
%AppData%\Arkanix_lol\history.json
%AppData%\Arkanix_lol\system_info.json
%AppData%\Arkanix_lol\screenshot_monitor_1.png
Akranix botnet C2:
📡 arkanix .pw/api/session/create
📡 arkanix .pw/delivery
📡 arkanix .pw/api/discord-injection/template

%AppData%\Arkanix_lol\history.json
%AppData%\Arkanix_lol\system_info.json
%AppData%\Arkanix_lol\screenshot_monitor_1.png
Akranix botnet C2:
📡 arkanix .pw/api/session/create
📡 arkanix .pw/delivery
📡 arkanix .pw/api/discord-injection/template
👉 hunting.abuse.ch/hunt/6919ec1...
Botnet C2 domains:
📡defender-temeerty .sbs
📡telemetry-defender .lol
Botnet C2 server:
🛑185.100.157.69:443 (Partner Hosting 🇬🇧)
Malware sample:
📄 bazaar.abuse.ch/sample/903cd...

👉 hunting.abuse.ch/hunt/6919ec1...
Botnet C2 domains:
📡defender-temeerty .sbs
📡telemetry-defender .lol
Botnet C2 server:
🛑185.100.157.69:443 (Partner Hosting 🇬🇧)
Malware sample:
📄 bazaar.abuse.ch/sample/903cd...
Full list of Rhadamanthys botnet C2s:
📡 threatfox.abuse.ch/browse/tag/O...
Europol press release:
🚨 www.europol.europa.eu/media-press/...

Full list of Rhadamanthys botnet C2s:
📡 threatfox.abuse.ch/browse/tag/O...
Europol press release:
🚨 www.europol.europa.eu/media-press/...
👏 Huge shoutout to Juroots, our top contributor with 2,746 IOCs submitted.
💀 The most-shared malware family (or in this case framework)? Clearfake, with 2,817 IOCs reported. ⤵️

👏 Huge shoutout to Juroots, our top contributor with 2,746 IOCs submitted.
💀 The most-shared malware family (or in this case framework)? Clearfake, with 2,817 IOCs reported. ⤵️
#milestone #community #grateful #sharingiscaring 😻

#milestone #community #grateful #sharingiscaring 😻
Malicious bash script:
📜https://bazaar.abuse.ch/sample/27e2a9abfeb5f72746931dff55cd21b6631bab3aa13d8a1cb67c9319d8692229/

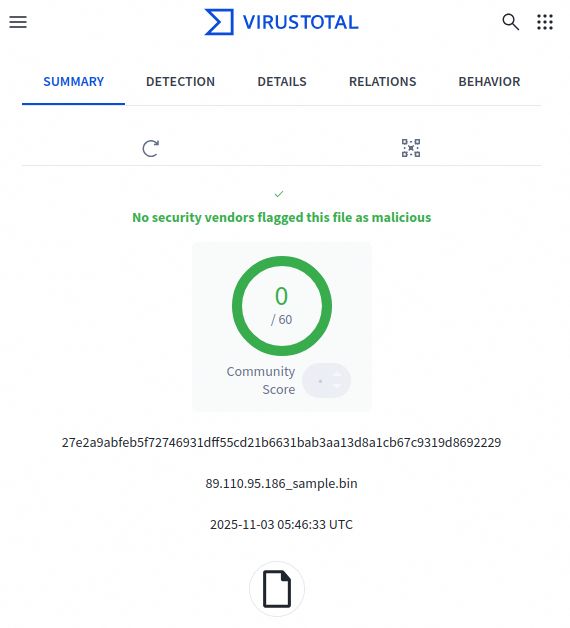
Malicious bash script:
📜https://bazaar.abuse.ch/sample/27e2a9abfeb5f72746931dff55cd21b6631bab3aa13d8a1cb67c9319d8692229/
That’s all you. That’s the power of our #community🤘
#AmazingWork #SharingIsCaring

That’s all you. That’s the power of our #community🤘
#AmazingWork #SharingIsCaring
First seen: 30 March 2020 and since then, they’ve shared 45,994 malware samples.
In the last 30 days alone, they have dropped 1,472 new samples, that’s +30% ⬆️ from the previous month, with 631 samples shared on September 30th. 🔥🔥
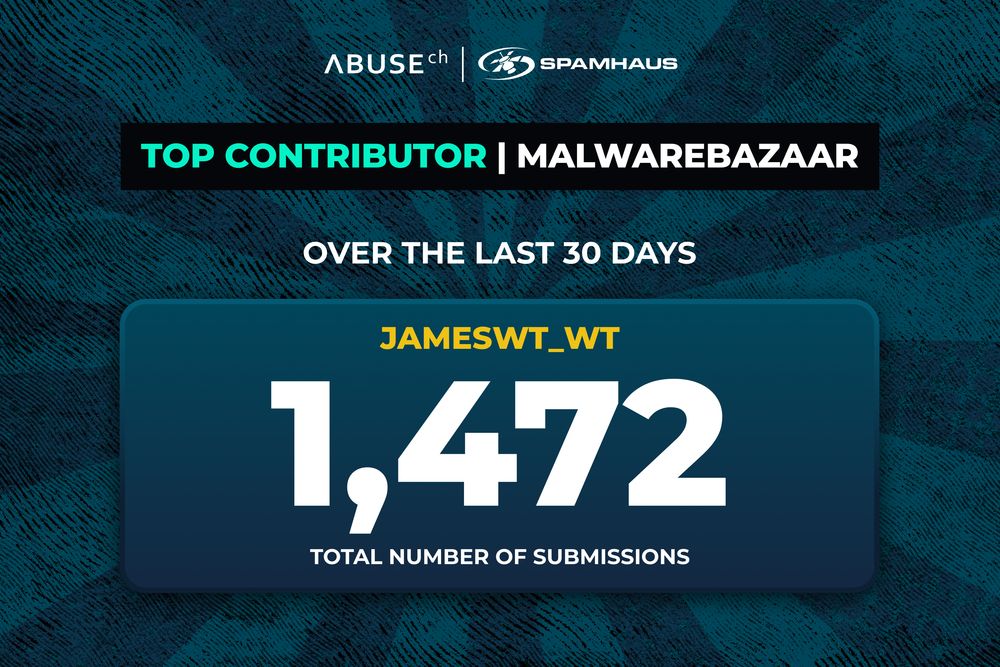
First seen: 30 March 2020 and since then, they’ve shared 45,994 malware samples.
In the last 30 days alone, they have dropped 1,472 new samples, that’s +30% ⬆️ from the previous month, with 631 samples shared on September 30th. 🔥🔥
Find more ThreatFox statistics here:
👉 threatfox.abuse.ch/statistics
#SharingIsCaring #XtremeRAT #Malware #ThreatIntel
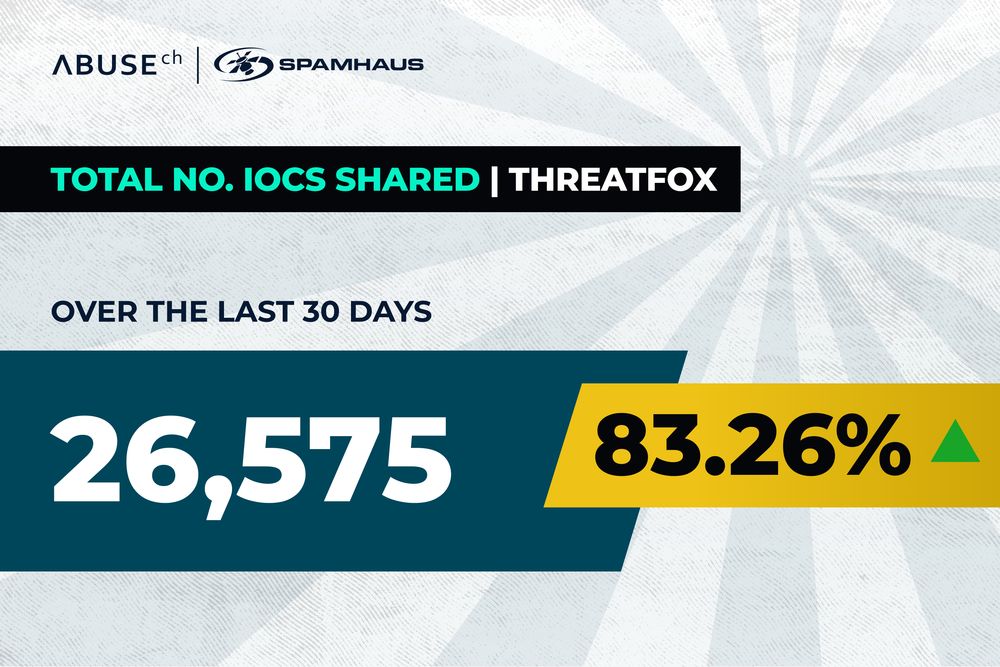
Find more ThreatFox statistics here:
👉 threatfox.abuse.ch/statistics
#SharingIsCaring #XtremeRAT #Malware #ThreatIntel
➡️ OpenTIP integration: Results from @kasperskylab.bsky.social OpenTIP are now included for all samples on MalwareBazaar, available via both, UI and API 🖥️

➡️ OpenTIP integration: Results from @kasperskylab.bsky.social OpenTIP are now included for all samples on MalwareBazaar, available via both, UI and API 🖥️
129.226.128.168:443 (Tencent 🇨🇳)
31.220.109.219:443 (Hostinger 🇺🇸)
165.227.143.219:443 (DigitalOcean🇺🇸)
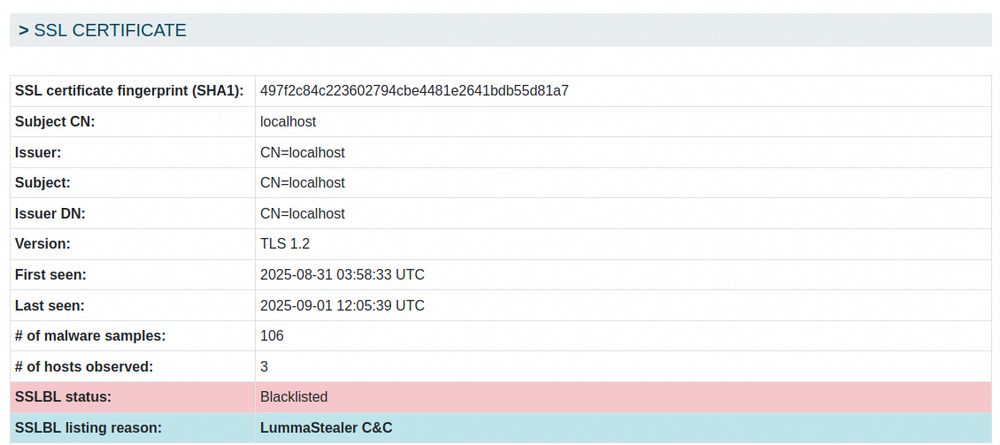
129.226.128.168:443 (Tencent 🇨🇳)
31.220.109.219:443 (Hostinger 🇺🇸)
165.227.143.219:443 (DigitalOcean🇺🇸)
Botnet C2: sophos-upd-srv .info 🇳🇱
Botnet C2: sophos-upd-srv .info 🇳🇱
microsoft-telemetry .cc
telemety-sys .lol
telemety-xbox .lol
witasametry .live
telamtykina .live
telemetrywatson .live
More Amadey IOCs are available on ThreatFox 🦊:
📡https://threatfox.abuse.ch/browse/malware/win.amadey/

microsoft-telemetry .cc
telemety-sys .lol
telemety-xbox .lol
witasametry .live
telamtykina .live
telemetrywatson .live
More Amadey IOCs are available on ThreatFox 🦊:
📡https://threatfox.abuse.ch/browse/malware/win.amadey/
urlhaus.abuse.ch/host/172.233...
Payload:
bazaar.abuse.ch/sample/dafb6...
IOCs:
threatfox.abuse.ch/browse/tag/D...
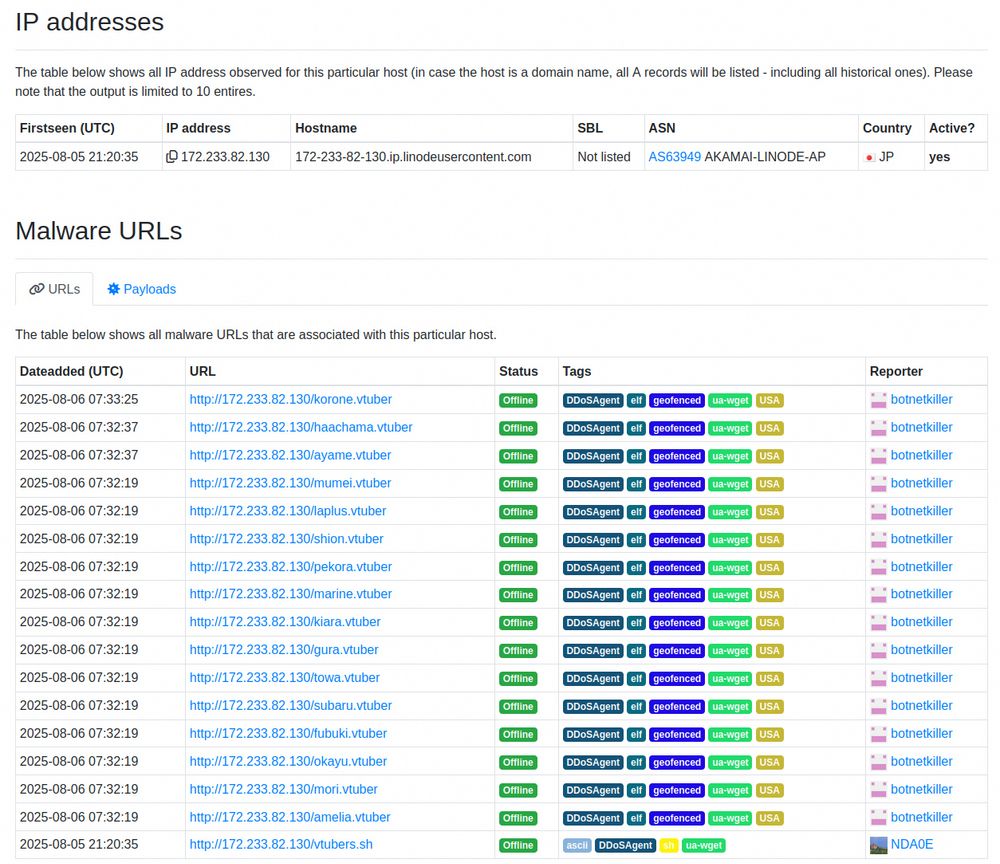
urlhaus.abuse.ch/host/172.233...
Payload:
bazaar.abuse.ch/sample/dafb6...
IOCs:
threatfox.abuse.ch/browse/tag/D...
Malware sample:
📄https://bazaar.abuse.ch/sample/8b94f5fa94f35e5ba47ce260b009b34401c5c54042d7b7252c8c7d13bf8d9f05/
Admin Panel:
📡https://salat .cn/login/ (Cloudflare)
Gihub:
🗜️https://github.com/webr-at/importantfiles/releases

Malware sample:
📄https://bazaar.abuse.ch/sample/8b94f5fa94f35e5ba47ce260b009b34401c5c54042d7b7252c8c7d13bf8d9f05/
Admin Panel:
📡https://salat .cn/login/ (Cloudflare)
Gihub:
🗜️https://github.com/webr-at/importantfiles/releases
➡️ hunting.abuse.ch/hunt/6890d35...
Payload delivery URL + botnet C2 are hosted at 51.89.204 .89 (StarkRDP 🇩🇪)

➡️ hunting.abuse.ch/hunt/6890d35...
Payload delivery URL + botnet C2 are hosted at 51.89.204 .89 (StarkRDP 🇩🇪)
See below for more...

See below for more...
To protect the future of the platforms and the community behind them, we've been making changes. Read more ⤵️ abuse.ch/blog/creatin...

To protect the future of the platforms and the community behind them, we've been making changes. Read more ⤵️ abuse.ch/blog/creatin...
You may want to block this network at your network edge 🛑

You may want to block this network at your network edge 🛑
It's 🍿 time!

It's 🍿 time!
www.europol.europa.eu/media-press/...

www.europol.europa.eu/media-press/...
Halkbank Ekstre.jar
\strlogs\keylogs_4558.html
Botnet C2:
📡77.90.153.31:5590 (AS214943 RAILNET 🇺🇸)
Malware sample:
📄https://bazaar.abuse.ch/sample/daf23a217b188f63657b051fda8bbd6eb341172b9519b9b5bff1a60eb4dda5a1/
Halkbank Ekstre.jar
\strlogs\keylogs_4558.html
Botnet C2:
📡77.90.153.31:5590 (AS214943 RAILNET 🇺🇸)
Malware sample:
📄https://bazaar.abuse.ch/sample/daf23a217b188f63657b051fda8bbd6eb341172b9519b9b5bff1a60eb4dda5a1/


