
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.

🔗Read the article here: www.proofpoint.com/us/blog/thre...

🔗Read the article here: www.proofpoint.com/us/blog/thre...
This blog details our team's findings: www.proofpoint.com/us/blog/thre....
#malware #ransomware #dataloss

This blog details our team's findings: www.proofpoint.com/us/blog/thre....
#malware #ransomware #dataloss
Hidden in Plain Sight | TA397’s New Attack Chain Delivers Espionage RATs
Report:
www.proofpoint.com/us/blog/thre...

Hidden in Plain Sight | TA397’s New Attack Chain Delivers Espionage RATs
Report:
www.proofpoint.com/us/blog/thre...
🧵⤵️
1) spoofing swisscom (note 'S', domain just reg'd)
2) leveraging encrypted rar + lnk + self signed pdf reader
3) BGP lure (fits with theme of email). BGP is the third leg in the outage triumvirate)


🧵⤵️




Payload delivery URLs:
🌐 urlhaus.abuse.ch/host/95.164....
Payload:
📄 bazaar.abuse.ch/sample/b8794...

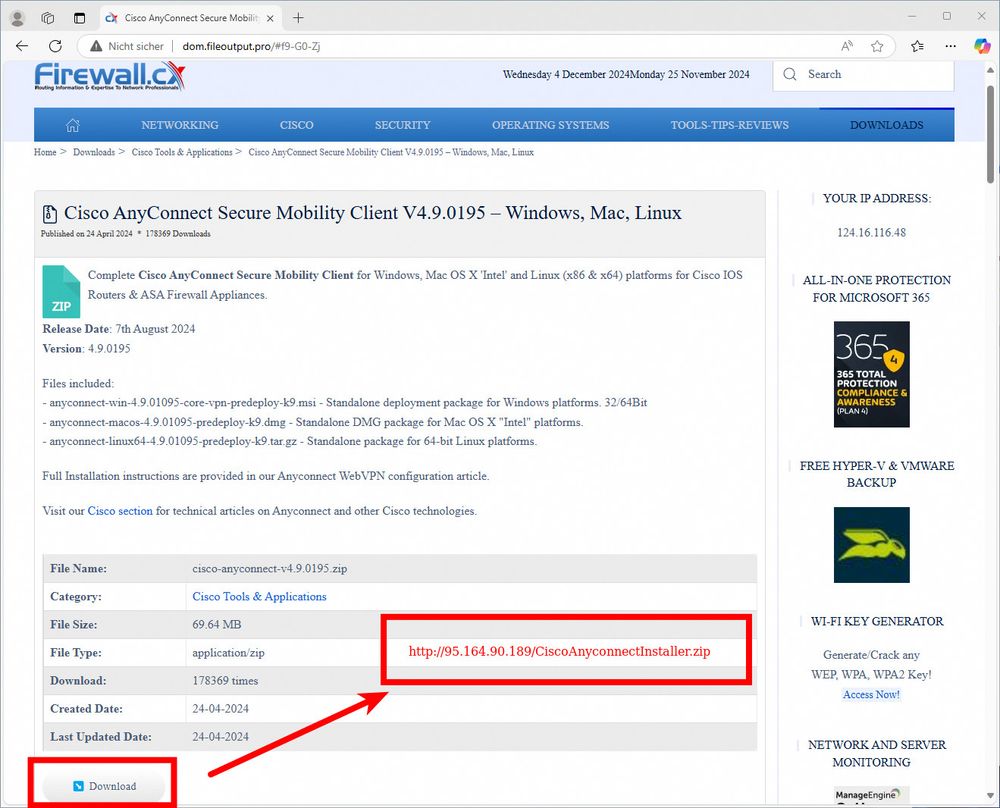
Payload delivery URLs:
🌐 urlhaus.abuse.ch/host/95.164....
Payload:
📄 bazaar.abuse.ch/sample/b8794...
wscript.exe Document-v15-51-07.js
msiexec.exe /I C:\Users\Admin\AppData\Local\Temp\fes.msi
rundll32.exe C:\Users\Admin\AppData\Roaming\avutil.dll, DLLMain
(1/3)👇
IOC's
github.com/pr0xylife/La...

wscript.exe Document-v15-51-07.js
msiexec.exe /I C:\Users\Admin\AppData\Local\Temp\fes.msi
rundll32.exe C:\Users\Admin\AppData\Roaming\avutil.dll, DLLMain
(1/3)👇
IOC's
github.com/pr0xylife/La...
Who’s excited and what will you be working on?
I can’t believe it but I’m excited to write rules for JavaScript 😬😵💫
But also get to show off the new macho module from the one and only
@jacoblatonis.me
Who’s excited and what will you be working on?
I can’t believe it but I’m excited to write rules for JavaScript 😬😵💫
But also get to show off the new macho module from the one and only
@jacoblatonis.me
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine
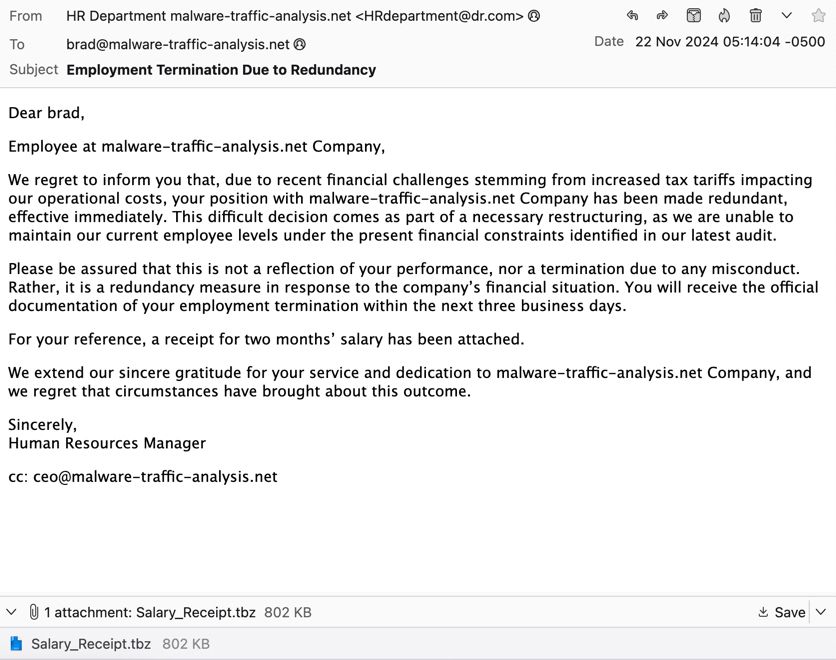
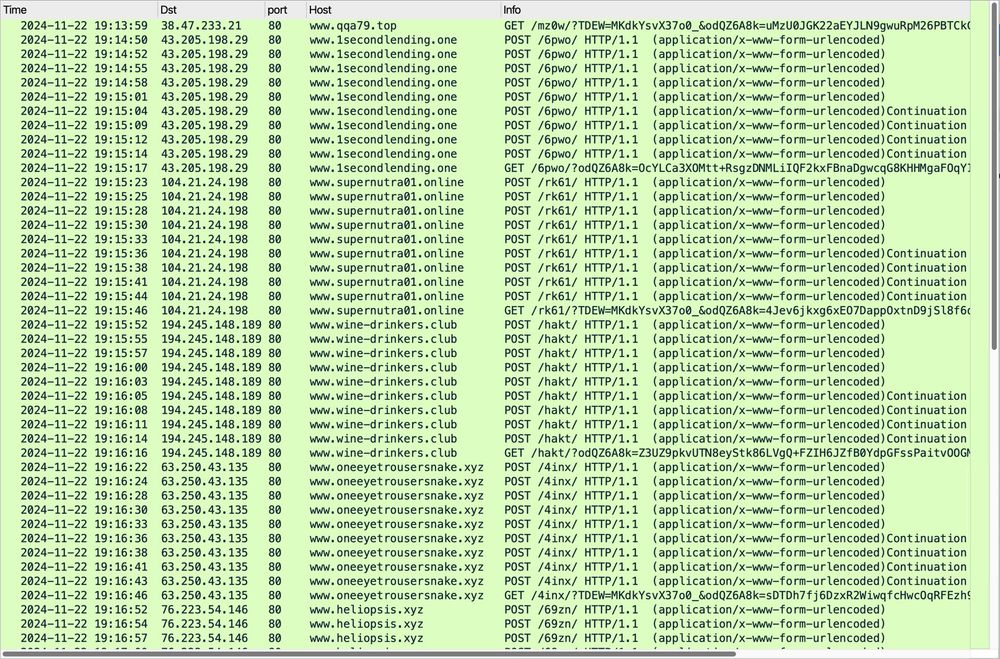
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine

www.proofpoint.com/us/blog/thre...
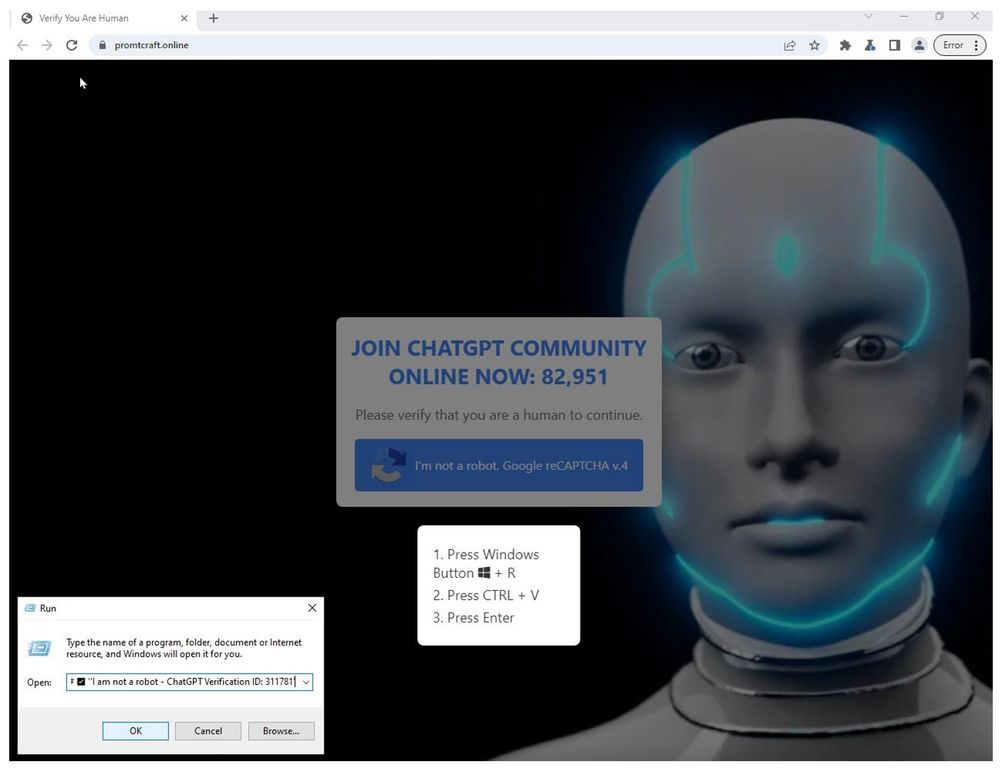
www.proofpoint.com/us/blog/thre...
www.reuters.com/world/biden-...

www.reuters.com/world/biden-...
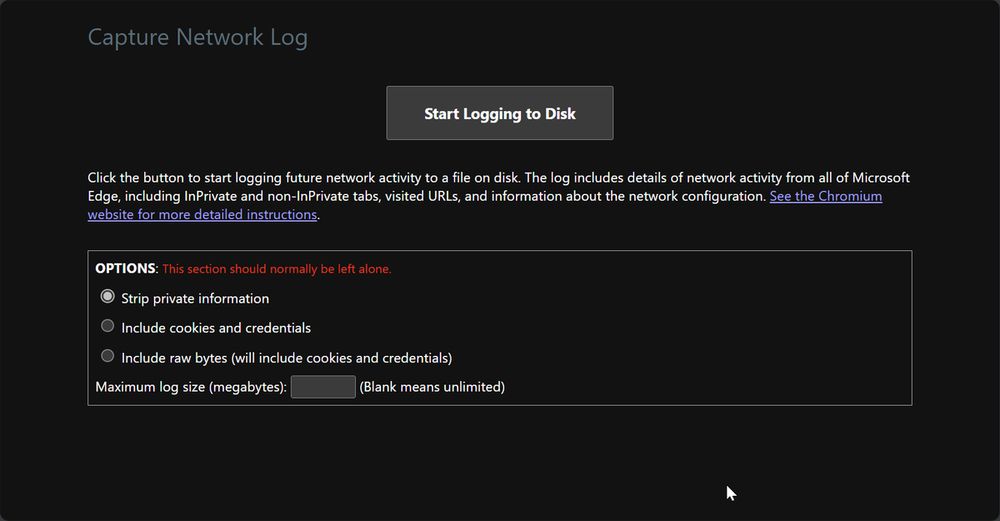
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
Network analyzer: See which accounts people you follow are following, but you don’t. By @theo.io bsky-follow-finder.theo.io
Bluesky Directory: 6,000+ starter packs. By @mubashariqbal.com blueskydirectory.com/starter-pack...
www.youtube.com/watch?v=O69e...

www.youtube.com/watch?v=O69e...
Some recent developments:
1. Now deploying ransomware (had been extorting orgs before)
2. In last few months targeting large/well known enterprises (not just telcos/help desk/crypto orgs)

Some recent developments:
1. Now deploying ransomware (had been extorting orgs before)
2. In last few months targeting large/well known enterprises (not just telcos/help desk/crypto orgs)

