
Cyber Security Engineer interested in Pentesting | Cloud Security | Adversary Emulation | Threat Hunting | Purple Teaming | Bug Bounties | SecDevOps
In my latest blog, I walk through how an attacker could abuse AWS CodeBuild + GitHub Actions to maintain long-term access in a compromised AWS account:
medium.com/@adan.alvare...

In my latest blog, I walk through how an attacker could abuse AWS CodeBuild + GitHub Actions to maintain long-term access in a compromised AWS account:
medium.com/@adan.alvare...

x.com/safe/status/...

x.com/safe/status/...
When an attacker gets access to your account, it is just the beginning of the game, not the end.
In my latest article, I explain how we can rig the game to stop attackers before real damage happens.
🔗Read here: medium.com/@adan.alvare... #CyberSecurity #AWS #CloudSecurity

When an attacker gets access to your account, it is just the beginning of the game, not the end.
In my latest article, I explain how we can rig the game to stop attackers before real damage happens.
🔗Read here: medium.com/@adan.alvare... #CyberSecurity #AWS #CloudSecurity

IBAN for donations is available here:
www.ccc.de/en/updates/2...
Talks for context
media.ccc.de/v/37c3-12142...
streaming.media.ccc.de/38c3/relive/...
IBAN for donations is available here:
www.ccc.de/en/updates/2...
Talks for context
media.ccc.de/v/37c3-12142...
streaming.media.ccc.de/38c3/relive/...

➔ Use GetFederationToken to generate temporary credentials
➔ Use SendSerialConsoleSSHPublicKey to pivot to EC2 instances
github.com/DataDog/stra...
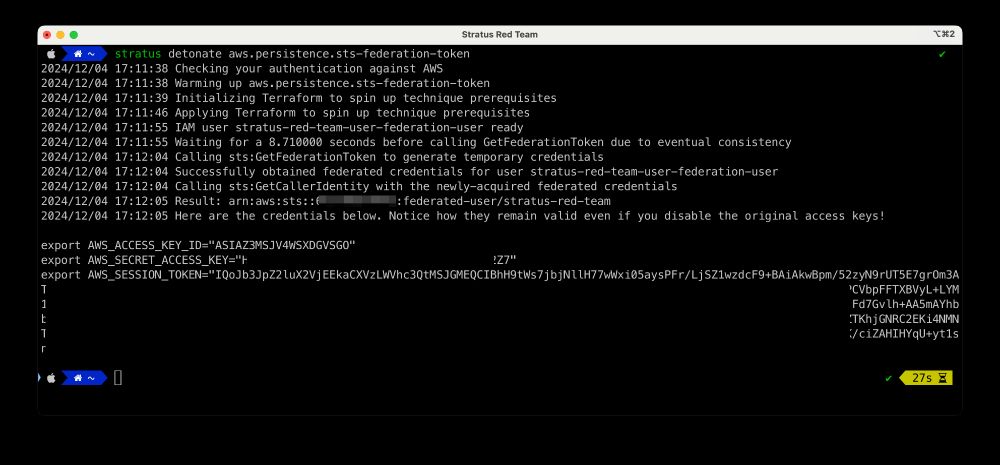

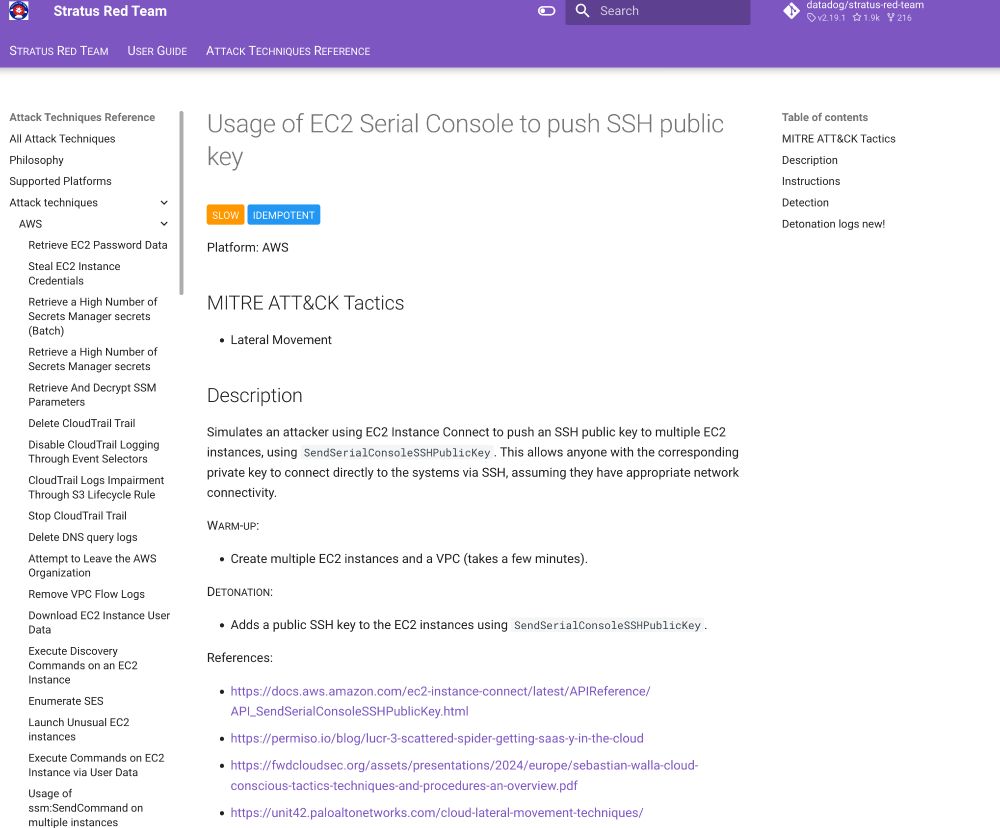
go.bsky.app/8XpcFm5
go.bsky.app/8XpcFm5


