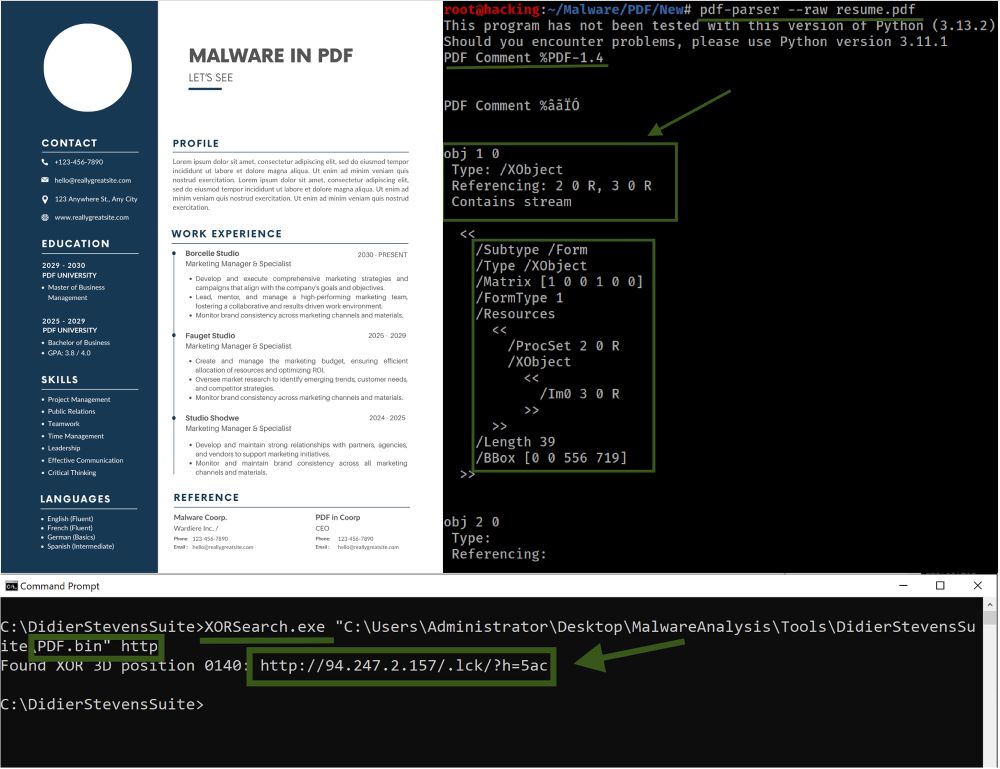
Today's story is a long overdue series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it’s time […]
[Original post on infosec.exchange]

Today's story is a long overdue series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it’s time […]
[Original post on infosec.exchange]
thespanner.co.uk/autovader

thespanner.co.uk/autovader
When asked, Grok was willing to provide step-by-step instructions on how to stalk these people...
Read more in my article on the Bitdefender blog: www.bitdefender.com/en-us/blog/h...

When asked, Grok was willing to provide step-by-step instructions on how to stalk these people...
Read more in my article on the Bitdefender blog: www.bitdefender.com/en-us/blog/h...

owasp.org/Top10/2025/0...
owasp.org/Top10/2025/0...
IP data on exposed instances is in our Device ID report: www.shadowserver.org/what-we-do/n... (device model is set to FortiWeb Management Interface)
IP data on exposed instances is in our Device ID report: www.shadowserver.org/what-we-do/n... (device model is set to FortiWeb Management Interface)

github.com/random-robbi...
github.com/random-robbi...

Corellium's founder Chris Wade also purchased them back in the day, according to sources.
www.vice.com/en/article/t...

Corellium's founder Chris Wade also purchased them back in the day, according to sources.
www.vice.com/en/article/t...
portswigger.net/web-security...
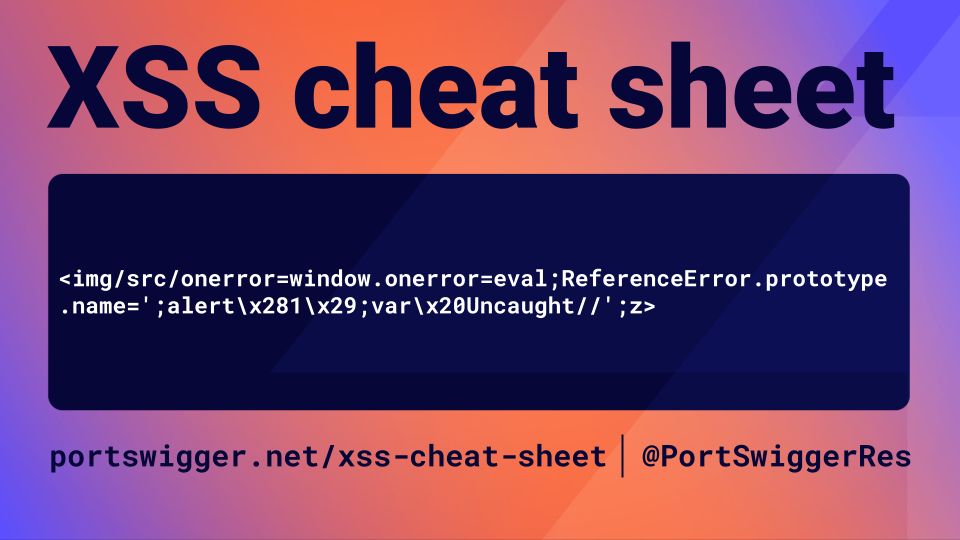
portswigger.net/web-security...