🎤 @kevintell.bsky.social delivered a session exploring advanced Red Team lateral movement techniques built on DCOM - a great opportunity to exchange practices with fellow experts.
Thank you to the @oenb.at for hosting such a great event!

🎤 @kevintell.bsky.social delivered a session exploring advanced Red Team lateral movement techniques built on DCOM - a great opportunity to exchange practices with fellow experts.
Thank you to the @oenb.at for hosting such a great event!
👉 Watch the whole show: video.lefigaro.fr/figaro/econo...

👉 Watch the whole show: video.lefigaro.fr/figaro/econo...
Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm
Our ninja, Riadh Bouchahoua, uncovers how attackers can exploit Chromium extension loading to steal data, maintain persistent access, and breach confidentiality on Chromium-based browsers.
Read more here ⬇️
www.synacktiv.com/en/publicati...

Our ninja, Riadh Bouchahoua, uncovers how attackers can exploit Chromium extension loading to steal data, maintain persistent access, and breach confidentiality on Chromium-based browsers.
Read more here ⬇️
www.synacktiv.com/en/publicati...
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG

@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
🔗 Entry: www.synacktiv.com/en/offers/tr...
🔗 Advanced: www.synacktiv.com/en/offers/tr...


🔗 Entry: www.synacktiv.com/en/offers/tr...
🔗 Advanced: www.synacktiv.com/en/offers/tr...
www.synacktiv.com/en/publicati...

www.synacktiv.com/en/publicati...


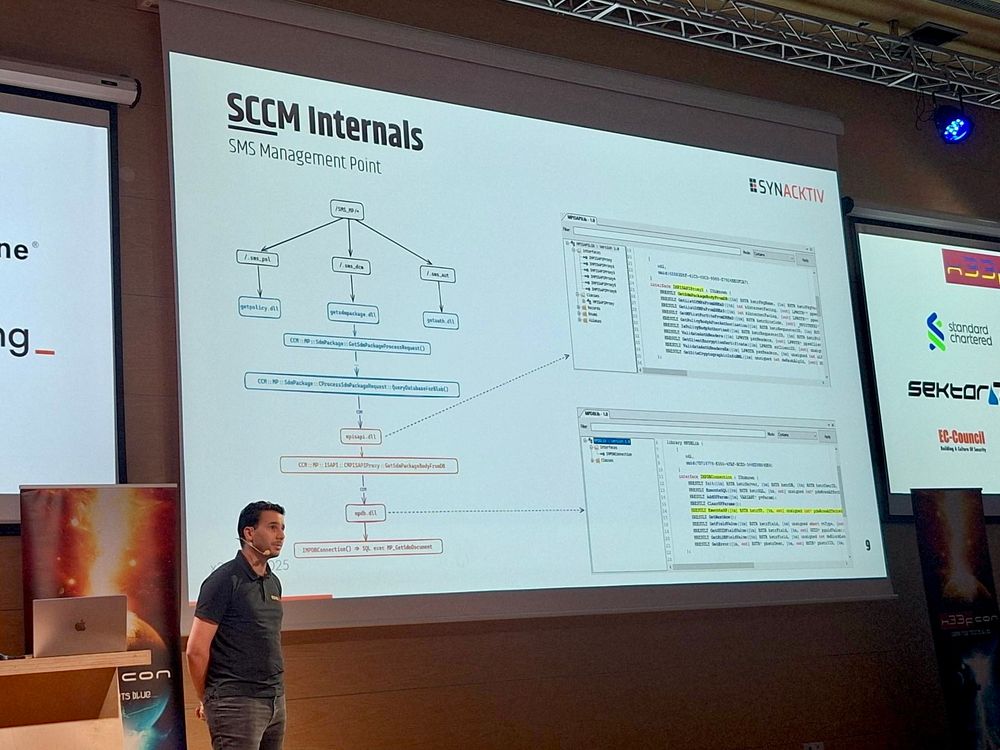

decoder.cloud/2025/04/24/f...
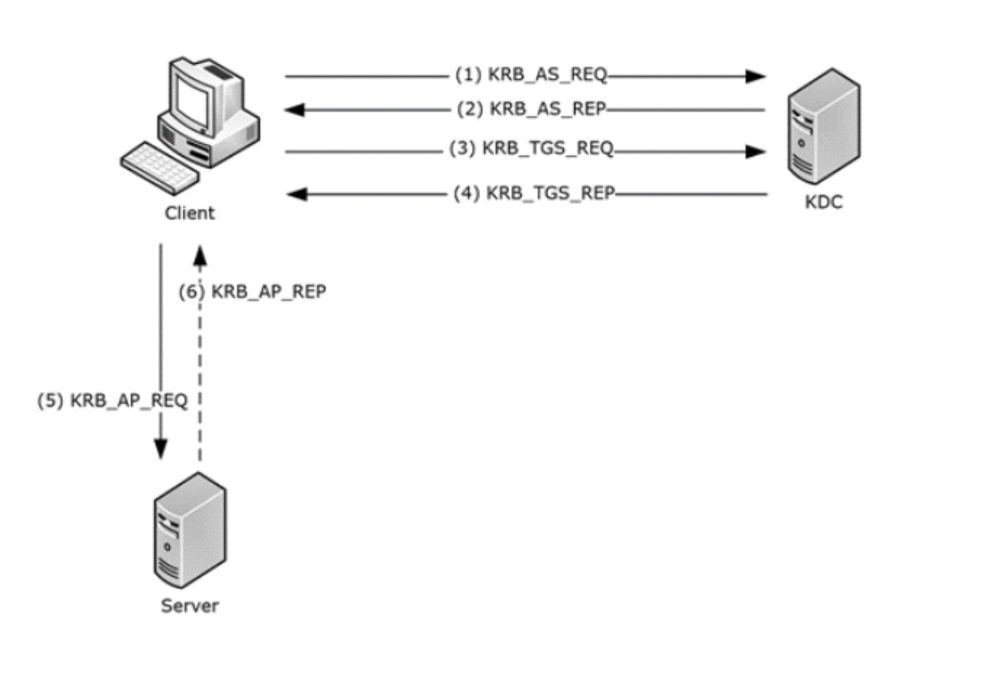
decoder.cloud/2025/04/24/f...




Find out if you are a good candidate by reading our offer (🇫🇷).
www.synacktiv.com/responsable-...
Find out if you are a good candidate by reading our offer (🇫🇷).
www.synacktiv.com/responsable-...
Join us this summer at @blackhatevents.bsky.social in Vegas for a deep dive into red teaming on Azure, M365, Azure DevOps, and hybrid infrastructures.
Early bird tickets available until May 23rd!
www.blackhat.com/us-25/traini...
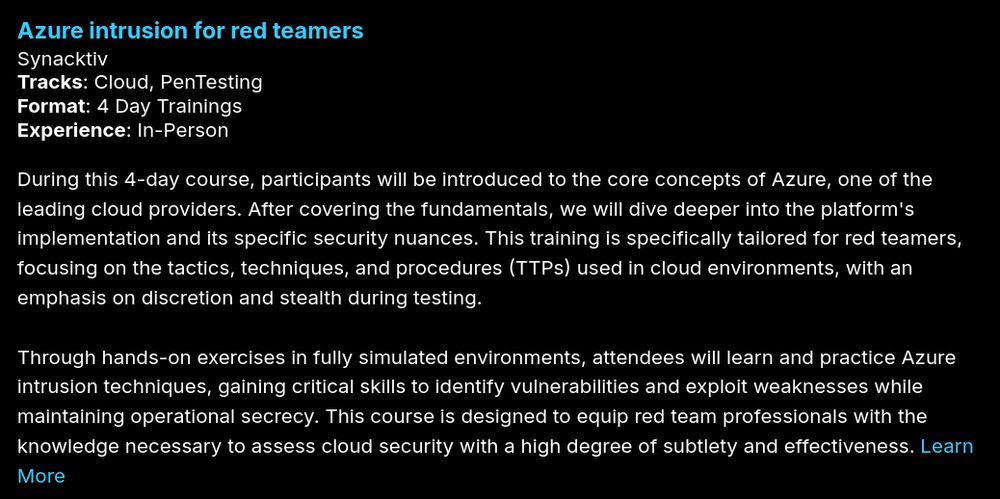
www.synacktiv.com/publications...
www.synacktiv.com/publications...