@kqlcafe.bsky.social . I will discuss #KQL, Logic Apps and hunting through the available APIs.
The session is on April 29th and is completely free to attend online.
🗓️Event registration & details: www.meetup.com/kql-cafe/
@kqlcafe.bsky.social . I will discuss #KQL, Logic Apps and hunting through the available APIs.
The session is on April 29th and is completely free to attend online.
🗓️Event registration & details: www.meetup.com/kql-cafe/
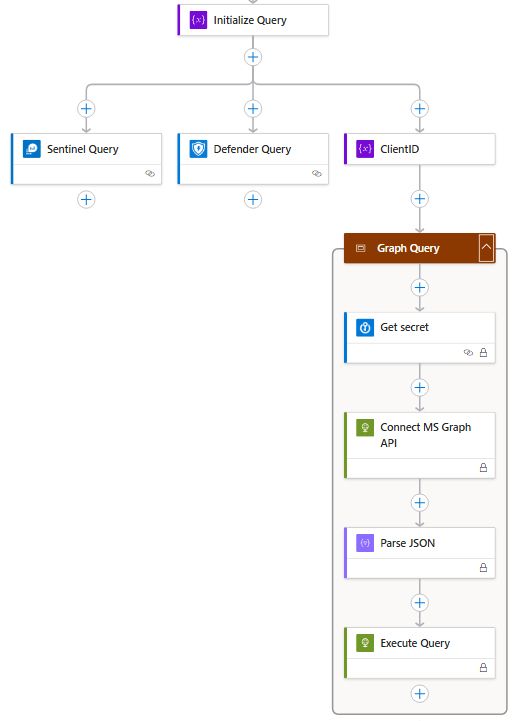
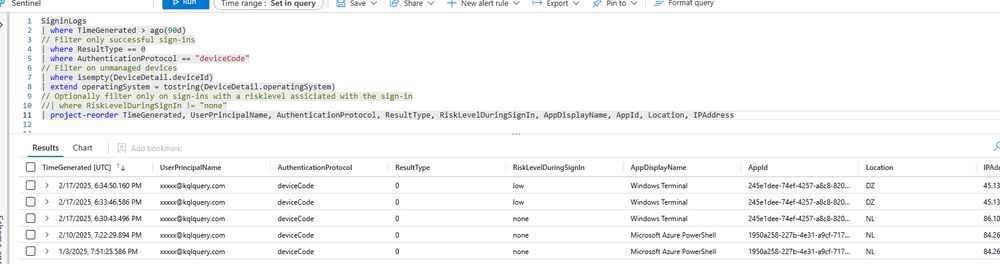
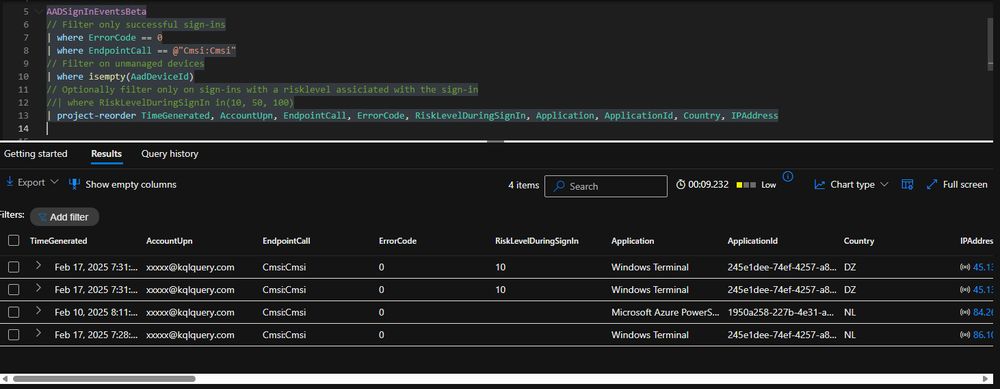
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
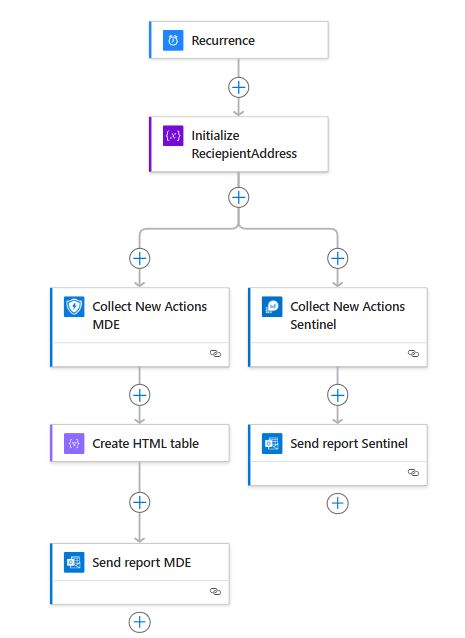
I will probably write a small blog about the topic soon.
Deployment: github.com/Bert-JanP/Se...
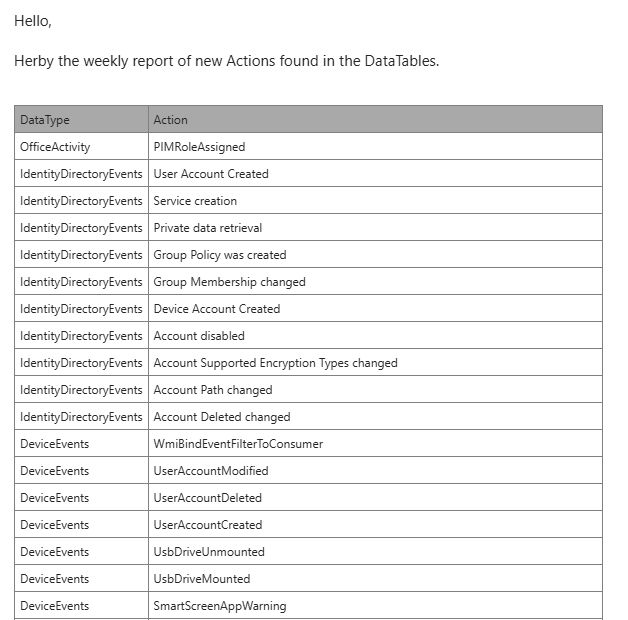
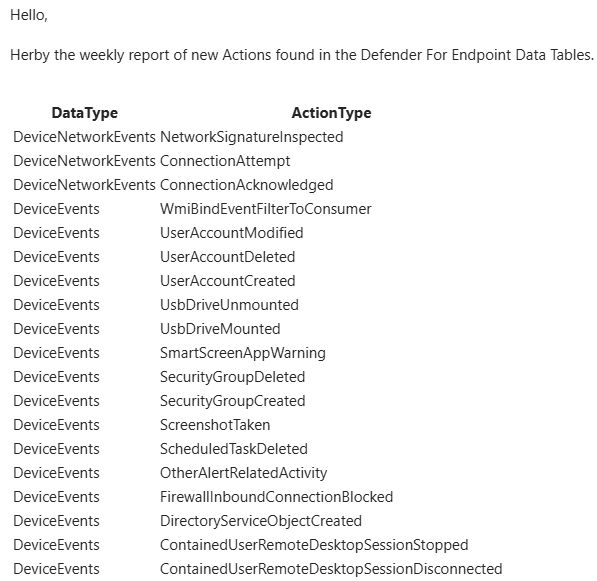
I will probably write a small blog about the topic soon.
Deployment: github.com/Bert-JanP/Se...
Az.SecurityInsights.internal\New-AzSentinelAlertRule : The maximum number of enabled Scheduled analytics rules (512)
learn.microsoft.com/en-us/azure/...
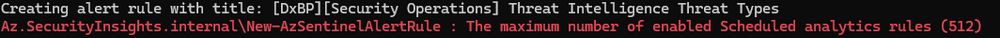
Az.SecurityInsights.internal\New-AzSentinelAlertRule : The maximum number of enabled Scheduled analytics rules (512)
learn.microsoft.com/en-us/azure/...
Source: techcommunity.microsoft.com/blog/microso...
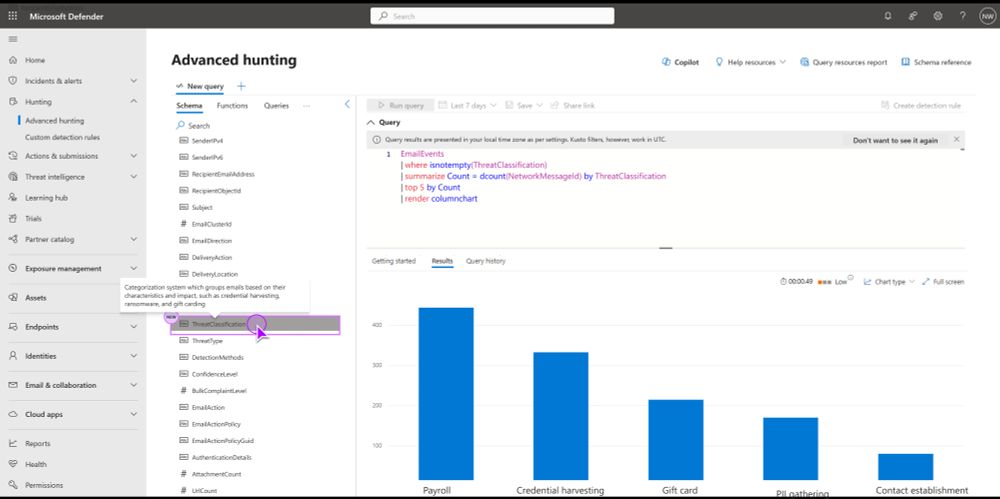
Source: techcommunity.microsoft.com/blog/microso...


