
https://linktr.ee/glennthorpe
I’ll be on a panel “How Do You Define Cybersecurity Experience? A Change in Perspective” where we’ll dig into what really counts as cybersecurity experience
I’ll be on a panel “How Do You Define Cybersecurity Experience? A Change in Perspective” where we’ll dig into what really counts as cybersecurity experience
(Did you know there were four CVEs flipped last week?) #threatintel
We dug through a year of JSON to catch every silent flip and built an RSS feed so you don’t miss the next one.
Read the blog + grab the feed 🗞️

(Did you know there were four CVEs flipped last week?) #threatintel
1/2

1/2

1/2

1/2
I think it turned out pretty well; pardon the disco effect where a stage light was failing :)
www.youtube.com/watc...
CC: @iagox86.bsky.social @greynoise.io

I think it turned out pretty well; pardon the disco effect where a stage light was failing :)
www.youtube.com/watc...
CC: @iagox86.bsky.social @greynoise.io
suricon.net/agenda-m...

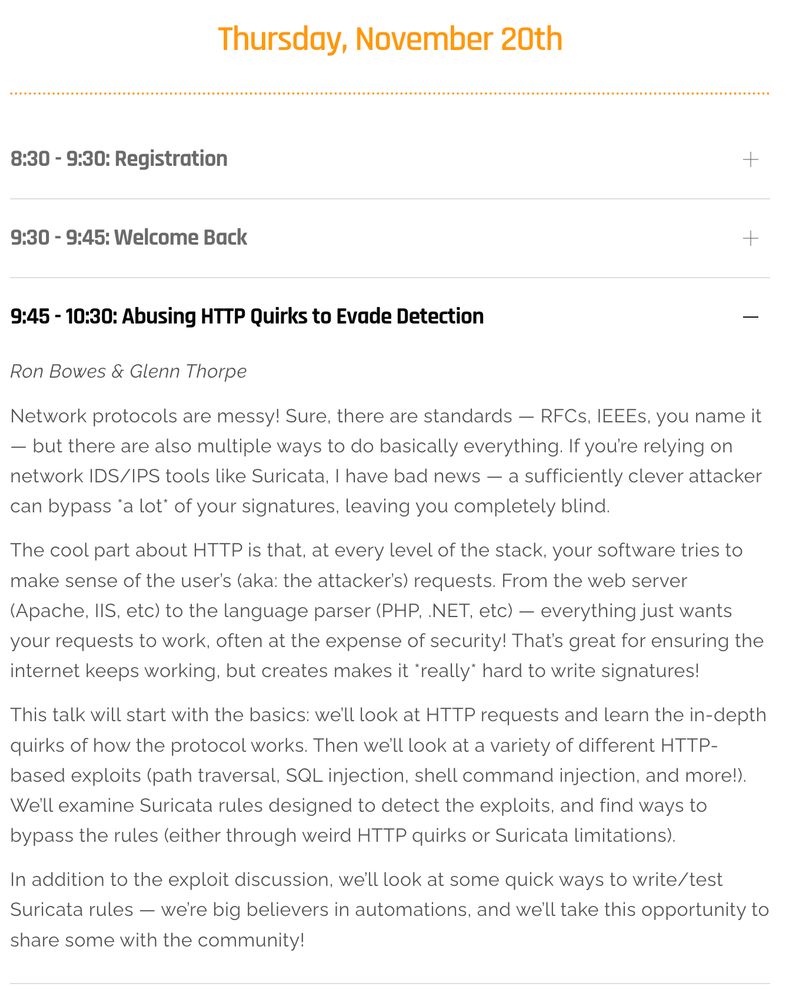
suricon.net/agenda-m...


#Grafana #GreyNoise #ThreatIntel

#Grafana #GreyNoise #ThreatIntel

#Cybersecurity #ThreatIntel #Botnet #VoIP #GreyNoise #Cyber #Tech

#Cybersecurity #ThreatIntel #Botnet #VoIP #GreyNoise #Cyber #Tech
🔥 CVE-2025-49132 (Pterodactyl Panel RCE) (10/10 RCE)
⚡ CVE-2024-20439 (Cisco Smart Licensing Utility) (9.8/10, KEV)
📝 CVE-2017-18370 (Zyxel P660HN)
1/4
🔥 CVE-2025-49132 (Pterodactyl Panel RCE) (10/10 RCE)
⚡ CVE-2024-20439 (Cisco Smart Licensing Utility) (9.8/10, KEV)
📝 CVE-2017-18370 (Zyxel P660HN)
1/4
1/2

1/2
64.176.50[.]109
38.154.237[.]100
102.129.235[.]108
121.237.80[.]241
45.135.232[.]2
Follow along...
1/2
64.176.50[.]109
38.154.237[.]100
102.129.235[.]108
121.237.80[.]241
45.135.232[.]2
Follow along...
1/2
phys.org/news/2025-0...

phys.org/news/2025-0...
#Cybersecurity #ThreatIntel #GreyNoise #ASUS

This works because a funny thing always happens: a random last-minute Zoom will appear if you close it completely.
This works because a funny thing always happens: a random last-minute Zoom will appear if you close it completely.
viz.greynoise.io/tag...

viz.greynoise.io/tag...
TL;DR—They appear to be removing RSS for KEV alerts and moving them to email or X.
They gave orgs 0 days to prepare. RSS is already a thing. The emails arrive many hours later. X is NOT a gov website(!); it even warns you when you click their link!
1/2
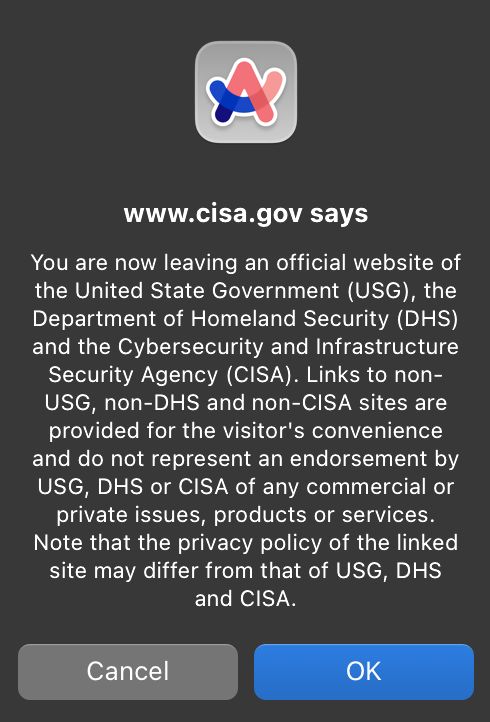
TL;DR—They appear to be removing RSS for KEV alerts and moving them to email or X.
They gave orgs 0 days to prepare. RSS is already a thing. The emails arrive many hours later. X is NOT a gov website(!); it even warns you when you click their link!
1/2
Catch it live Tuesday at 1030 AM ET: stormwatch.ing



