If you are using the Teams webhook with Microsoft's Verified ID Helpdesk sample, you should not trust any of the notifications you receive 😬
Unfortunately, everything is exposed to and sent by the client with no validation that user verification was performed :(
graph.microsoft.com/...
I built a Logic App that was working but now sees no data. If anyone knows other sources for Verified ID transactions, LMK! :)
If you are using the Teams webhook with Microsoft's Verified ID Helpdesk sample, you should not trust any of the notifications you receive 😬
Unfortunately, everything is exposed to and sent by the client with no validation that user verification was performed :(
office365itpros.com/2025/08/15/m...
#Microsoft365

office365itpros.com/2025/08/15/m...
#Microsoft365
🛡️ Microsoft Sentinel’s modern security data lake is a game-changer for SOC teams, CISOs, and security architects. In this article, I break down:
📌 Unified Data Management — onboarding all your security data across clouds and…

🛡️ Microsoft Sentinel’s modern security data lake is a game-changer for SOC teams, CISOs, and security architects. In this article, I break down:
📌 Unified Data Management — onboarding all your security data across clouds and…
Now comes part 3 and the logs are finally available to the masses.
#EntraID #KQL #Security
cloudbrothers.info/en/detect-th...

Now comes part 3 and the logs are finally available to the masses.
#EntraID #KQL #Security
cloudbrothers.info/en/detect-th...
I haven't seen any announcements on this and guidance is extremely lacking, so Joe Stocker gave me time to create a script to help everyone assess costs early :)
I would love your feedback!
github.com/nathanmcnult...
I haven't seen any announcements on this and guidance is extremely lacking, so Joe Stocker gave me time to create a script to help everyone assess costs early :)
I would love your feedback!
github.com/nathanmcnult...
#powershell #graph #MSIntune
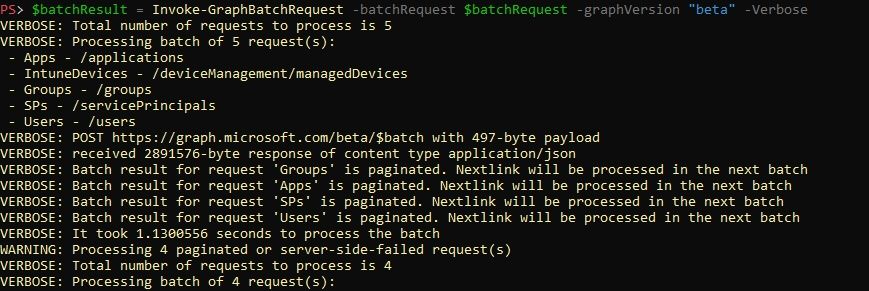
#powershell #graph #MSIntune
Check the claims field, the tenant ID is contained within the claim and you can use something like aadinternals.com/osint/ to find out which tenant the caller is from.
Check the claims field, the tenant ID is contained within the claim and you can use something like aadinternals.com/osint/ to find out which tenant the caller is from.
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
This new feature in Defender for Endpoint shows the effective configuration and the source the settings came from
Very helpful for troubleshooting :)
learn.microsoft.com/...
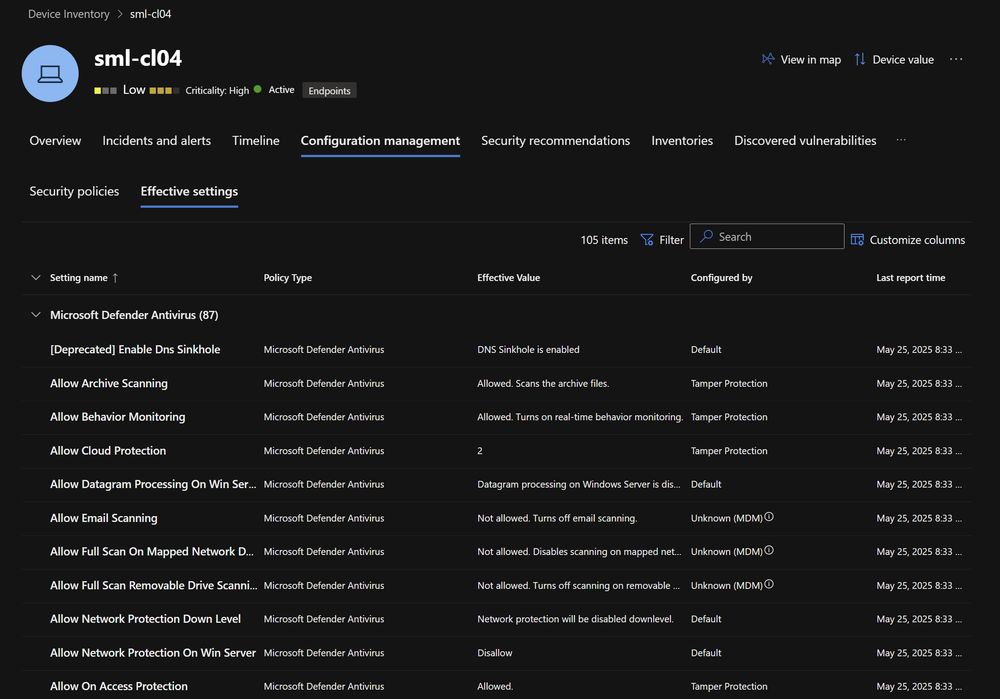
This new feature in Defender for Endpoint shows the effective configuration and the source the settings came from
Very helpful for troubleshooting :)
learn.microsoft.com/...
#Windows #WindowsUpdate #MsIntune #Automation
inthecloud247.com/automaticall...

#Windows #WindowsUpdate #MsIntune #Automation
inthecloud247.com/automaticall...
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
merill.net/2024/07/prop...
#PowerShell #MMSMOA

merill.net/2024/07/prop...
#PowerShell #MMSMOA

microsoftedge.microsoft.com/addons/detai...
microsoftedge.microsoft.com/addons/detai...
#Security #MicrosoftSecurity #Cybersecurity #SFI #SecureFutureInitiative

#Security #MicrosoftSecurity #Cybersecurity #SFI #SecureFutureInitiative
Protect your users!
ONLY send them to the official download link 👇
Bookmark this! Update your user guides & intranet NOW. RT to spread the word!
#CyberSecurity #MFA
🧵↓
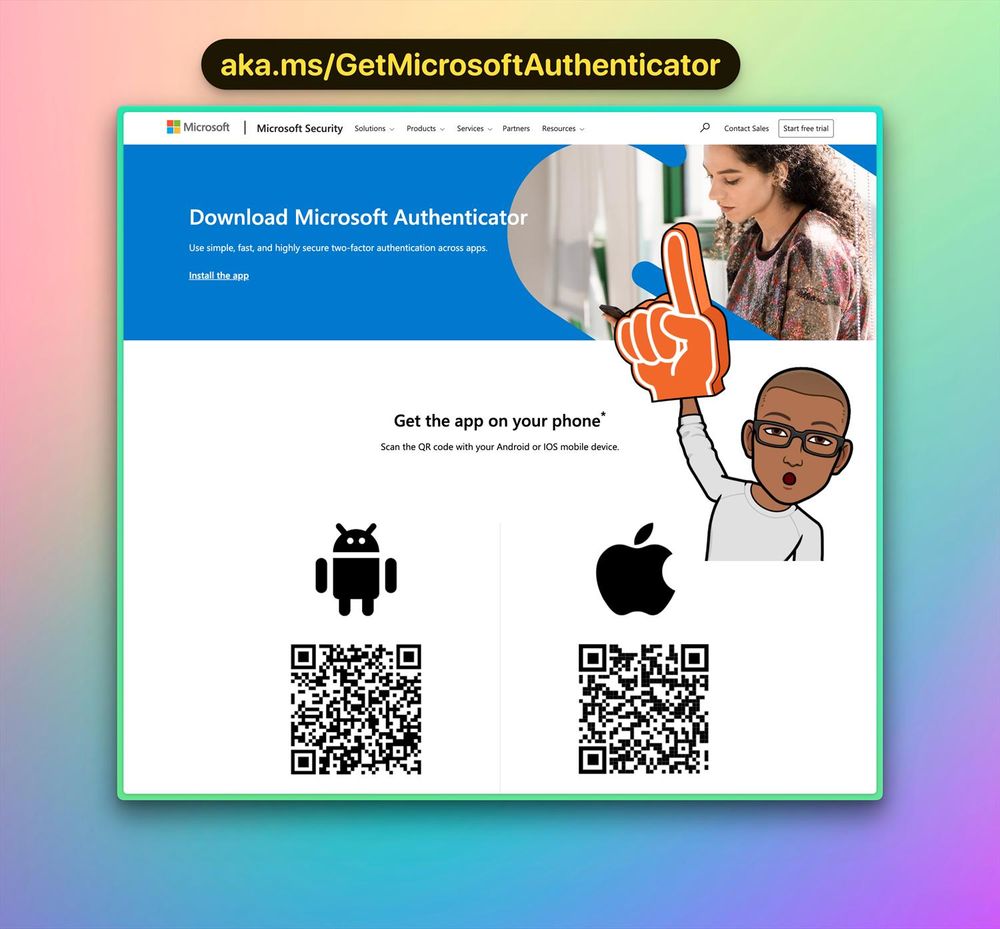
Protect your users!
ONLY send them to the official download link 👇
Bookmark this! Update your user guides & intranet NOW. RT to spread the word!
#CyberSecurity #MFA
🧵↓
I tried really hard to make this as short and simple as possible. Please be nice to your IR folks and set this up, it's important ;)
nathanmcnulty.com/bl...

I tried really hard to make this as short and simple as possible. Please be nice to your IR folks and set this up, it's important ;)
nathanmcnulty.com/bl...
office365itpros.com/2025/04/14/m...
#Microsoft365
office365itpros.com/2025/04/14/m...
#Microsoft365
For reference, here's the article:
blog.admindroid.com/...
Short thread, but my primary concern is privilege escalation

For reference, here's the article:
blog.admindroid.com/...
Short thread, but my primary concern is privilege escalation
learn.microsoft.com/...
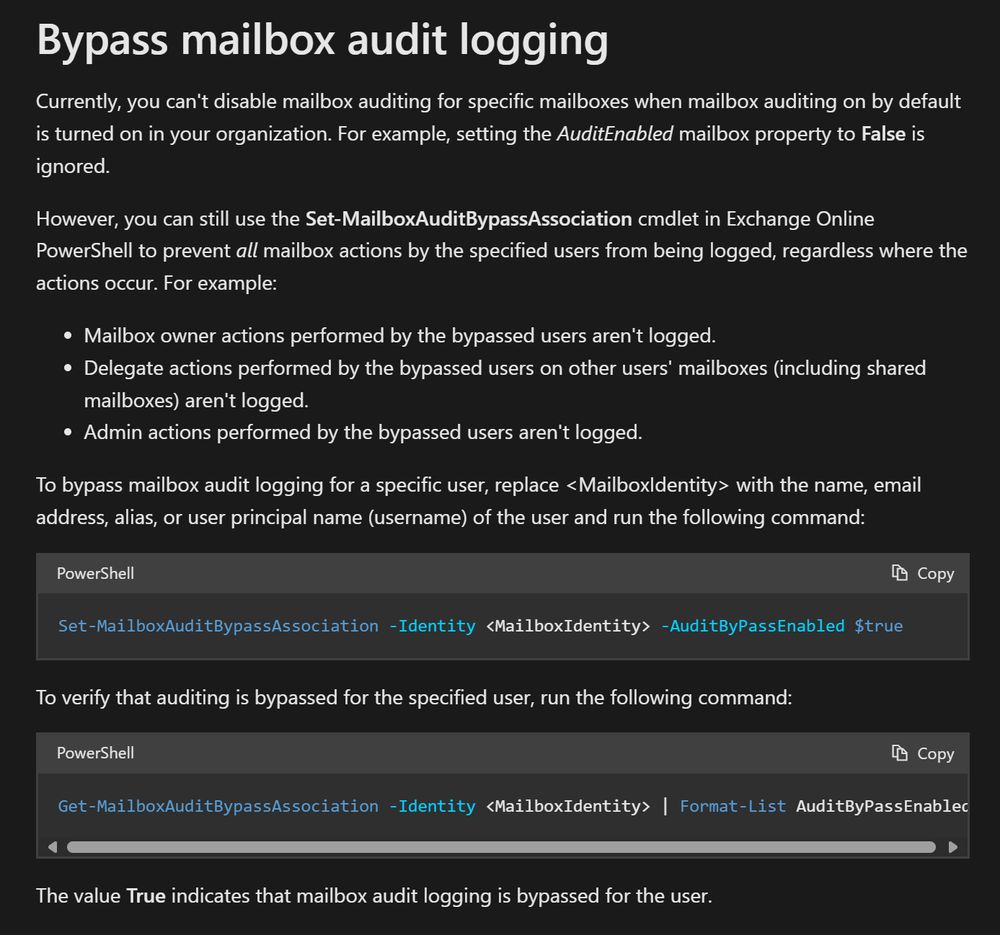
learn.microsoft.com/...
Get-MgBetaAuditLogSignIn -Filter "signInEventTypes/any(t: t eq 'servicePrincipal') and servicePrincipalId eq '00000000-0000-0000-0000-000000000000'" | Out-GridView -PassThru | ForEach-Object {New-MgBetaServicePrincipal -AppId $_.appId}
learn.microsoft.com/...
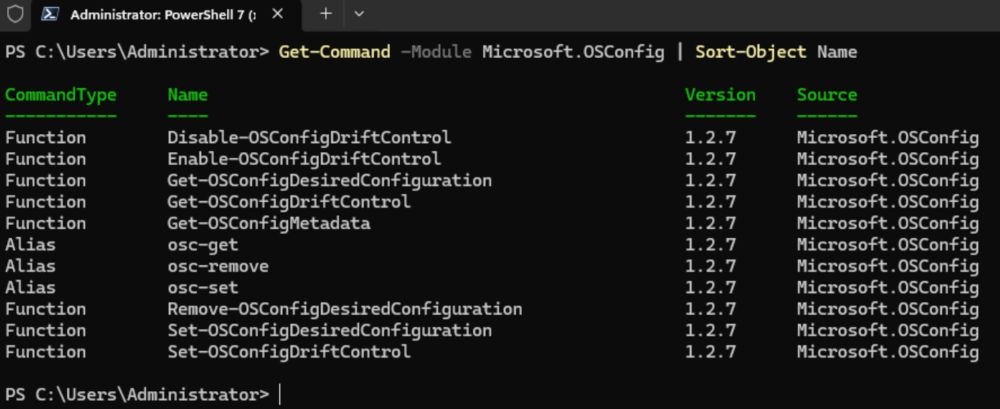
I'd like to automate discovery and remediation for admins, but I need help testing :)

Get-MgBetaAuditLogSignIn -Filter "signInEventTypes/any(t: t eq 'servicePrincipal') and servicePrincipalId eq '00000000-0000-0000-0000-000000000000'" | Out-GridView -PassThru | ForEach-Object {New-MgBetaServicePrincipal -AppId $_.appId}
powershellisfun.com/2025/04/04/i...
#PowerShell #Security #OSConfig
powershellisfun.com/2025/04/04/i...
#PowerShell #Security #OSConfig
I got to talk with @merill.net recently about Restricted Management Admin Units, but some noted they break Access Packages and PIM making them less useful
While true by design, we can actually fix this!
nathanmcnulty.com/blog/2025/04...

I got to talk with @merill.net recently about Restricted Management Admin Units, but some noted they break Access Packages and PIM making them less useful
While true by design, we can actually fix this!
nathanmcnulty.com/blog/2025/04...
learn.microsoft.com/...
I'd like to automate discovery and remediation for admins, but I need help testing :)

learn.microsoft.com/...
I'd like to automate discovery and remediation for admins, but I need help testing :)
office365itpros.com/2025/04/03/t...

office365itpros.com/2025/04/03/t...

