For guidance on how to secure privileged access, see aka.ms/SPA

For guidance on how to secure privileged access, see aka.ms/SPA
(short 🧵 with download link for an open standard at the end)

(short 🧵 with download link for an open standard at the end)
This includes slides from two sessions:
◼️ Security and Zero Trust Body of Knowledge Introduction and Overview
◼️ Security Roles and Glossary Standard Overview and Vision
www.slideshare.net/slideshow/se...
🧵
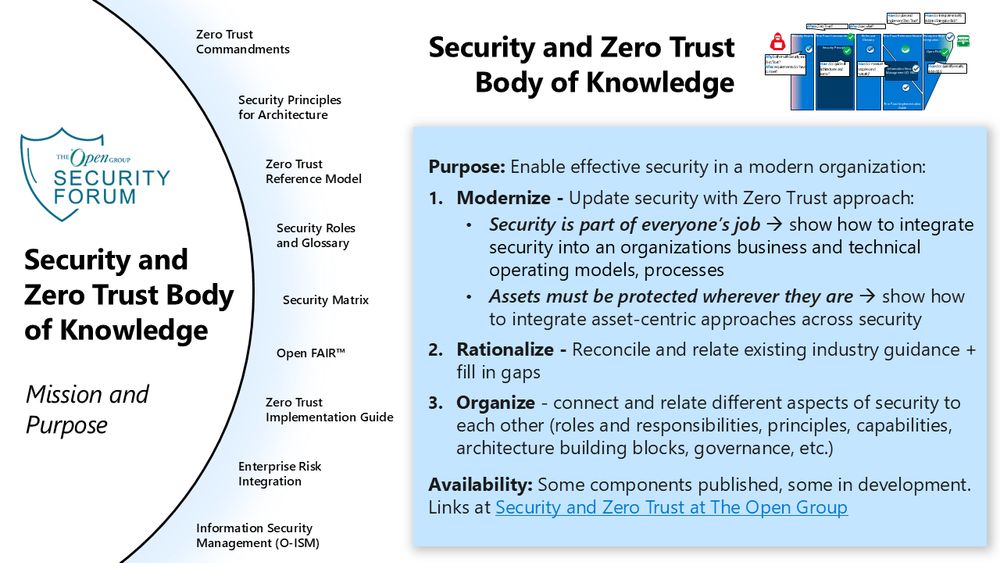
This includes slides from two sessions:
◼️ Security and Zero Trust Body of Knowledge Introduction and Overview
◼️ Security Roles and Glossary Standard Overview and Vision
www.slideshare.net/slideshow/se...
🧵
The greatest obstacle to security success is assuming and expecting that perfect security is possible (or worthwhile to pursue).
(1 of 2)

The greatest obstacle to security success is assuming and expecting that perfect security is possible (or worthwhile to pursue).
(1 of 2)
Worried the problems will come back as soon as you stop investing in security?
You're probably right...
a 🧵

Worried the problems will come back as soon as you stop investing in security?
You're probably right...
a 🧵
If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.

If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.
🔷 If you reward business leaders to ignore cybersecurity, they will.
... a 🧵

🔷 If you reward business leaders to ignore cybersecurity, they will.
... a 🧵
(and yes, there are animations and morph transitions in the downloadable slides - aka.ms/mcra)
🧵

(and yes, there are animations and morph transitions in the downloadable slides - aka.ms/mcra)
🧵
That's what often happens when you don't logs for security:
a 🧵

That's what often happens when you don't logs for security:
a 🧵
Cybersecurity professionals are currently and always will be set up to fail (and blamed for those failures) UNLESS security accountability and responsibility are correctly assigned across business, technology, and security roles
a 🧵

Cybersecurity professionals are currently and always will be set up to fail (and blamed for those failures) UNLESS security accountability and responsibility are correctly assigned across business, technology, and security roles
a 🧵
How to become a trusted advisor instead of being sent to the kids table & ignored while waiting to be blamed/fired at the next incident?
a 🧵

How to become a trusted advisor instead of being sent to the kids table & ignored while waiting to be blamed/fired at the next incident?
a 🧵
a short 🧵

a short 🧵
Building and securing AI Agents is fundamentally different - they are the programs/applications/apps of the AI platform, but managing risk from them is fundamentally different than previous apps because they come with so much functionality.

Building and securing AI Agents is fundamentally different - they are the programs/applications/apps of the AI platform, but managing risk from them is fundamentally different than previous apps because they come with so much functionality.
Check out the Security Roles and Glossary Standard we just published.
www.linkedin.com/pulse/securi...

Check out the Security Roles and Glossary Standard we just published.
www.linkedin.com/pulse/securi...

publications.opengroup.org/s252
publications.opengroup.org/s253
publications.opengroup.org/s254
publications.opengroup.org/s255
short 🧵with key points...

publications.opengroup.org/s252
publications.opengroup.org/s253
publications.opengroup.org/s254
publications.opengroup.org/s255
short 🧵with key points...
I highly recommend taking a quick look through it as there is a lot of security news and releases (keyword search had 172 hits on the word security 🙂)
news.microsoft.com/ignite-2025-...

I highly recommend taking a quick look through it as there is a lot of security news and releases (keyword search had 172 hits on the word security 🙂)
news.microsoft.com/ignite-2025-...
I pretty much stop listening after I hear "This attack would have been stopped by..."
short 🧵(rant)

I pretty much stop listening after I hear "This attack would have been stopped by..."
short 🧵(rant)
Most people in a security team should be interacting with non-security people across technology and business teams.

Most people in a security team should be interacting with non-security people across technology and business teams.

(see? standards people have a sense of humor as well 😀)
For more on roles and glossary standard (and others in this body of knowledge), see lnkd.in/gyd-3T39

(see? standards people have a sense of humor as well 😀)
For more on roles and glossary standard (and others in this body of knowledge), see lnkd.in/gyd-3T39
Everything in security is about removing the cheap, easy, and reliable options from the threat actor menu.
Everything in security is about removing the cheap, easy, and reliable options from the threat actor menu.
short 🧵 with some updates and insights
short 🧵 with some updates and insights
This post is a bit pedantic, but I have a reason for the details so bear with me :-)
a 🧵

This post is a bit pedantic, but I have a reason for the details so bear with me :-)
a 🧵

