
I SO look forward to it and to meeting the participants!! 🤩👩🏻💻
Full class content & details: www.brucon.org/training-det...

I SO look forward to it and to meeting the participants!! 🤩👩🏻💻
Full class content & details: www.brucon.org/training-det...
It started with 2 days full of #socialengineering & #OSINT training where I had the privilege to teach a class that was present, curious, and ready to try things out.
Big bonus: reconnecting with friends during the conference days afterwards😊


It started with 2 days full of #socialengineering & #OSINT training where I had the privilege to teach a class that was present, curious, and ready to try things out.
Big bonus: reconnecting with friends during the conference days afterwards😊
This is an intensive, 2-day training 🧵

This is an intensive, 2-day training 🧵
The Dark Overlord investigation is an interesting report showcasing how HUMINT helps better understand threat actor activities, and even infiltrate their inner circles to uncover real identities.
Some notes 🧵
nightlion.com/wp-content/u...

The Dark Overlord investigation is an interesting report showcasing how HUMINT helps better understand threat actor activities, and even infiltrate their inner circles to uncover real identities.
Some notes 🧵
nightlion.com/wp-content/u...
Samuel will discuss the types of criminal activity that leverage Telegram, as well as important investigative tools & techniques to help you maximize your information collection from the platform while maintaining appropriate OPSEC.

Samuel will discuss the types of criminal activity that leverage Telegram, as well as important investigative tools & techniques to help you maximize your information collection from the platform while maintaining appropriate OPSEC.
Elicitation is about making people volunteer information without asking a single question.
It is part of most social engineering attempts that involve information collection, and an integral part of HUMINT operations (including threat intelligence vHUMINT).

Elicitation is about making people volunteer information without asking a single question.
It is part of most social engineering attempts that involve information collection, and an integral part of HUMINT operations (including threat intelligence vHUMINT).
Spent the week giving our 2-day training to a largely diverse class, strolling around London, celebrating a birthday (thanks to @osintgeek.de who is the best work buddy you can have), and attending the conference!
You can say it was a real FULL week.



Spent the week giving our 2-day training to a largely diverse class, strolling around London, celebrating a birthday (thanks to @osintgeek.de who is the best work buddy you can have), and attending the conference!
You can say it was a real FULL week.
It was the first time I delivered a deep-dive focusing entirely on the #psychology interplaying in social engineering & HUMINT operations at a cybersecurity conference.
It is very energizing to have a class full of curious minds!

It was the first time I delivered a deep-dive focusing entirely on the #psychology interplaying in social engineering & HUMINT operations at a cybersecurity conference.
It is very energizing to have a class full of curious minds!
“Look What You Made Me Do”: The Psychology behind Social Engineering & Human Intelligence Operations
- taking place at DeepSec in Vienna on the 19th & 20th of November!
deepsec.net/speaker.html...


“Look What You Made Me Do”: The Psychology behind Social Engineering & Human Intelligence Operations
- taking place at DeepSec in Vienna on the 19th & 20th of November!
deepsec.net/speaker.html...

The talented @OSINTgeek & I will be teaching our "Fundamentals of Cyber Investigations & Human Intelligence" class on the 9-10th of December in London!

The talented @OSINTgeek & I will be teaching our "Fundamentals of Cyber Investigations & Human Intelligence" class on the 9-10th of December in London!
Summer is here and it's my time to tackle a long reading list:)

Summer is here and it's my time to tackle a long reading list:)
❗️Disclaimer: This is an edited version:some slides/details have been omitted.
www.wins.org/wp-content/u...

❗️Disclaimer: This is an edited version:some slides/details have been omitted.
www.wins.org/wp-content/u...
Thank you for inviting me,I had a great time learning from others & meeting everyone!




(🧵)


(🧵)
However... this time, in addition to the updates we have made, there will also be a little surprise, something we have never done before 🤭🤫

However... this time, in addition to the updates we have made, there will also be a little surprise, something we have never done before 🤭🤫
We get to the core of how social engineering works (and how to thwart this threat) by getting to the core of human psychology and behavior.


We get to the core of how social engineering works (and how to thwart this threat) by getting to the core of human psychology and behavior.
Last week I had the pleasure of participating at the Swiss Cyber Storm as a speaker.
It was one of THE most mentally stimulating conferences I have been to, a top shelf kind of conference for cybersecurity.

Last week I had the pleasure of participating at the Swiss Cyber Storm as a speaker.
It was one of THE most mentally stimulating conferences I have been to, a top shelf kind of conference for cybersecurity.
In 2 weeks we will be meeting at DeepSec in Vienna for a deep dive training on #SocialEngineering & #OSINT!
Join the 2-day training "Practical Social Engineering & Open-source Intelligence"
⬇️ Details & Registration: ow.ly/oGRH50PEZoE

In 2 weeks we will be meeting at DeepSec in Vienna for a deep dive training on #SocialEngineering & #OSINT!
Join the 2-day training "Practical Social Engineering & Open-source Intelligence"
⬇️ Details & Registration: ow.ly/oGRH50PEZoE
We need an investigative methodology that supports all the capabilities of today's world in an organized & reproducible manner; the tools,the analytical thinking, the investigative process
Accurate quote:

We need an investigative methodology that supports all the capabilities of today's world in an organized & reproducible manner; the tools,the analytical thinking, the investigative process
Accurate quote:
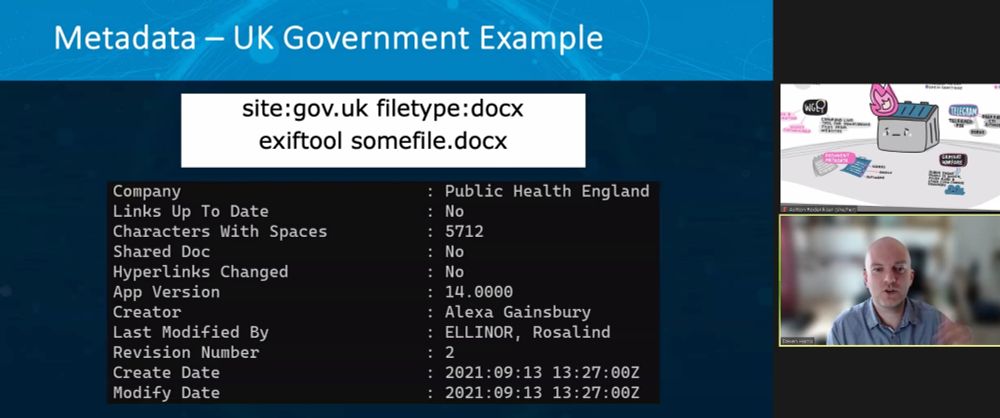



@nixintel.bsky.social wrote a blog post on how to create one:
www.osintcurio.us/2022/09/12/f...

@nixintel.bsky.social wrote a blog post on how to create one:
www.osintcurio.us/2022/09/12/f...

