From Namur, BE.

I'm slowly making progress. For now I can redirect users to arbitrary URLs by poisoning the queue like you showed in your paper.
Stealing other people's responses would be much cooler though :)

I'm slowly making progress. For now I can redirect users to arbitrary URLs by poisoning the queue like you showed in your paper.
Stealing other people's responses would be much cooler though :)





But I can't get a valid response unfortunately...

But I can't get a valid response unfortunately...
And thanks @jameskettle.com for the race condition custom action, it's really convenient to have it directly in Repeater.
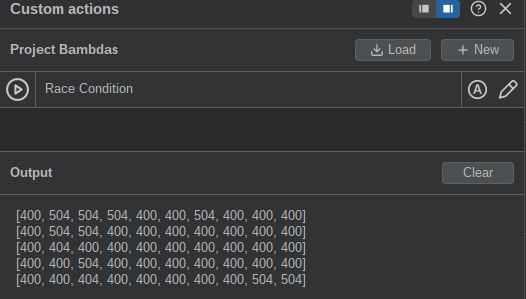
And thanks @jameskettle.com for the race condition custom action, it's really convenient to have it directly in Repeater.
- only use your own accounts to test,
- create multiple accounts to test for access control issues,
- use your bug bounty platform email otherwise you're not elligible for a bounty.
Also bug bounty program:

- only use your own accounts to test,
- create multiple accounts to test for access control issues,
- use your bug bounty platform email otherwise you're not elligible for a bounty.
Also bug bounty program:




It's so cool to be able test things locally, and see the result of proxying weird chars in HTTP requests.

It's so cool to be able test things locally, and see the result of proxying weird chars in HTTP requests.
This one returns the page code when I do a POST on this aspx endpoint.

This one returns the page code when I do a POST on this aspx endpoint.











