www.eff.org/deeplinks/20...

www.eff.org/deeplinks/20...
Founder + President of Volexity leading a team of experts that deal w/ complex cyber intrusions from nation-state level intruders. His talk will cover a Chinese APT actor that Volexity tracks as UTA0388.
Check out the official agenda:
cyberwarcon.com

Founder + President of Volexity leading a team of experts that deal w/ complex cyber intrusions from nation-state level intruders. His talk will cover a Chinese APT actor that Volexity tracks as UTA0388.
Check out the official agenda:
cyberwarcon.com
www.volexity.com/blog/2025/10...

www.volexity.com/blog/2025/10...

Course details: memoryanalysis.net/courses-malw...

doublepulsar.com/citrixbleed-...
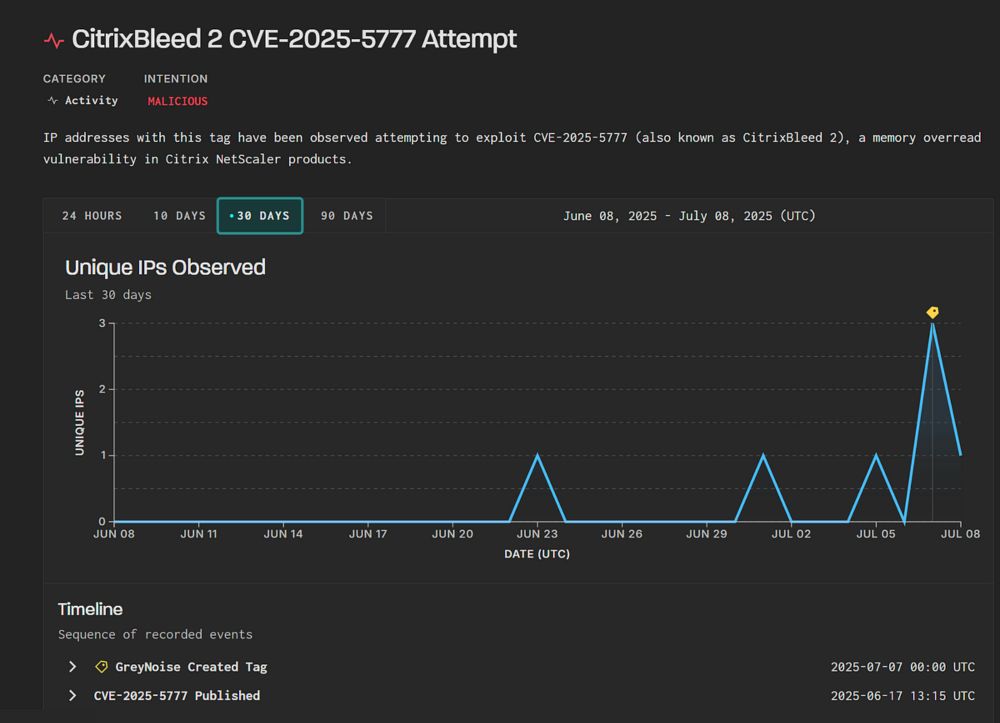
doublepulsar.com/citrixbleed-...
www.volexity.com/blog/2025/04... #dfir
www.volexity.com/blog/2025/04... #dfir
www.ncsc.gov.uk/news/ncsc-pa...

www.ncsc.gov.uk/news/ncsc-pa...
look no further than this VSCode extension built by @jacoblatonis.me
marketplace.visualstudio.com/items?itemNa...

look no further than this VSCode extension built by @jacoblatonis.me
marketplace.visualstudio.com/items?itemNa...
With the amount of Next.js-based sites around, especially on infosec sites, I'd say this looks like a problem.
CVSS: 9.1
github.com/vercel/next....
With the amount of Next.js-based sites around, especially on infosec sites, I'd say this looks like a problem.
CVSS: 9.1
github.com/vercel/next....
#dfir #threatintel #m365security
#dfir #threatintel #m365security

#dfir #threatintel #m365security
Key:
- Unpatched credential disclosure 0day in VPN client that's actively exploited in the wild
- Volexity assesses with medium confidence that BrazenBamboo is a private enterprise that produces capabilities for governmental operators concerned with domestic targets

Key:
- Unpatched credential disclosure 0day in VPN client that's actively exploited in the wild
- Volexity assesses with medium confidence that BrazenBamboo is a private enterprise that produces capabilities for governmental operators concerned with domestic targets

