
The “AppSuite PDF Editor” poses as a legit tool but is a backdoor: most of its code supports malware functions, including C2 comms, scheduled tasks, and AES-encrypted data exfiltration.
Persistence is full, cleanup needs system repave.
#ransomNews

The “AppSuite PDF Editor” poses as a legit tool but is a backdoor: most of its code supports malware functions, including C2 comms, scheduled tasks, and AES-encrypted data exfiltration.
Persistence is full, cleanup needs system repave.
#ransomNews

Substack: techletters.substack.com/p/techletter...

Substack: techletters.substack.com/p/techletter...





CVE-2025-6543, a memory overflow, has been exploited as a zero-day since May 2025.
Multiple vital organizations were breached, with attackers deploying stealthy web shells and erasing forensic traces. Patch immediately.
#ransomNews

CVE-2025-6543, a memory overflow, has been exploited as a zero-day since May 2025.
Multiple vital organizations were breached, with attackers deploying stealthy web shells and erasing forensic traces. Patch immediately.
#ransomNews










Open Directory Search Engine. Search audio, video, archives, documents, mobile apps and other files.
Browse list of IPs/domains with open directories.
filepursuit.com
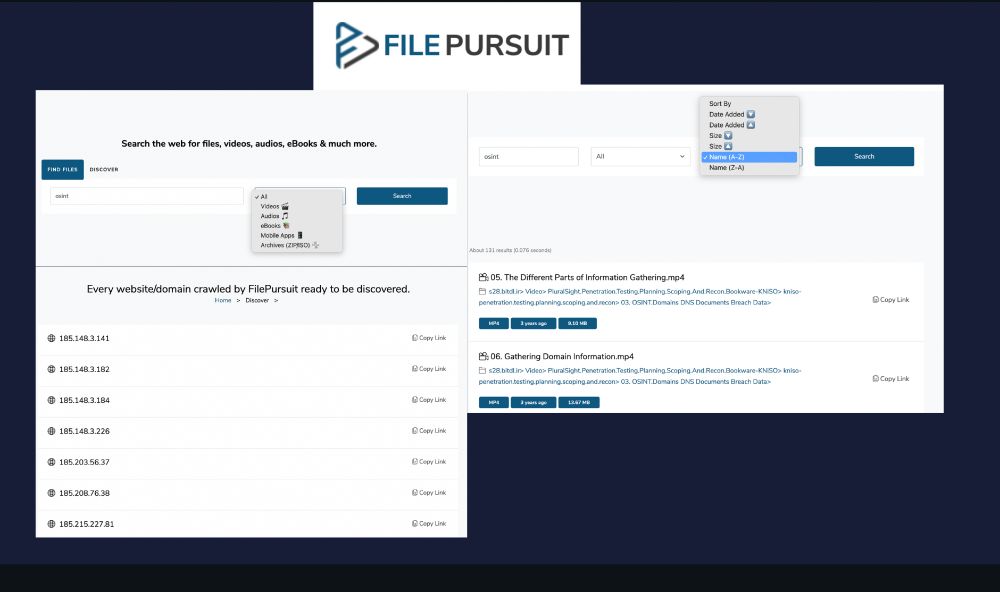
Open Directory Search Engine. Search audio, video, archives, documents, mobile apps and other files.
Browse list of IPs/domains with open directories.
filepursuit.com




