
dMSA abuse is still a problem, and @logangoins.bsky.social
just dropped a reality check with new tooling to prove it.
Learn more about the issue & the new BadTakeover BOF. ghst.ly/42POg9L

dMSA abuse is still a problem, and @logangoins.bsky.social
just dropped a reality check with new tooling to prove it.
Learn more about the issue & the new BadTakeover BOF. ghst.ly/42POg9L

Over the last year, stealing cookies on Windows devices has changed significantly for Chromium browsers like Chrome and Edge. Andrew Gomez dives into these changes, how threat actors adapt, & new detection opportunities. ghst.ly/45S1ZgW

Over the last year, stealing cookies on Windows devices has changed significantly for Chromium browsers like Chrome and Edge. Andrew Gomez dives into these changes, how threat actors adapt, & new detection opportunities. ghst.ly/45S1ZgW

github.com/olafhartong/...
Slides available here:
github.com/olafhartong/...
github.com/olafhartong/...
Slides available here:
github.com/olafhartong/...
This disables cloud delivered protection which underpins a bunch of capabilities, disables roughly half of your protection
Fortunately, if you enable Tamper Protection, it is forcefully enabled for you :)

This disables cloud delivered protection which underpins a bunch of capabilities, disables roughly half of your protection
Fortunately, if you enable Tamper Protection, it is forcefully enabled for you :)
Microsoft has released the new advanced hunting table "GraphAPIAuditEvents" which offers great opportunities to investigate activities based on #MicrosoftGraph API calls.
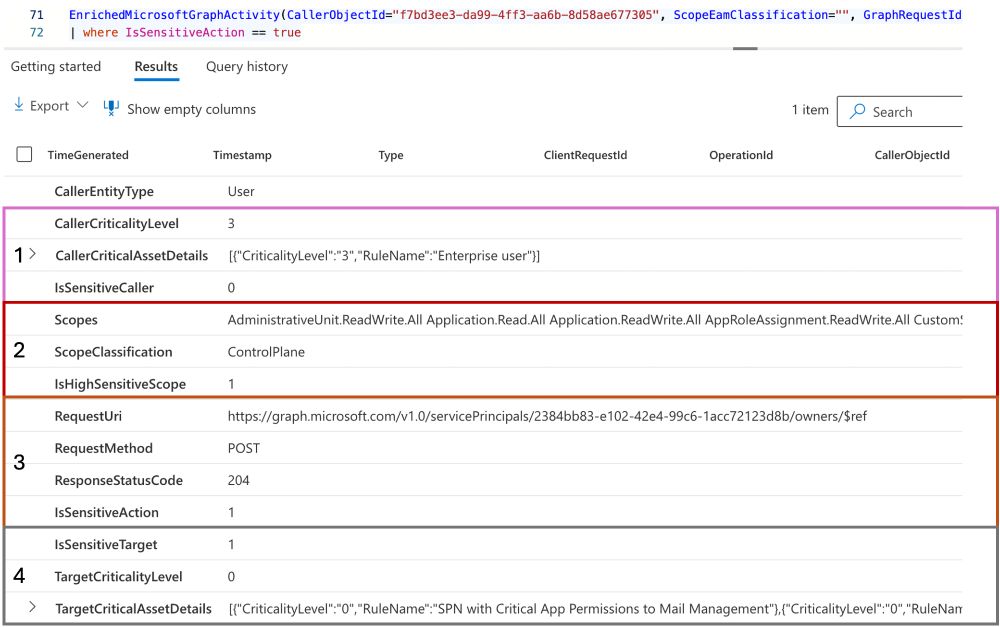
Microsoft has released the new advanced hunting table "GraphAPIAuditEvents" which offers great opportunities to investigate activities based on #MicrosoftGraph API calls.
Kicking off his blog series, Diego Lomellini uses Micrograd to explain core ML concepts like supervised learning, regression, classification, loss functions, & gradient descent. ghst.ly/44n3IeJ

Kicking off his blog series, Diego Lomellini uses Micrograd to explain core ML concepts like supervised learning, regression, classification, loss functions, & gradient descent. ghst.ly/44n3IeJ
Check out @jonas-bk.bsky.social's blog post to learn more. ghst.ly/4lj9C5T

Check out @jonas-bk.bsky.social's blog post to learn more. ghst.ly/4lj9C5T
@subat0mik.bsky.social & @unsignedsh0rt.bsky.social dive into the research & its impact on the state of SCCM security. Read more: ghst.ly/460vI9d

@subat0mik.bsky.social & @unsignedsh0rt.bsky.social dive into the research & its impact on the state of SCCM security. Read more: ghst.ly/460vI9d
@xpnsec.com covers the architecture, access controls, and why some legacy UAC bypass techniques remain effective in his latest blog post. ghst.ly/44mw5JM

@xpnsec.com covers the architecture, access controls, and why some legacy UAC bypass techniques remain effective in his latest blog post. ghst.ly/44mw5JM

- restricted permissions on Directory Synchronization Accounts role
- new dedicated sync app
Let’s find out how sync still works 🔍
Some old tricks persist—and new ones have emerged 💥
tenable.com/blog/despite... 🧵

- restricted permissions on Directory Synchronization Accounts role
- new dedicated sync app
Let’s find out how sync still works 🔍
Some old tricks persist—and new ones have emerged 💥
tenable.com/blog/despite... 🧵
I tried really hard to make this as short and simple as possible. Please be nice to your IR folks and set this up, it's important ;)
nathanmcnulty.com/bl...

I tried really hard to make this as short and simple as possible. Please be nice to your IR folks and set this up, it's important ;)
nathanmcnulty.com/bl...


Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
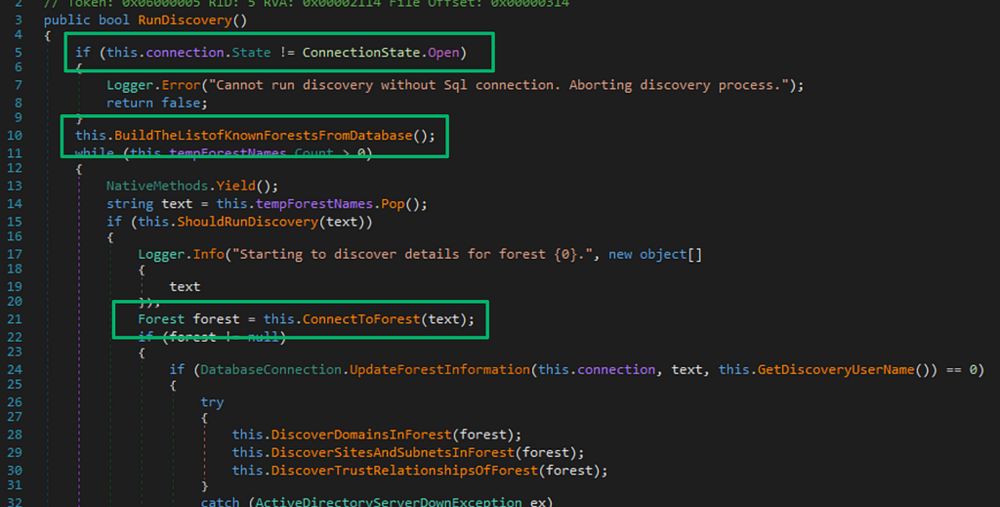
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp


