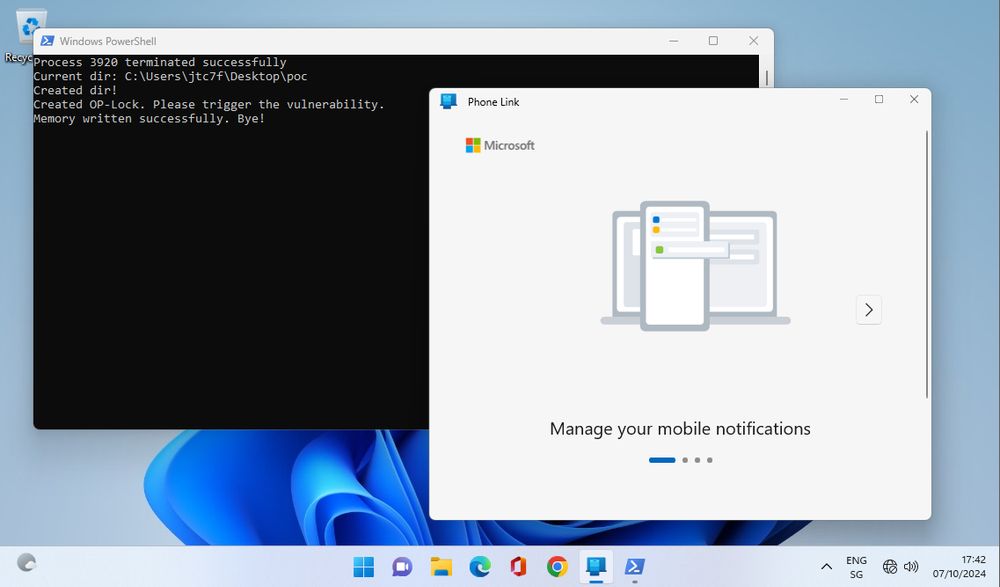

In part 4 of his blog series, @emanuelduss.ch shows how detection mechanisms of web filters can be bypassed: blog.compass-security.com/2025/03/bypa...
#pentest #network
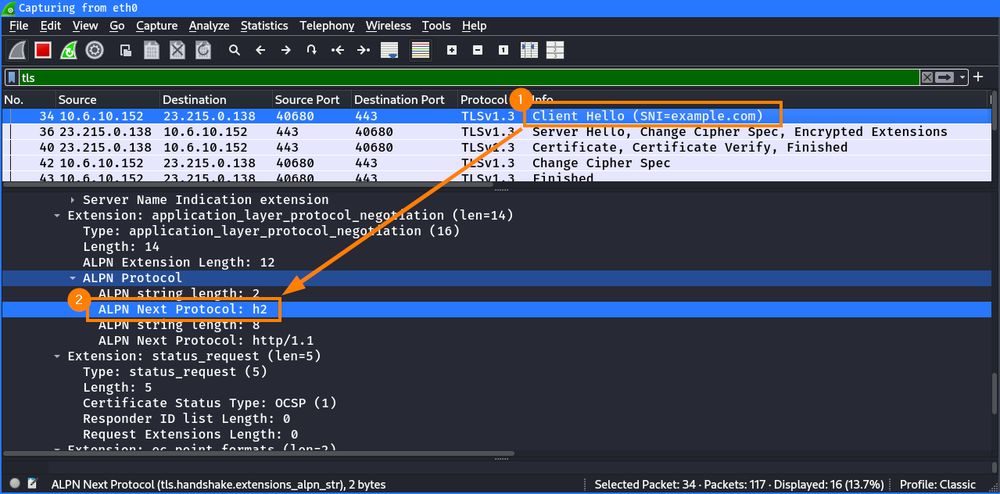
In part 4 of his blog series, @emanuelduss.ch shows how detection mechanisms of web filters can be bypassed: blog.compass-security.com/2025/03/bypa...
#pentest #network


