
Researcher @binarly • PhD Candidate @TUBerlin •
Capturing Flags with ENOFLAG

so I built my own paper discovery website:
a minimalistic design with high information density and full control over search terms.

so I built my own paper discovery website:
a minimalistic design with high information density and full control over search terms.
just replace 'github' with 'deepwiki' in a repo's url and it will generate an architecture overview, explanations for components, flow diagrams etc.
I tried it on large code bases like afl++ and libafl and it's actually impressive

just replace 'github' with 'deepwiki' in a repo's url and it will generate an architecture overview, explanations for components, flow diagrams etc.
I tried it on large code bases like afl++ and libafl and it's actually impressive
So, what is SURE? More in the 🧵
@momo5502.bsky.social works on a high-perf windows emulator for security research.
I noticed that it supports icicle as a backend, a fuzzing-specific emulator. awesome to see academic work being continuously developed and making it into the real world
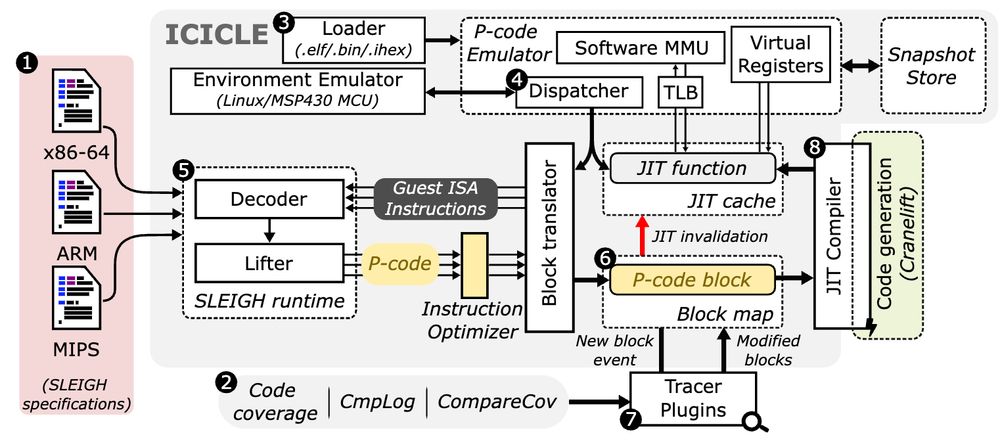
@momo5502.bsky.social works on a high-perf windows emulator for security research.
I noticed that it supports icicle as a backend, a fuzzing-specific emulator. awesome to see academic work being continuously developed and making it into the real world
but man these ml conferences look kinda dystopian

but man these ml conferences look kinda dystopian
I had an absolute blast speaking and being at
@re-verse.io, so many great talks and hallway discussions
I had an absolute blast speaking and being at
@re-verse.io, so many great talks and hallway discussions
reminds me of how @dmnk.bsky.social and I got the unicornafl rust bindings up and running to fuzz some basebands 5 years ago
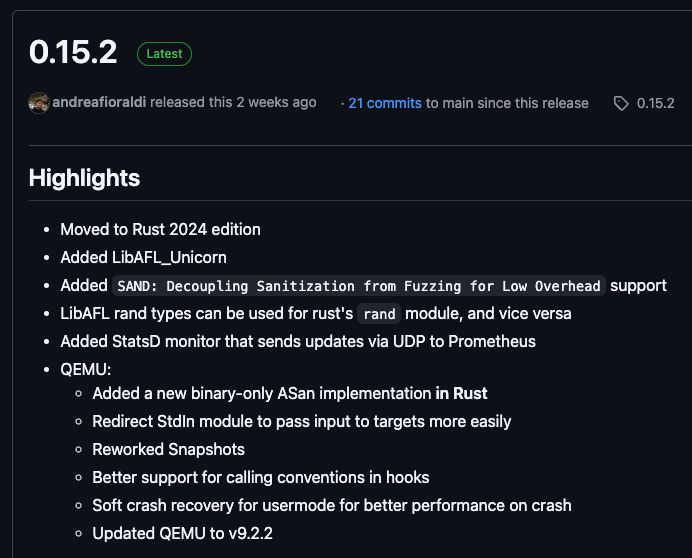
reminds me of how @dmnk.bsky.social and I got the unicornafl rust bindings up and running to fuzz some basebands 5 years ago
making firmware hacking maybe a little less painful
cc @stacksmashing.bsky.social
making firmware hacking maybe a little less painful
cc @stacksmashing.bsky.social
when it does what it's supposed to, it's great, but man is it trying hard to misinterpret my intentions.

when it does what it's supposed to, it's great, but man is it trying hard to misinterpret my intentions.
@ret2systems.bsky.social's Markus, incl. building a custom interposer to upgrade the CPU
a deep dive into hardware hacking, an ode to hw engineering and a call for software-focused researchers to try new things


@ret2systems.bsky.social's Markus, incl. building a custom interposer to upgrade the CPU
a deep dive into hardware hacking, an ode to hw engineering and a call for software-focused researchers to try new things
it has so many settings to tweak, different modes to select and the code can be quite scary at first.
but writing a target-specific custom fuzzer is super powerful!
to get started, Trail of Bits just published a nice primer:
appsec.guide/docs/fuzzing...
it has so many settings to tweak, different modes to select and the code can be quite scary at first.
but writing a target-specific custom fuzzer is super powerful!
to get started, Trail of Bits just published a nice primer:
appsec.guide/docs/fuzzing...
where is, it I miss it :/
anyone any recommendation for an alternative? some tunable feed of recent papers?
where is, it I miss it :/
anyone any recommendation for an alternative? some tunable feed of recent papers?
so many cool people and great discussions on firmware, fuzzing, ai and binary analysis
if you want to find out more about firmware rehosting or are an enjoyer of ascii diagrams, check out the slides to my talk below :)

so many cool people and great discussions on firmware, fuzzing, ai and binary analysis
if you want to find out more about firmware rehosting or are an enjoyer of ascii diagrams, check out the slides to my talk below :)
had a super fun day at Kennedy Space Center.
and then I got to witness my first rocket launch in person, a falcon 9 bringing Intuitive Machine's lunar lander into orbit.
my space-nerd heart is so happy.

had a super fun day at Kennedy Space Center.
and then I got to witness my first rocket launch in person, a falcon 9 bringing Intuitive Machine's lunar lander into orbit.
my space-nerd heart is so happy.
it addresses many of humanity's great questions:
- do we actually know how to do garbage collection?
- pointers, indices or handlers?
- and what are typesafe use-after-frees?

it addresses many of humanity's great questions:
- do we actually know how to do garbage collection?
- pointers, indices or handlers?
- and what are typesafe use-after-frees?
Join me for a retrospective:
mahaloz.re/dec-progr...

Join me for a retrospective:
mahaloz.re/dec-progr...

it provides a taxonomy of nearly all the available approaches and discusses the most important concepts, such as peripheral modeling and fidelity trade-offs

it provides a taxonomy of nearly all the available approaches and discusses the most important concepts, such as peripheral modeling and fidelity trade-offs
The BIFOLD Graduate School has 10 open PhD positions!
Join us in vibrant Berlin to work with top-notch researchers on machine learning, data management, and, of course, security!
🔗 mlsec.org/jobs.html#jobs
The BIFOLD Graduate School has 10 open PhD positions!
Join us in vibrant Berlin to work with top-notch researchers on machine learning, data management, and, of course, security!
🔗 mlsec.org/jobs.html#jobs
A blog post about how frustration with poor decompilation led me to dive deep into Ghidra's decompiler to discover (and reverse-engineer) - an obscure, undocumented DSL
msm.lt/re/ghidra/ru...
#reverseengineering #ghidra

A blog post about how frustration with poor decompilation led me to dive deep into Ghidra's decompiler to discover (and reverse-engineer) - an obscure, undocumented DSL
msm.lt/re/ghidra/ru...
#reverseengineering #ghidra
to continue the tradition, here is some of my favorite firmware & embedded security research of 2024:
Defeating the new Raspberry Pi's RP2350 Security Features [1]
Reversing and Hacking Firmware of an in-orbit Satellite to Re-establish Lost Communication [2]

to continue the tradition, here is some of my favorite firmware & embedded security research of 2024:
Defeating the new Raspberry Pi's RP2350 Security Features [1]
Reversing and Hacking Firmware of an in-orbit Satellite to Re-establish Lost Communication [2]
also, because that firmware didn't have an update mechanism
incredible talk!
media.ccc.de/v/38c3-hacki...

also, because that firmware didn't have an update mechanism
incredible talk!
media.ccc.de/v/38c3-hacki...

