
It's ProxyBlob, a reverse proxy over Azure.
Check out Alexandre Nesic's article on how it came to exist after an assumed breach mission ⤵️
👉 blog.quarkslab.com/proxyblobing...

It's ProxyBlob, a reverse proxy over Azure.
Check out Alexandre Nesic's article on how it came to exist after an assumed breach mission ⤵️
👉 blog.quarkslab.com/proxyblobing...

It's ProxyBlob, a reverse proxy over Azure.
Check out Alexandre Nesic's article on how it came to exist after an assumed breach mission ⤵️
👉 blog.quarkslab.com/proxyblobing...
MacroPack, ShellcodePack, and DarwinOps all come with bypass presets for major EDRs and Antivirus
Those presets are regularly updated and tested!
If you want to see a demo or an equivalent screenshot for the major EDRs contact us !
#redteam

MacroPack, ShellcodePack, and DarwinOps all come with bypass presets for major EDRs and Antivirus
Those presets are regularly updated and tested!
If you want to see a demo or an equivalent screenshot for the major EDRs contact us !
#redteam
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Join him next Monday at Campus Cyber Hauts-the-France:
www.meetup.com/hack-the-box...
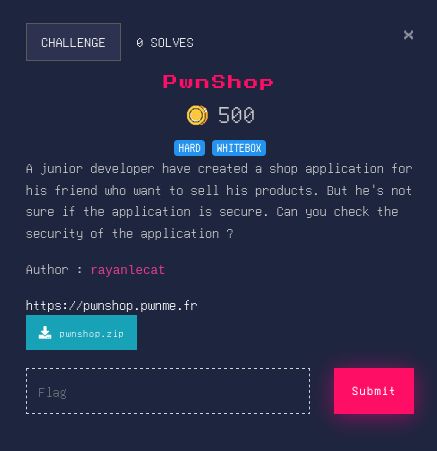
Join him next Monday at Campus Cyber Hauts-the-France:
www.meetup.com/hack-the-box...
To help with static analysis detection by EDR,
ShellcodePack implements a method to load a shellcode from a separate file or from an URL
This tutorial explains how to use that option!
#redteam
blog.balliskit.com/loading-a-sh...

To help with static analysis detection by EDR,
ShellcodePack implements a method to load a shellcode from a separate file or from an URL
This tutorial explains how to use that option!
#redteam
blog.balliskit.com/loading-a-sh...
This is it! After over two years of development, countless delays, and hundreds of manual company verifications, Evilginx Pro is finally live!
Thank you all for your invaluable support 💗
breakdev.org/evilginx-pro...

This is it! After over two years of development, countless delays, and hundreds of manual company verifications, Evilginx Pro is finally live!
Thank you all for your invaluable support 💗
breakdev.org/evilginx-pro...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
My latest post highlights the advanced tactics used to bypass security controls and deceive even the most savvy users. Check it out ⤵️
Learn some infrastructure tricks and delivery methods to bypass common detection.
👉 blog.quarkslab.com/technical-di...
(promise this one is legit 👀)
My latest post highlights the advanced tactics used to bypass security controls and deceive even the most savvy users. Check it out ⤵️
Learn some infrastructure tricks and delivery methods to bypass common detection.
👉 blog.quarkslab.com/technical-di...
(promise this one is legit 👀)

Learn some infrastructure tricks and delivery methods to bypass common detection.
👉 blog.quarkslab.com/technical-di...
(promise this one is legit 👀)


Check it out 👇
casvancooten.com/posts/2025/0...

Check it out 👇
casvancooten.com/posts/2025/0...
Mathieu Farrell shows you how in the "Pwn Everything, Bounce Everywhere, all at once" blog post series.
blog.quarkslab.com/pwn-everythi...

Mathieu Farrell shows you how in the "Pwn Everything, Bounce Everywhere, all at once" blog post series.
blog.quarkslab.com/pwn-everythi...
In part 2 of "Pwn Everything, Bounce Everywhere, all at once" Mathieu Farrell tells you how to chain them for unautheticated RCE
blog.quarkslab.com/pwn-everythi...

In part 2 of "Pwn Everything, Bounce Everywhere, all at once" Mathieu Farrell tells you how to chain them for unautheticated RCE
blog.quarkslab.com/pwn-everythi...
👉 blog.scrt.ch/2025/02/18/r...
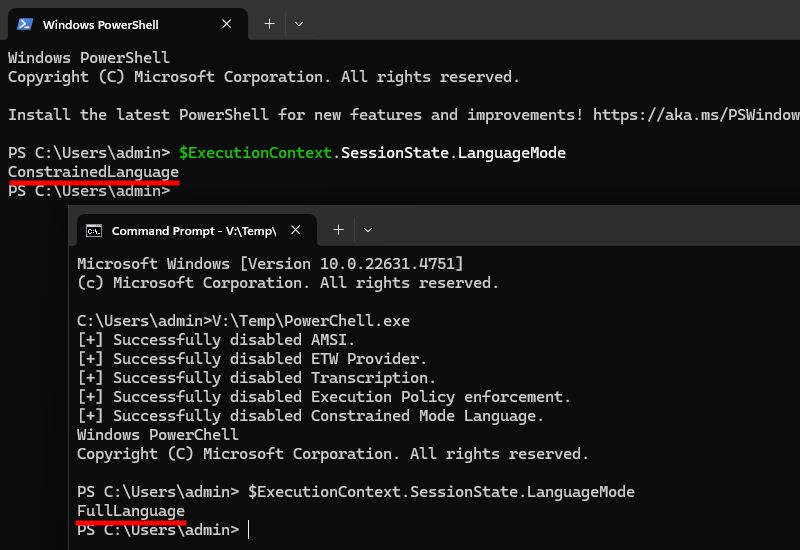
👉 blog.scrt.ch/2025/02/18/r...

