Russia-linked APT InedibleOchotense impersonates ESET to deploy backdoor on Ukrainian systems
Russia-linked group InedibleOchotense used fake ESET installers in phishing attacks on Ukrainian targets in May 2025. Russia-linked group InedibleOchotense used trojanized ESET installer…
#hackernews #news
Russia-linked group InedibleOchotense used fake ESET installers in phishing attacks on Ukrainian targets in May 2025. Russia-linked group InedibleOchotense used trojanized ESET installer…
#hackernews #news

Russia-linked APT InedibleOchotense impersonates ESET to deploy backdoor on Ukrainian systems
Russia-linked group InedibleOchotense used fake ESET installers in phishing attacks on Ukrainian targets in May 2025. Russia-linked group InedibleOchotense used trojanized ESET installers in phishing attacks against Ukrainian entities detected in May 2025. The campaign used emails and Signal messages to deliver trojanized ESET installers that installed both legitimate software and the Kalambur backdoor. “Another […]
securityaffairs.com
November 8, 2025 at 6:14 AM
Russia-linked APT InedibleOchotense impersonates ESET to deploy backdoor on Ukrainian systems
Russia-linked group InedibleOchotense used fake ESET installers in phishing attacks on Ukrainian targets in May 2025. Russia-linked group InedibleOchotense used trojanized ESET installer…
#hackernews #news
Russia-linked group InedibleOchotense used fake ESET installers in phishing attacks on Ukrainian targets in May 2025. Russia-linked group InedibleOchotense used trojanized ESET installer…
#hackernews #news
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May …
#hackernews #news
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May …
#hackernews #news

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May 2025, is tracked by the security outfit under the moniker InedibleOchotense, describing it as Russia-aligned.
"InedibleOchotense sent spear-phishing emails and Signal text messages, containing a link
thehackernews.com
November 7, 2025 at 2:48 PM
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May …
#hackernews #news
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May …
#hackernews #news
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine reconbee.com/trojanized-e...
#Trojanized #ESET #kalamburbackdoor #phishingattacks #phishingawareness #cyberattack
#Trojanized #ESET #kalamburbackdoor #phishingattacks #phishingawareness #cyberattack

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
introduction of a backdoor dubbed BACKORDER read more about Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
reconbee.com
November 7, 2025 at 2:14 PM
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine reconbee.com/trojanized-e...
#Trojanized #ESET #kalamburbackdoor #phishingattacks #phishingawareness #cyberattack
#Trojanized #ESET #kalamburbackdoor #phishingattacks #phishingawareness #cyberattack
MUT-4831: Trojanized npm packages deliver Vidar infostealer malware #malware
MUT-4831: Trojanized npm packages deliver Vidar infostealer malware
Eyal Estrin
unread,
11:11 PM (25 minutes ago)
to
https://securitylabs.datadoghq.com/articles/mut-4831-trojanized-npm-packages-vidar/
Eyal Estrin
CISSP, CCSP, CISM, CISA, CDPSE, CCSK
Blog: https://security-24-7.com | Books: https://amzn.to/42Xai9A | https://amzn.to/3Sggbtv
Twitter: @eyalestrin | Bluesky: @eyalestrin.bsky.social
groups.google.com
November 7, 2025 at 7:36 AM
MUT-4831: Trojanized npm packages deliver Vidar infostealer malware #malware
iT4iNT SERVER Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine VDS VPS Cloud #CyberSecurity #Phishing #Malware #ESET #Ukraine

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities.
The campaign, detected in May 2025, is tracked by the security outfit under the moniker InedibleOchotense, describing it as Russia-aligned.
"InedibleOchotense sent spear-phishing emails and Signal text messages, containing a link
dlvr.it
November 6, 2025 at 4:54 PM
iT4iNT SERVER Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine VDS VPS Cloud #CyberSecurity #Phishing #Malware #ESET #Ukraine
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
#thehackersnews
#thehackersnews

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine | Read more hacking news on The Hacker News cybersecurity news website and learn how to protect against cyberattacks and software vulnerabilities.
thehackernews.com
November 6, 2025 at 4:30 PM
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
#thehackersnews
#thehackersnews
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
thehackernews.com
November 6, 2025 at 4:15 PM
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine #cybersecurity #hacking #news #infosec #security #technology #privacy thehackernews.com/20...

November 6, 2025 at 4:04 PM
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine #cybersecurity #hacking #news #infosec #security #technology #privacy thehackernews.com/20...
New alert on Bluesky! Trojanized ESET Installers in Ukraine phishing attacks. #Cybersecurity, stay vigilant.
November 6, 2025 at 3:55 PM
New alert on Bluesky! Trojanized ESET Installers in Ukraine phishing attacks. #Cybersecurity, stay vigilant.
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine Tech-Wire - Stay Updated with insights, trends, news and opinions on Technology, Digital Marketing, Education, and H...
#Cyber #Security
Origin | Interest | Match
#Cyber #Security
Origin | Interest | Match

Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities. The campaign, detected in May 2025, is tracked by the security outfit under the moniker InedibleOchotense, describing it as Russia-aligned. "InedibleOchotense sent spear-phishing emails and Signal text messages, containing a link to a trojanized ESET installer, to multiple Ukrainian entities," ESET said in its APT Activity Report Q2 2025–Q3 2025 shared with The Hacker News. InedibleOchotense is assessed to share tactical overlaps with a campaign documented by EclecticIQ that involved the deployment of a backdoor called BACKORDER and by CERT-UA as UAC-0212, which it describes as a sub-cluster within the Sandworm (aka APT44) hacking group. While the email message is written in Ukrainian, ESET said the first line uses a Russian word, likel..
tech-wire.in
November 6, 2025 at 6:06 PM
Originally from DataDog: MUT-4831: Trojanized npm packages deliver Vidar infostealer malware ( :-{ı▓ #cloudsecurity #datadog #cyberresearch

MUT-4831: Trojanized npm packages deliver Vidar infostealer malware
Analysis of a threat actor campaign targeting Windows users with Vidar infostealer malware via malicious npm packages
securitylabs.datadoghq.com
November 6, 2025 at 1:20 PM
Originally from DataDog: MUT-4831: Trojanized npm packages deliver Vidar infostealer malware ( :-{ı▓ #cloudsecurity #datadog #cyberresearch
MUT-4831: Trojanized npm packages deliver Vidar infostealer malware
securitylabs.datadoghq.com/articles/mut...
securitylabs.datadoghq.com/articles/mut...

MUT-4831: Trojanized npm packages deliver Vidar infostealer malware | Datadog Security Labs
Analysis of a threat actor campaign targeting Windows users with Vidar infostealer malware via malicious npm packages
securitylabs.datadoghq.com
November 6, 2025 at 10:57 AM
MUT-4831: Trojanized npm packages deliver Vidar infostealer malware
securitylabs.datadoghq.com/articles/mut...
securitylabs.datadoghq.com/articles/mut...
🚨 Malicious VS Code extension 'SleepyDuck' found in Open VSX! 🦆 The RAT uses an Ethereum smart contract for a resilient C2 infrastructure. Targets developers via a trojanized Solidity extension. #Malware #SupplyChain #Crypto #DevSecOps
"SleepyDuck" RAT Emerges in Open VSX Marketplace via Malicious Update
A new RAT named SleepyDuck has been found in a malicious extension in the Open VSX marketplace, using an Ethereum smart contract for a resilient command-and-control (C2) mechanism to target developers.
cyber.netsecops.io
November 4, 2025 at 5:53 PM
🚨 Malicious VS Code extension 'SleepyDuck' found in Open VSX! 🦆 The RAT uses an Ethereum smart contract for a resilient C2 infrastructure. Targets developers via a trojanized Solidity extension. #Malware #SupplyChain #Crypto #DevSecOps
so, apparently, some 90's motherboards using American Megatrends' BIOS had a "trojanized" BIOS which played happy birthday on november 13th. and I could NOT find any information on why or how this has happened
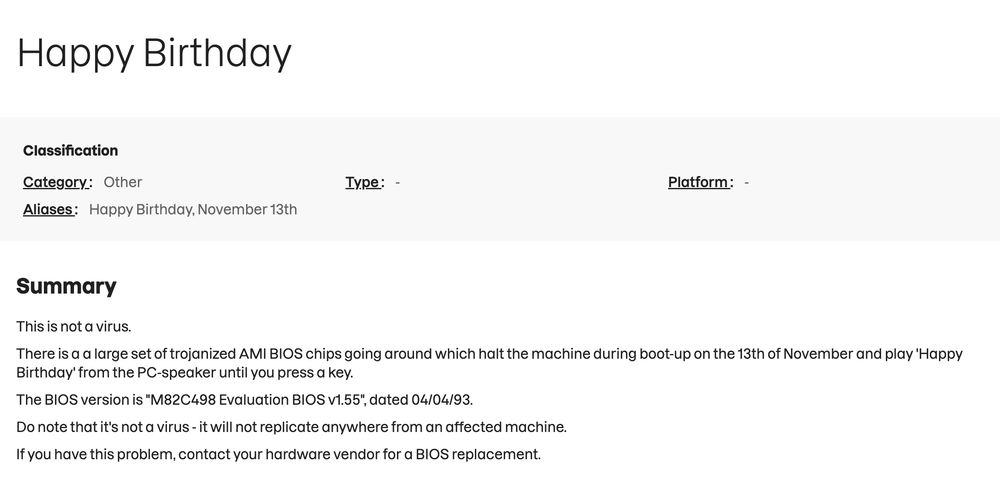
October 30, 2025 at 7:04 AM
so, apparently, some 90's motherboards using American Megatrends' BIOS had a "trojanized" BIOS which played happy birthday on november 13th. and I could NOT find any information on why or how this has happened
When launched, the trojanized Greenshot shows a fake compliance progress bar for 3 seconds, then confirms "All compliance checks passed!"
Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.
Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.

October 23, 2025 at 4:48 PM
When launched, the trojanized Greenshot shows a fake compliance progress bar for 3 seconds, then confirms "All compliance checks passed!"
Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.
Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.
Targets are attracted to a lucrative job offer and lured to execute trojanized PDF readers or VNC tools. This social engineering technique seems to have been working well for several years, suggesting many employees still have insufficient awareness of this tactic. 2/9
October 23, 2025 at 4:10 AM
Targets are attracted to a lucrative job offer and lured to execute trojanized PDF readers or VNC tools. This social engineering technique seems to have been working well for several years, suggesting many employees still have insufficient awareness of this tactic. 2/9
Cisco Talos reports on a new attack by the North Korean threat group Famous Chollima, which targets job seekers through fake offers, leading to the installation of malware. A compromised system in a Sri Lankan organization was infected via a trojanized Node.

BeaverTail and OtterCookie evolve with a new Javascript module
blog.talosintelligence.com
October 17, 2025 at 3:03 PM
Cisco Talos reports on a new attack by the North Korean threat group Famous Chollima, which targets job seekers through fake offers, leading to the installation of malware. A compromised system in a Sri Lankan organization was infected via a trojanized Node.
North Korean hackers combine BeaverTail and OtterCookie malware to target job seekers via trojanized Node.js apps. Stay vigilant against fake job offers. #CyberSecurity #MalwareAlert #JobScam Link: thedailytechfeed.com/north-korean...

October 17, 2025 at 9:22 AM
North Korean hackers combine BeaverTail and OtterCookie malware to target job seekers via trojanized Node.js apps. Stay vigilant against fake job offers. #CyberSecurity #MalwareAlert #JobScam Link: thedailytechfeed.com/north-korean...
North Korea’s Famous Chollima APT Uses Trojanized Node.js App to Deploy OtterCookie RAT for Crypto Theft
North Korea’s Famous Chollima APT Uses Trojanized Node.js App to Deploy OtterCookie RAT for Crypto T
securityonline.info
October 17, 2025 at 12:51 AM
North Korea’s Famous Chollima APT Uses Trojanized Node.js App to Deploy OtterCookie RAT for Crypto Theft
North Korean Hackers Using Malicious Scripts Combining BeaverTail and OtterCookie for Keylogging A new information-stealer has emerged targeting job seekers with a trojanized Node.js application na...
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match

North Korean Hackers Using Malicious Scripts Combining BeaverTail and OtterCookie for Keylogging
New info-stealer Chessfi targets job seekers via trojanized Node.js apps, stealing credentials and crypto through fake job offers.
cybersecuritynews.com
October 16, 2025 at 6:32 PM
North Korean Hackers Using Malicious Scripts Combining BeaverTail and OtterCookie for Keylogging A new information-stealer has emerged targeting job seekers with a trojanized Node.js application na...
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match
We identified a malvertising campaign targeting users searching for legitimate software, leading to the download of a trojanized WinSCP installer that deployed Broomstick/OysterLoader.
All files involved in the initial access phase were signed with valid certificates.
All files involved in the initial access phase were signed with valid certificates.

October 16, 2025 at 1:29 PM
We identified a malvertising campaign targeting users searching for legitimate software, leading to the download of a trojanized WinSCP installer that deployed Broomstick/OysterLoader.
All files involved in the initial access phase were signed with valid certificates.
All files involved in the initial access phase were signed with valid certificates.
~Zscaler~
An SEO poisoning campaign distributes a trojanized Ivanti VPN client to steal credentials for a C2 server.
-
IOCs: 4. 239. 95. 1, netml. shop, shopping5. shop
-
#Ivanti #SEOpoisoning #ThreatIntel
An SEO poisoning campaign distributes a trojanized Ivanti VPN client to steal credentials for a C2 server.
-
IOCs: 4. 239. 95. 1, netml. shop, shopping5. shop
-
#Ivanti #SEOpoisoning #ThreatIntel
SEO Poisoning Targets Ivanti VPN Users
www.zscaler.com
October 14, 2025 at 8:08 PM
~Zscaler~
An SEO poisoning campaign distributes a trojanized Ivanti VPN client to steal credentials for a C2 server.
-
IOCs: 4. 239. 95. 1, netml. shop, shopping5. shop
-
#Ivanti #SEOpoisoning #ThreatIntel
An SEO poisoning campaign distributes a trojanized Ivanti VPN client to steal credentials for a C2 server.
-
IOCs: 4. 239. 95. 1, netml. shop, shopping5. shop
-
#Ivanti #SEOpoisoning #ThreatIntel
🎮 Nostalgia turned into a forensic deep dive: what seemed like a harmless Flash game from the early 2000s was actually trojanized. A story of curiosity, trust and malware hidden in digital memories.
Come check it out at #WICCON2025 : wiccon.nl/schedule
Come check it out at #WICCON2025 : wiccon.nl/schedule

October 8, 2025 at 7:00 AM
🎮 Nostalgia turned into a forensic deep dive: what seemed like a harmless Flash game from the early 2000s was actually trojanized. A story of curiosity, trust and malware hidden in digital memories.
Come check it out at #WICCON2025 : wiccon.nl/schedule
Come check it out at #WICCON2025 : wiccon.nl/schedule

