
It's a form of browser hijacker that remotely controls your browser based on server commands.
Typical form: press key combos for copy-pasting URLs, opening tabs, context menu, downloading files etc


It's a form of browser hijacker that remotely controls your browser based on server commands.
Typical form: press key combos for copy-pasting URLs, opening tabs, context menu, downloading files etc
cyberint.com/blog/threat-...

cyberint.com/blog/threat-...
More info on this activity at github.com/PaloAltoNetw...
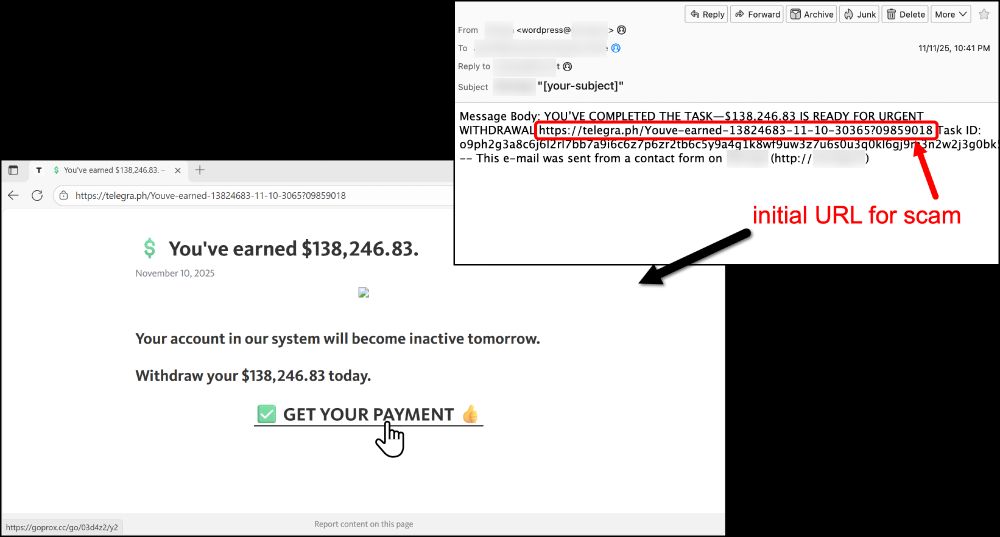



More info on this activity at github.com/PaloAltoNetw...

#GreyNoise #AI #AISecurity #MCP #MCPSecurity #Cybersecurity #ThreatIntel

#GreyNoise #AI #AISecurity #MCP #MCPSecurity #Cybersecurity #ThreatIntel

We use this tool internally to help track multiple threat actors with high confidence.
Mark Overholser from Corelight joins us to pull back the curtain on how the Black Hat Network Operations Center (NOC) is built, monitored, and the craziest things that have shown up!
Spotify: open.spotify.com/episode/2F4x...

Mark Overholser from Corelight joins us to pull back the curtain on how the Black Hat Network Operations Center (NOC) is built, monitored, and the craziest things that have shown up!
Spotify: open.spotify.com/episode/2F4x...
Read more on the Fortra blog: www.fortra.com/blog/cybercr...

Read more on the Fortra blog: www.fortra.com/blog/cybercr...
Our blog shows they’re increasingly weaponizing #OAuth applications to maintain persistent access in the cloud—even after #passwords are reset or #MFA is enforced.
This persistence poses a growing risk to modern enterprises.
Our blog shows they’re increasingly weaponizing #OAuth applications to maintain persistent access in the cloud—even after #passwords are reset or #MFA is enforced.
This persistence poses a growing risk to modern enterprises.
@sam-hans0n.bsky.social and I share stories of malware we discovered while searching for ICS threats, and discuss our approach to assessing their reputation.
Don't Cry Wolf: Evidence-Based Assessment of ICS Threats

@sam-hans0n.bsky.social and I share stories of malware we discovered while searching for ICS threats, and discuss our approach to assessing their reputation.
Don't Cry Wolf: Evidence-Based Assessment of ICS Threats

(and fits well on my UW monitor)

(and fits well on my UW monitor)
www.huntress.com/blog/nezha-c...

Join us on YouTube - youtube.com/live/ID9q7E4...

Join us on YouTube - youtube.com/live/ID9q7E4...
This is from a file disguised as a cracked version of software, and I usually see #LummaStealer from this.




This is from a file disguised as a cracked version of software, and I usually see #LummaStealer from this.
🎧 open.spotify.com/episode/2CFB...

🎧 open.spotify.com/episode/2CFB...




open.spotify.com/episode/4eS4...

open.spotify.com/episode/4eS4...
🎯 youtube.com/shorts/eddBB...

🎯 youtube.com/shorts/eddBB...
Staff Security Research Engineer:
proofpoint.wd5.myworkdayjobs.com/en-US/Proofp...
Senior Threat Researcher (ecrime team):
proofpoint.wd5.myworkdayjobs.com/ProofpointCa...

Staff Security Research Engineer:
proofpoint.wd5.myworkdayjobs.com/en-US/Proofp...
Senior Threat Researcher (ecrime team):
proofpoint.wd5.myworkdayjobs.com/ProofpointCa...


