working on malware analysis and reverse engineering. dtrsec.com
www.youtube.com/watch?v=iChO...

www.youtube.com/watch?v=iChO...
www.youtube.com/watch?v=mQI1...

www.youtube.com/watch?v=mQI1...
www.youtube.com/watch?v=jmyV...

www.youtube.com/watch?v=jmyV...
www.youtube.com/watch?v=MdKh...

www.youtube.com/watch?v=MdKh...
www.youtube.com/watch?v=9Xrn...

www.youtube.com/watch?v=9Xrn...
www.youtube.com/watch?v=n4mT...

www.youtube.com/watch?v=n4mT...
www.youtube.com/watch?v=3Cof...

www.youtube.com/watch?v=3Cof...
www.youtube.com/watch?v=Yu4v...

www.youtube.com/watch?v=Yu4v...
www.youtube.com/watch?v=giEs...

www.youtube.com/watch?v=giEs...
www.youtube.com/watch?v=44Ne...

www.youtube.com/watch?v=44Ne...
www.youtube.com/watch?v=QxEn...

www.youtube.com/watch?v=QxEn...
Now you can run Python-based playbooks to automate security operations, enhance detections, and streamline workflows!
Check out what's possible: limacharlie.io/blog/playboo...

Now you can run Python-based playbooks to automate security operations, enhance detections, and streamline workflows!
Check out what's possible: limacharlie.io/blog/playboo...
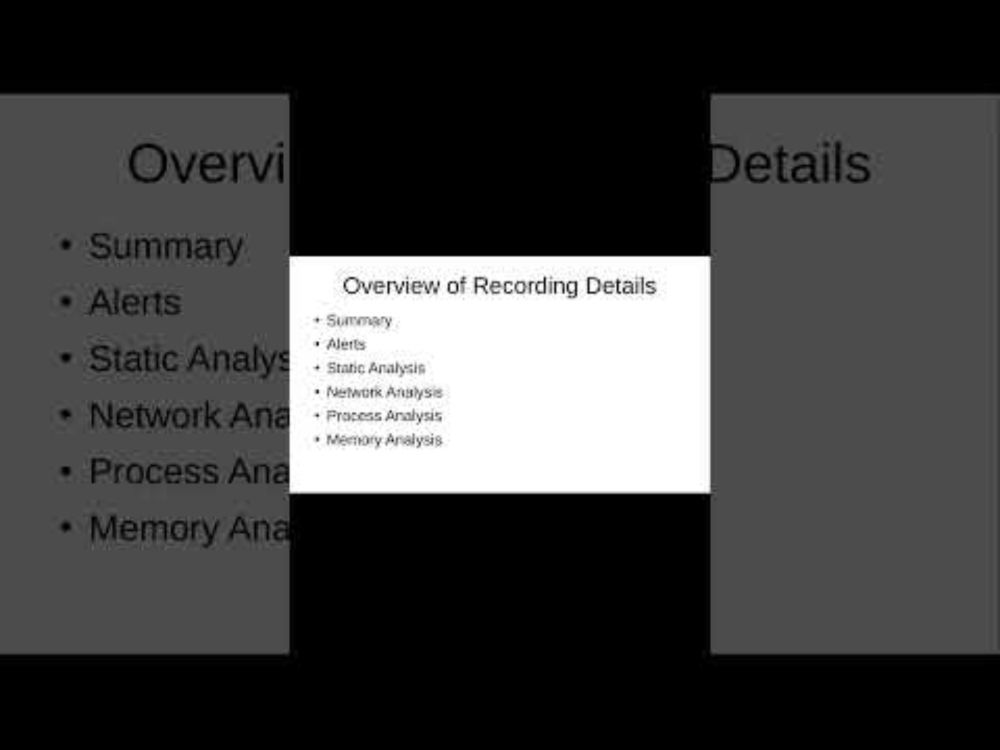
This video is an overview of process details, including command line arguments, network activity, file system activity (including downloading/viewing created files), and registry activity.
www.youtube.com/watch?v=6M2o...

This video is an overview of process details, including command line arguments, network activity, file system activity (including downloading/viewing created files), and registry activity.
www.youtube.com/watch?v=6M2o...
youtube.com/shorts/Y5K1T...
#malware #phishing #cybersecurity #browser #reverseengineering #sandbox
youtube.com/shorts/Y5K1T...
#malware #phishing #cybersecurity #browser #reverseengineering #sandbox
www.youtube.com/shorts/Y5K1T...
#malware #phishing #cybersecurity #browser #reverseengineering #sandbox

www.youtube.com/shorts/Y5K1T...
#malware #phishing #cybersecurity #browser #reverseengineering #sandbox
www.youtube.com/watch?v=cKtF...

www.youtube.com/watch?v=cKtF...
github.com/st0pp3r/awes...
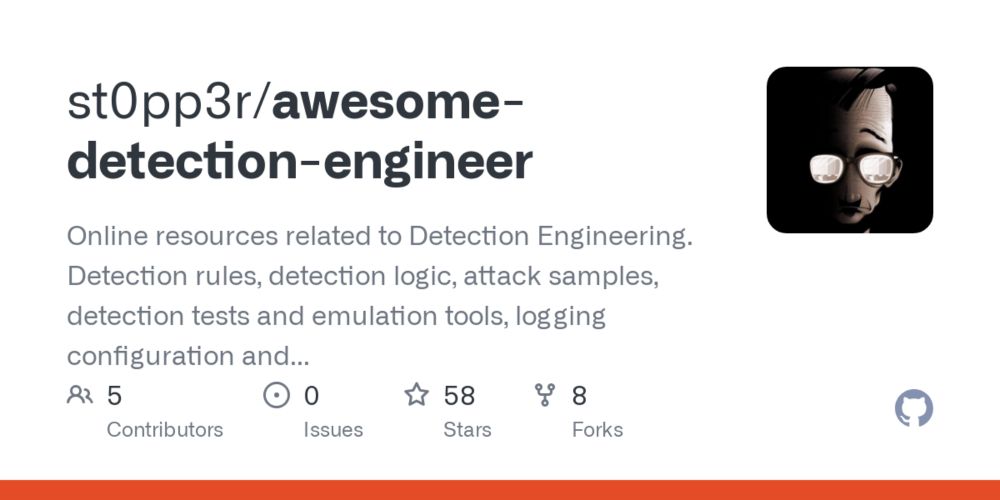
github.com/st0pp3r/awes...
Check them out over at dtrsec.com
Here's a cool breakdown of their tool, REnigma: https://buff.ly/4jTzsO4

Check them out over at dtrsec.com
Here's a cool breakdown of their tool, REnigma: https://buff.ly/4jTzsO4
www.youtube.com/watch?v=Nw5o...
www.youtube.com/watch?v=Nw5o...
limacharlie.io/defender-fri...
#infosec
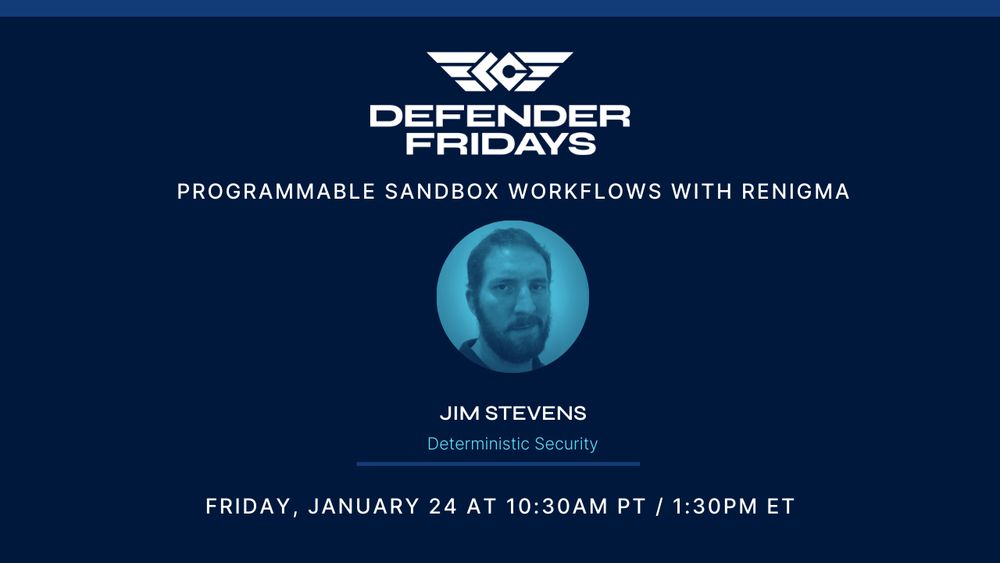
limacharlie.io/defender-fri...
#infosec
www.youtube.com/watch?v=7iIo...
www.youtube.com/watch?v=7iIo...
www.youtube.com/watch?v=TGr8...

www.youtube.com/watch?v=TGr8...
MSSN CTRL 2024 talk we did on how to analyze malware with a programmable sandbox. It includes a demo of REnigma's backtracker going backwards in time to find TLS plaintext from encrypted bytes sent to network interface memory mapped IO writes.
limacharlie.io/events/mssn-...

MSSN CTRL 2024 talk we did on how to analyze malware with a programmable sandbox. It includes a demo of REnigma's backtracker going backwards in time to find TLS plaintext from encrypted bytes sent to network interface memory mapped IO writes.
limacharlie.io/events/mssn-...


