
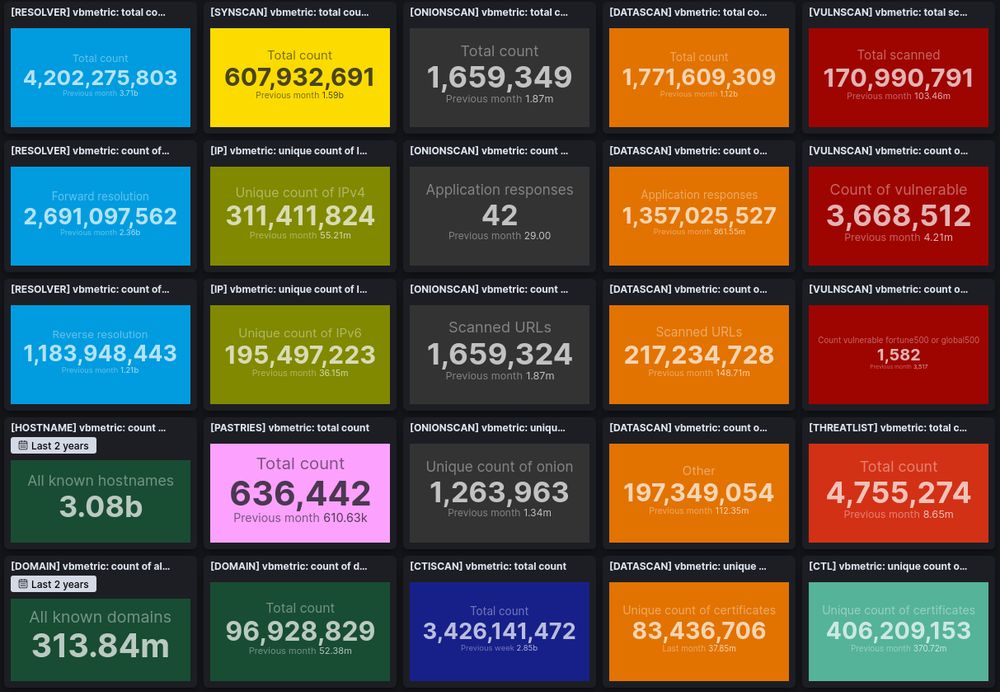
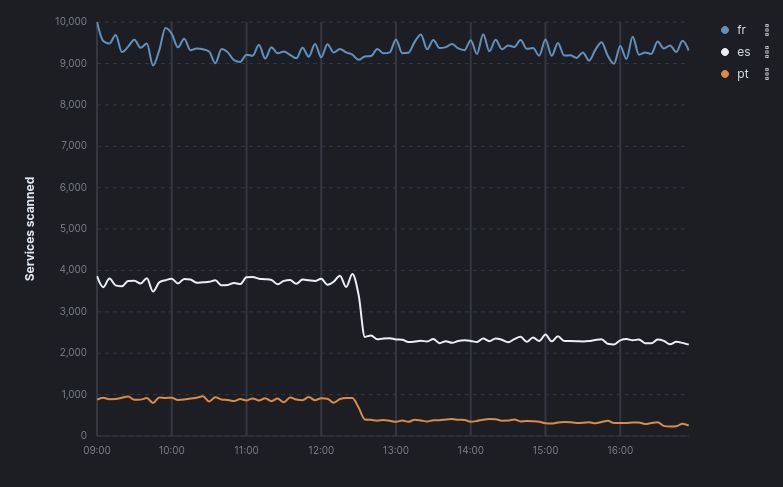
👉 Over the last 12 months, we massively increased our visibility of Internet exposed assets. Until now, we focused on #ASM, but this year we will improve our automatic #ASD and expand into the #CTI segment.
Read more: search.onyphe.io/docs/write-u...
It's been useful enough that I started extracting it to a standalone geolocus MCP server I shld be able to release in a couple days.
The @onyphe.io folks are super rad.
It's been useful enough that I started extracting it to a standalone geolocus MCP server I shld be able to release in a couple days.
The @onyphe.io folks are super rad.
CVE-2025-4427+CVE-2025-4428 unauth RCE
search.onyphe.io/search?q=cat...
Thanks to watchTowr for detection method.
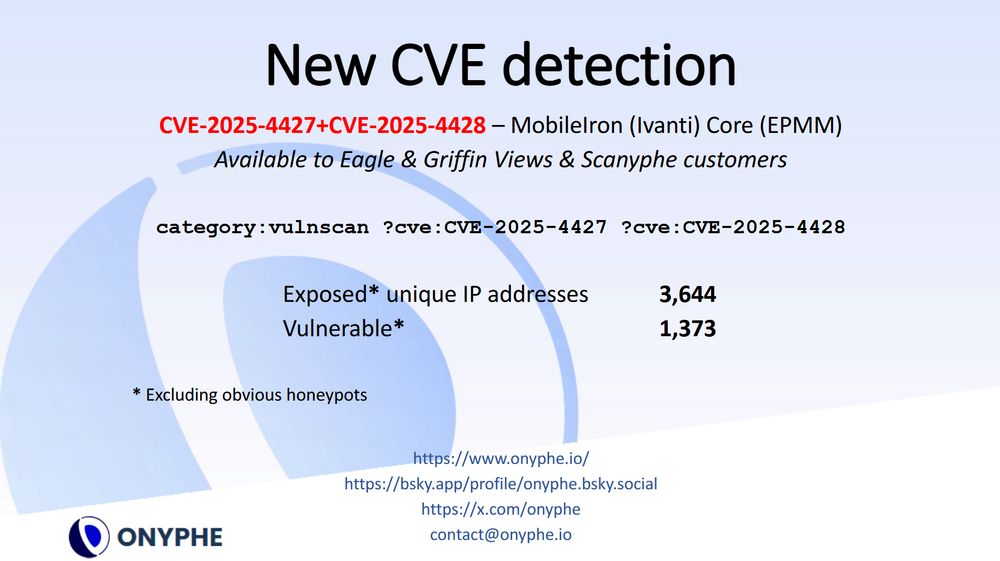
CVE-2025-4427+CVE-2025-4428 unauth RCE
search.onyphe.io/search?q=cat...
Thanks to watchTowr for detection method.
Since it's way more efficient to use this than their API, I built a cross-platform CLI tool for […]
[Original post on mastodon.social]
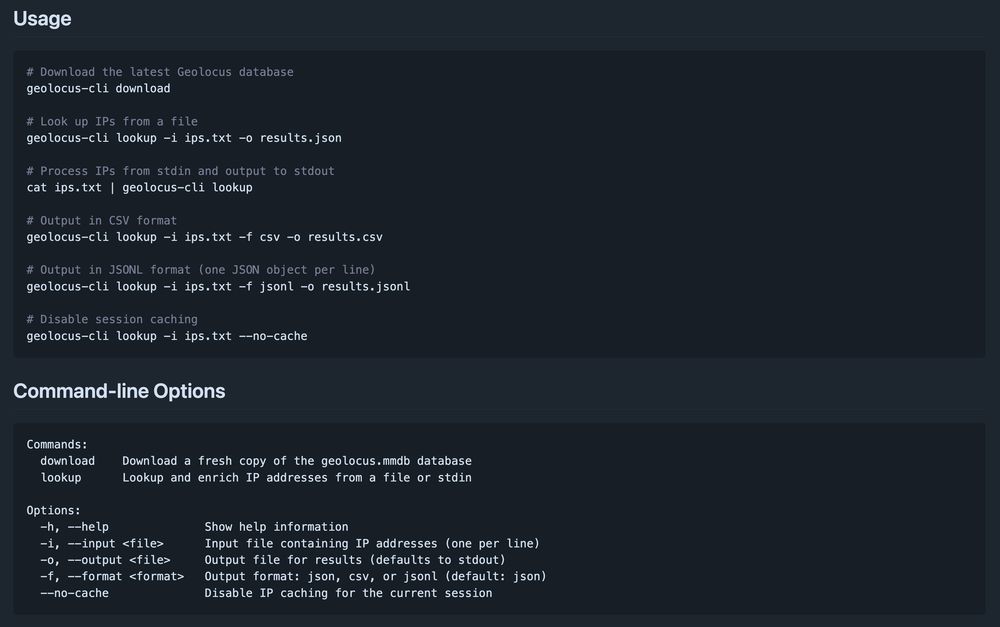
Since it's way more efficient to use this than their API, I built a cross-platform CLI tool for […]
[Original post on mastodon.social]
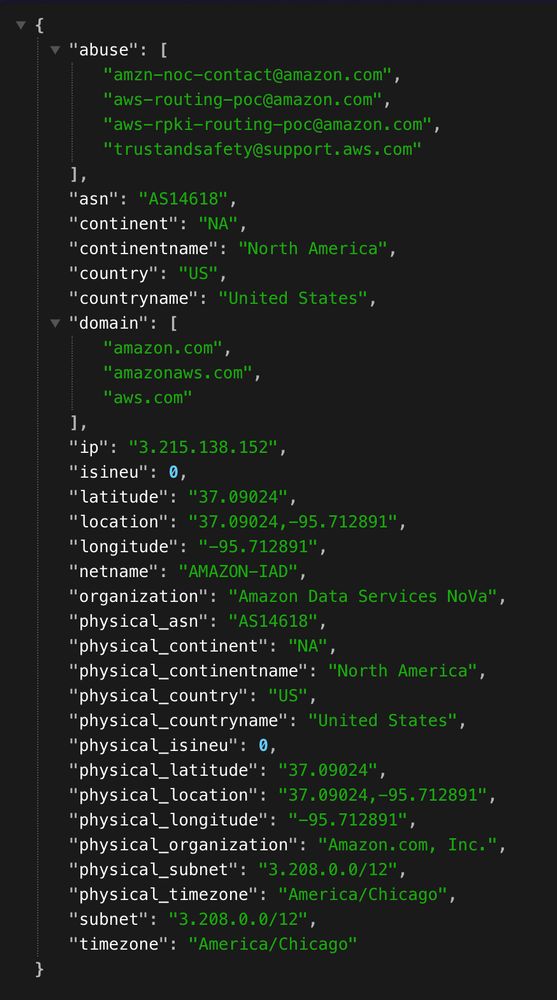
ONYPHE has made available a free API and free MMDB download of their new Geolocus database. It provided IP address metadata in the form of: { "abuse": [ "amzn-noc-contact@amazon.com", "aws-routing-poc@amazon.com", "aws-rpki-routing…
#hackernews #news
ONYPHE has made available a free API and free MMDB download of their new Geolocus database. It provided IP address metadata in the form of: { "abuse": [ "amzn-noc-contact@amazon.com", "aws-routing-poc@amazon.com", "aws-rpki-routing…
#hackernews #news

#PowerOutage

#PowerOutage
💥Unauthenticated Remote Code Execution. No CVSS yet, we suggest to give it a 10
📌40,000 IP addresses representing over 37,000 domain names exposed, 12,168 unique domains vulnerable
Blog:
blog.onyphe.io/en/cve-2025-...
💥Unauthenticated Remote Code Execution. No CVSS yet, we suggest to give it a 10
📌40,000 IP addresses representing over 37,000 domain names exposed, 12,168 unique domains vulnerable
Blog:
blog.onyphe.io/en/cve-2025-...
"we are willing to share it, privately"
More than 18k devices compromised
Read more: blog.onyphe.io/en/symlink-b...
"nous sommes prêts à la partager, en privé"
Plus de 18,000 équipements compromis
Lire l'article : blog.onyphe.io/backdoor-sym...
"nous sommes prêts à la partager, en privé"
Plus de 18,000 équipements compromis
Lire l'article : blog.onyphe.io/backdoor-sym...
"we are willing to share it, privately"
More than 18k devices compromised
Read more: blog.onyphe.io/en/symlink-b...
"we are willing to share it, privately"
More than 18k devices compromised
Read more: blog.onyphe.io/en/symlink-b...
👉We provide a free MMDB file for download and a brand new Website for lookups & even a free API access:
www.geolocus.io

👉We provide a free MMDB file for download and a brand new Website for lookups & even a free API access:
www.geolocus.io
Et aussi un podcast (coucou @nolimitsecu.bsky.social), des chiffres passionnants d' @onyphe.io et de La tech est politique et sa nouvelle rubrique.
www.linkedin.com/pulse/zero-d...

Et aussi un podcast (coucou @nolimitsecu.bsky.social), des chiffres passionnants d' @onyphe.io et de La tech est politique et sa nouvelle rubrique.
www.linkedin.com/pulse/zero-d...
Available here ➡️
search.onyphe.io/docs/onyphe-...
or here 🐳 hub.docker.com/r/onyphe/ony...
or even here 🥷 metacpan.org/dist/Onyphe
Available here ➡️
search.onyphe.io/docs/onyphe-...
or here 🐳 hub.docker.com/r/onyphe/ony...
or even here 🥷 metacpan.org/dist/Onyphe
#ASD #AttackSurfaceDiscovery APIs are on their way to general availability.
It will never be as easy to create an asset inventory for any organization attack surface #EASM
Backed by 10th of billions of informations we collect.

#ASD #AttackSurfaceDiscovery APIs are on their way to general availability.
It will never be as easy to create an asset inventory for any organization attack surface #EASM
Backed by 10th of billions of informations we collect.
👋 In partnership with Signal Spam
#phishing #phishingkit #cybersecurity

👋 In partnership with Signal Spam
#phishing #phishingkit #cybersecurity
In December 2024 you say?
@insikt.bsky.social
Is this not just badcandy again?
because those telcos and universities have been owned for much longer than that via CVE-2023-20198. They just periodically have to recompromise them as they get rebooted.
Also try 50k devices.
CVE-2025-0108: authentication bypass on management interface
search.onyphe.io/search?q=cat...
Thanks to @assetnote.io for having shared the detection method.
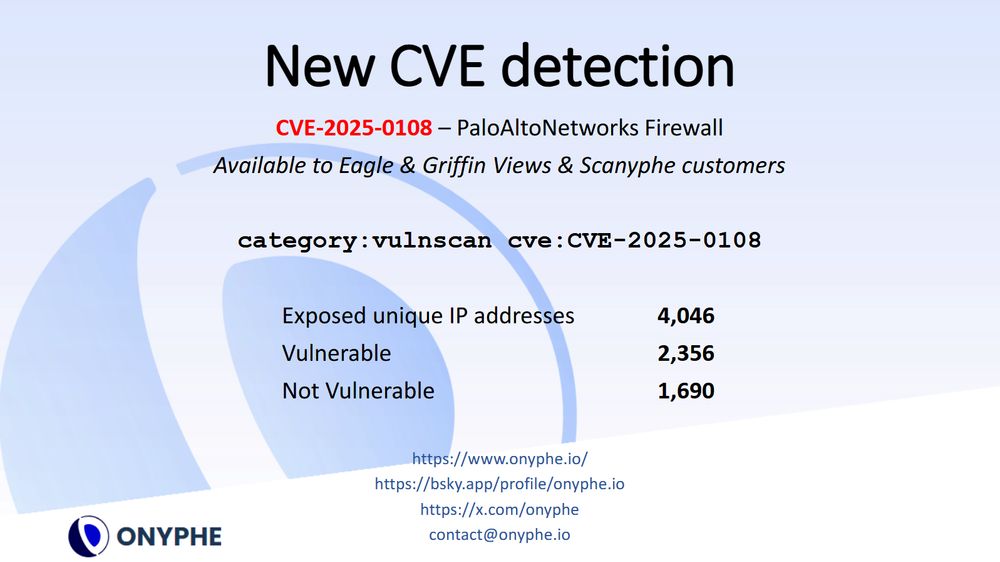
CVE-2025-0108: authentication bypass on management interface
search.onyphe.io/search?q=cat...
Thanks to @assetnote.io for having shared the detection method.
archive.hack.lu/hack-lu-2024...

archive.hack.lu/hack-lu-2024...
👉 Over the last 12 months, we massively increased our visibility of Internet exposed assets. Until now, we focused on #ASM, but this year we will improve our automatic #ASD and expand into the #CTI segment.
Read more: search.onyphe.io/docs/write-u...

👉 Over the last 12 months, we massively increased our visibility of Internet exposed assets. Until now, we focused on #ASM, but this year we will improve our automatic #ASD and expand into the #CTI segment.
Read more: search.onyphe.io/docs/write-u...
there are 2.2M results for Windows RPC boxes
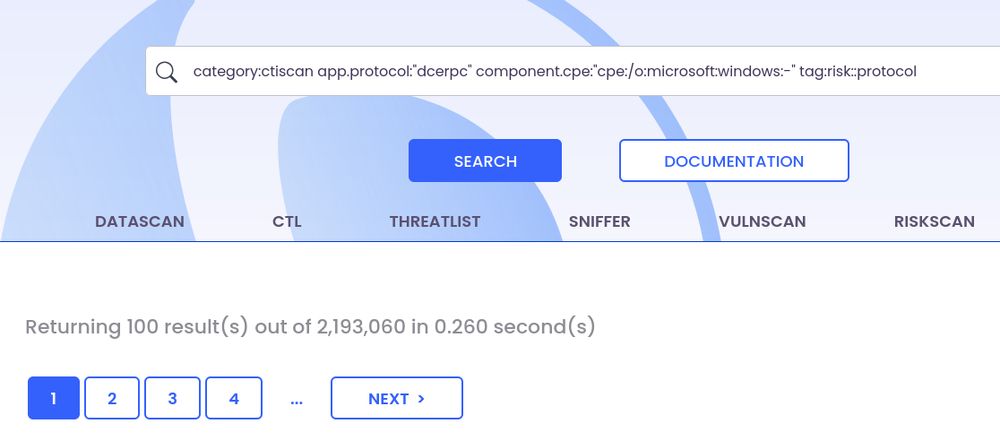
there are 2.2M results for Windows RPC boxes


