Check out our website to view the agenda and plan your day, read more about our speakers, or buy a last minute ticket!
We can't wait to see everyone in Arlington, VA on November 19th!
www.cyberwarcon.com

Check out our website to view the agenda and plan your day, read more about our speakers, or buy a last minute ticket!
We can't wait to see everyone in Arlington, VA on November 19th!
www.cyberwarcon.com
🇦🇺 for my first Cyber Threat Intel talk! It was an amazing and surreal experience. A huge thanks to the organizers for having me and another thanks to everyone that attended!




🇦🇺 for my first Cyber Threat Intel talk! It was an amazing and surreal experience. A huge thanks to the organizers for having me and another thanks to everyone that attended!
Patrick has expertise in monitoring and defending against cyber espionage threat actors.
His talk, "Cyber(trade)war: Paradigm Shift in Economic Espionage", will cover the shift in PRC state-sponsored cyber espionage.
Learn more! www.cyberwarcon.com

Patrick has expertise in monitoring and defending against cyber espionage threat actors.
His talk, "Cyber(trade)war: Paradigm Shift in Economic Espionage", will cover the shift in PRC state-sponsored cyber espionage.
Learn more! www.cyberwarcon.com
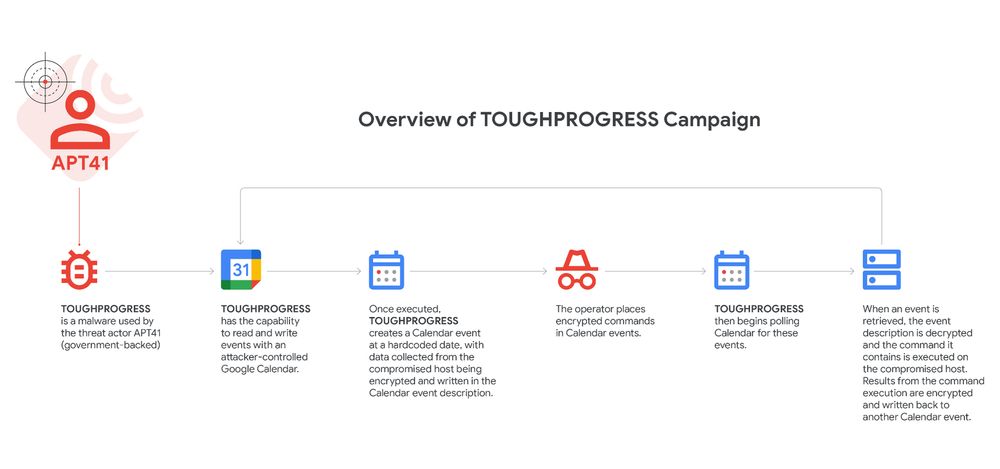
I wrote some more on COLDRIVER - specifically about their recent malware they have been using since at least May. If you’re on the COLDRIVER target list keep an eye out for this stuff. They have been more active with it than previous malware.

this year! The lineup looks amazing, as always. including a keynote with Dimitri Alperovitch. 🤯
Check out the full agenda here!
cyberwarcon.com/agenda-25

this year! The lineup looks amazing, as always. including a keynote with Dimitri Alperovitch. 🤯
Check out the full agenda here!
cyberwarcon.com/agenda-25
www.brighttalk.com/webcast/7451...

www.brighttalk.com/webcast/7451...
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...
Citizen Lab worked closely with one of the targets and shared their work on it also: citizenlab.ca/2025/06/russ...
Citizen Lab worked closely with one of the targets and shared their work on it also: citizenlab.ca/2025/06/russ...
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...