When building critical security infrastructure, the foundation matters. While open-source tools provide valuable building blocks, complex challenges like DNS wildcard detection require purpose-built solutions.
When building critical security infrastructure, the foundation matters. While open-source tools provide valuable building blocks, complex challenges like DNS wildcard detection require purpose-built solutions.
Modern enterprise infrastructure has evolved significantly. Today's environments are cloud-distributed, protected by Web Application Firewalls, and delivered through Content Delivery Networks.
Modern enterprise infrastructure has evolved significantly. Today's environments are cloud-distributed, protected by Web Application Firewalls, and delivered through Content Delivery Networks.
A key insight from our Surfacing Security podcast: Organisations face two major hurdles with security automation. Let's break down why the skill gap remains such a persistent challenge...
A key insight from our Surfacing Security podcast: Organisations face two major hurdles with security automation. Let's break down why the skill gap remains such a persistent challenge...
A key insight from our Surfacing Security podcast: The power of deep analysis isn't just in what it finds - it's in how it scales. The traditional view that deep analysis can't scale efficiently? That's being turned on its head.
A key insight from our Surfacing Security podcast: The power of deep analysis isn't just in what it finds - it's in how it scales. The traditional view that deep analysis can't scale efficiently? That's being turned on its head.
Years before ASM became an industry buzzword, we identified a crucial gap in security: the need to continuously monitor EVERYTHING across an attack surface.
Years before ASM became an industry buzzword, we identified a crucial gap in security: the need to continuously monitor EVERYTHING across an attack surface.
Finding vulnerabilities is just the beginning.
The path to effective remediation is longer than most realise...
Finding vulnerabilities is just the beginning.
The path to effective remediation is longer than most realise...
In our latest Surfacing Security episode, we challenge the conventional understanding of ASM and explore its true potential - because ASM isn't just about asset discovery, it's about what you do with that information.
In our latest Surfacing Security episode, we challenge the conventional understanding of ASM and explore its true potential - because ASM isn't just about asset discovery, it's about what you do with that information.
What happens when you combine comprehensive attack surface visibility with continuous monitoring?
What happens when you combine comprehensive attack surface visibility with continuous monitoring?
A key insight from our latest podcast: The security industry has a data obsession, but data alone doesn't protect your organization. The traditional approach of bigger wordlists, faster tools, and wider scanning isn't enough.
A key insight from our latest podcast: The security industry has a data obsession, but data alone doesn't protect your organization. The traditional approach of bigger wordlists, faster tools, and wider scanning isn't enough.
#attacksurfacemanagement

#attacksurfacemanagement
Modern cloud infrastructure is transforming how applications are deployed. But it's also creating massive blind spots in traditional security scanning.
Modern cloud infrastructure is transforming how applications are deployed. But it's also creating massive blind spots in traditional security scanning.
A platform where security research drives our exposure discovery engine, not just CVE matching.
A platform where security research drives our exposure discovery engine, not just CVE matching.
Over the last 10 years, Attack Surfaces have evolved. With SaaS, CDNs and Cloud Platforms, the IT environment has expanded significantly.
Over the last 10 years, Attack Surfaces have evolved. With SaaS, CDNs and Cloud Platforms, the IT environment has expanded significantly.

🎧 Listen to Surfacing Security
Spotify: https://buff.ly/3BFRth2
Apple Podcasts: https://buff.ly/3TTe6F3
YouTube: https://buff.ly/3ZfTb28
#CyberSec #ASM

🎧 Listen to Surfacing Security
Spotify: https://buff.ly/3BFRth2
Apple Podcasts: https://buff.ly/3TTe6F3
YouTube: https://buff.ly/3ZfTb28
#CyberSec #ASM
Order of operations bugs are one of my favorite types of bugs :) Write up and exploit script here: assetnote.io/resources/re...
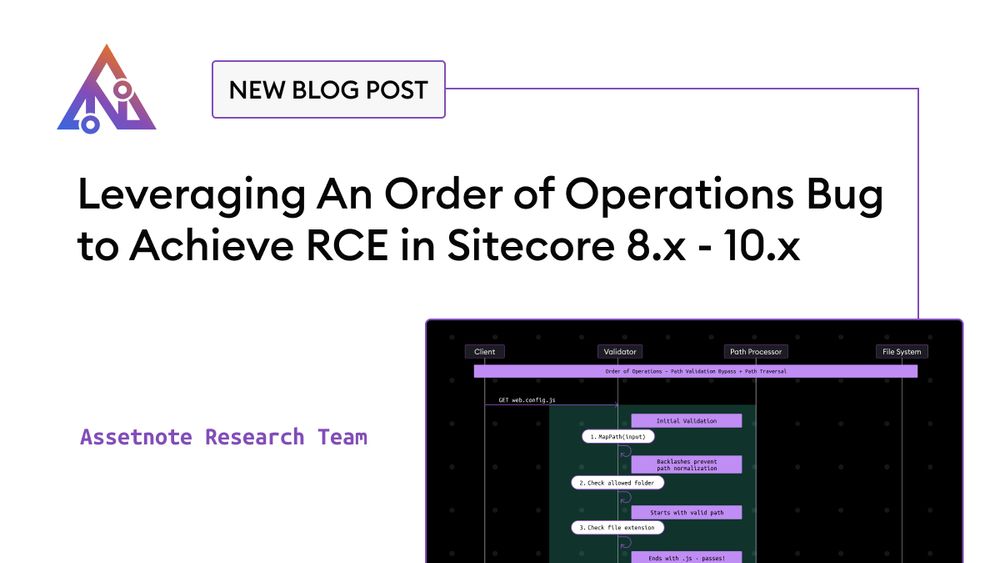
Order of operations bugs are one of my favorite types of bugs :) Write up and exploit script here: assetnote.io/resources/re...

