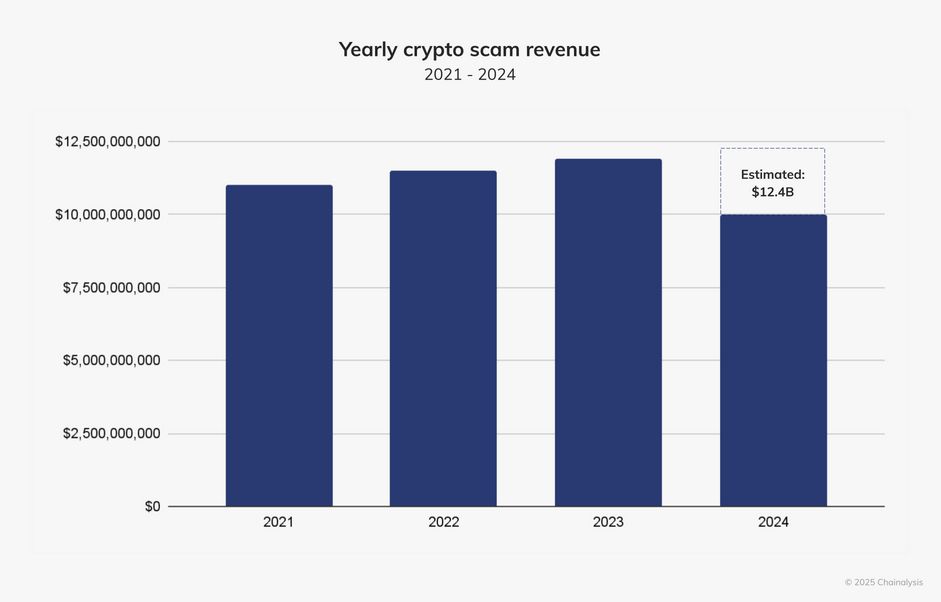
-Cyber scam profits expected to reach all-time high
-More malware found on HuggingFace, Steam, npm
-Brute-force campaign hits networking devices
-Variston shuts down
-New Italian spyware vendor uncovered (SIO)
-Malware reports on RansomHub, I2PRAT, Xloader, FinStealer, BadIIS, GhostWeaver, Godzilla
-More malware found on HuggingFace, Steam, npm
-Brute-force campaign hits networking devices
-Variston shuts down
-New Italian spyware vendor uncovered (SIO)
-Malware reports on RansomHub, I2PRAT, Xloader, FinStealer, BadIIS, GhostWeaver, Godzilla
February 17, 2025 at 10:17 AM
-Cyber scam profits expected to reach all-time high
-More malware found on HuggingFace, Steam, npm
-Brute-force campaign hits networking devices
-Variston shuts down
-New Italian spyware vendor uncovered (SIO)
-Malware reports on RansomHub, I2PRAT, Xloader, FinStealer, BadIIS, GhostWeaver, Godzilla
-More malware found on HuggingFace, Steam, npm
-Brute-force campaign hits networking devices
-Variston shuts down
-New Italian spyware vendor uncovered (SIO)
-Malware reports on RansomHub, I2PRAT, Xloader, FinStealer, BadIIS, GhostWeaver, Godzilla
The analysis reveals I2PRAT as an emerging threat with activity noted from October 2024 to January 2025. As part of the investigation and within our mission to enhance cyber threat #detection, we also share some #Sigma and #Suricata detection rules!
https://buff.ly/4b1SUnE
https://buff.ly/4b1SUnE

Community/IOCs/I2PRAT at main · SEKOIA-IO/Community
Welcome to the SEKOIA.IO Community repository! . Contribute to SEKOIA-IO/Community development by creating an account on GitHub.
buff.ly
February 17, 2025 at 9:19 AM
The analysis reveals I2PRAT as an emerging threat with activity noted from October 2024 to January 2025. As part of the investigation and within our mission to enhance cyber threat #detection, we also share some #Sigma and #Suricata detection rules!
https://buff.ly/4b1SUnE
https://buff.ly/4b1SUnE
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe

February 17, 2025 at 9:19 AM
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe


February 17, 2025 at 9:17 AM
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe


February 17, 2025 at 9:15 AM
🐭 RATatouille: Cooking Up Chaos in the I2P Kitchen
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
🔍 Our Threat Detection & Research (TDR) team has been analyzing a sophisticated new malware, #I2PRAT, featured in our latest FLINT report- now available in our blog!
https://buff.ly/3WVWpqe
Notícia da SecurityOnline
"Novo Malware I2PRAT: Avançado, Indetectável?" #bolhasec
"Novo Malware I2PRAT: Avançado, Indetectável?" #bolhasec

New I2PRAT Malware: Advanced, Undetectable?
Uncover the threat of I2PRAT malware, a sophisticated Remote Access Trojan targeting data security through I2P anonymity.
securityonline.info
February 14, 2025 at 5:30 PM
Notícia da SecurityOnline
"Novo Malware I2PRAT: Avançado, Indetectável?" #bolhasec
"Novo Malware I2PRAT: Avançado, Indetectável?" #bolhasec
How to remove I2PRAT I2PRAT is a sophisticated Remote Access Trojan (RAT) crafted in the C++ prog...
https://www.bugsfighter.com/remove-i2prat/
#Trojans #Viruses
Event Attributes
https://www.bugsfighter.com/remove-i2prat/
#Trojans #Viruses
Event Attributes
Awakari App
awakari.com
February 13, 2025 at 12:01 PM
How to remove I2PRAT I2PRAT is a sophisticated Remote Access Trojan (RAT) crafted in the C++ prog...
https://www.bugsfighter.com/remove-i2prat/
#Trojans #Viruses
Event Attributes
https://www.bugsfighter.com/remove-i2prat/
#Trojans #Viruses
Event Attributes
Sekoia's Pierre Le Bourhis analyses I2PRAT, a recent multi-stage RAT distributed as a ClickFix payload. blog.sekoia.io/ratatouille-...

February 12, 2025 at 10:43 AM
Sekoia's Pierre Le Bourhis analyses I2PRAT, a recent multi-stage RAT distributed as a ClickFix payload. blog.sekoia.io/ratatouille-...
I2PRAT: A New Stealthy Malware Exploiting Anonymization Networks
2025-02-11 In the ever-evolving world of cybersecurity, new threats constantly emerge, testing the limits of current defense mechanisms. One such threat is a newly identified Remote Access Trojan (RAT) called "I2PRAT," also known as…
2025-02-11 In the ever-evolving world of cybersecurity, new threats constantly emerge, testing the limits of current defense mechanisms. One such threat is a newly identified Remote Access Trojan (RAT) called "I2PRAT," also known as…

I2PRAT: A New Stealthy Malware Exploiting Anonymization Networks
2025-02-11 In the ever-evolving world of cybersecurity, new threats constantly emerge, testing the limits of current defense mechanisms. One such threat is a newly identified Remote Access Trojan (RAT) called "I2PRAT," also known as "Ratatouille." This sophisticated malware leverages the Invisible Internet Project (I2P), an encrypted peer-to-peer network, to anonymize its communications and evade detection. First observed in late 2024, I2PRAT has quickly become a significant concern for cybersecurity experts due to its advanced evasion techniques and the challenges it poses for traditional security measures.
undercodenews.com
February 12, 2025 at 9:41 AM
I2PRAT: A New Stealthy Malware Exploiting Anonymization Networks
2025-02-11 In the ever-evolving world of cybersecurity, new threats constantly emerge, testing the limits of current defense mechanisms. One such threat is a newly identified Remote Access Trojan (RAT) called "I2PRAT," also known as…
2025-02-11 In the ever-evolving world of cybersecurity, new threats constantly emerge, testing the limits of current defense mechanisms. One such threat is a newly identified Remote Access Trojan (RAT) called "I2PRAT," also known as…
GDATA's Banu Ramakrishnan analyses I2PRAT, a malware that uses I2P for CnC communication. I2PD, an open-source C++ implementation of I2P client, is used for this purpose. www.gdatasoftware.com/blog/2024/12...

December 19, 2024 at 11:16 AM
GDATA's Banu Ramakrishnan analyses I2PRAT, a malware that uses I2P for CnC communication. I2PD, an open-source C++ implementation of I2P client, is used for this purpose. www.gdatasoftware.com/blog/2024/12...
Notícia da SecurityOnline
"Novo Malware "I2PRAT" Explora a Rede I2P Anônima para Comando e Controle Discreto" #bolhasec
"Novo Malware "I2PRAT" Explora a Rede I2P Anônima para Comando e Controle Discreto" #bolhasec

New Malware “I2PRAT” Exploits Anonymous I2P Network for Stealthy Command and Control
A new malware campaign, identified as I2PRAT (I2P Remote Access Trojan), is raising the bar for cybercriminals’ ability to evade detection. Detailed in a report by Banu Ramakrishnan, a Malware...
The post New Malware “I2PRAT” Exploits Anonymous I2P Network for Stealthy Command and Control appeared first on Cybersecurity News.
securityonline.info
December 18, 2024 at 10:31 AM
Notícia da SecurityOnline
"Novo Malware "I2PRAT" Explora a Rede I2P Anônima para Comando e Controle Discreto" #bolhasec
"Novo Malware "I2PRAT" Explora a Rede I2P Anônima para Comando e Controle Discreto" #bolhasec
New Malware “I2PRAT” Exploits Anonymous I2P Network for Stealthy Command and Control securityonline.info/new-malware-...

New Malware “I2PRAT” Exploits Anonymous I2P Network for Stealthy Command and Control
Learn about the I2PRAT malware campaign, a sophisticated threat that leverages the Invisible Internet Project (I2P) to hide its activities and evade detection.
securityonline.info
December 18, 2024 at 4:35 AM
New Malware “I2PRAT” Exploits Anonymous I2P Network for Stealthy Command and Control securityonline.info/new-malware-...
Some recent malware reports
Xloader: sublime.security/blog/xloader...
Bizfum Stealer: www.cyfirma.com/research/biz...
Lumma Stealer: www.cybereason.com/blog/threat-...
CoinLurker: blog.morphisec.com/coinlurker-t...
I2PRAT: www.gdatasoftware.com/blog/2024/12...
Mamont: securelist.com/mamont-banke...
Xloader: sublime.security/blog/xloader...
Bizfum Stealer: www.cyfirma.com/research/biz...
Lumma Stealer: www.cybereason.com/blog/threat-...
CoinLurker: blog.morphisec.com/coinlurker-t...
I2PRAT: www.gdatasoftware.com/blog/2024/12...
Mamont: securelist.com/mamont-banke...

BIZFUM STEALER - CYFIRMA
EXECUTIVE SUMMARY CYFIRMA remains committed to providing timely insights into emerging threats, such as the recently uncovered “BIZFUM STEALER” on...
www.cyfirma.com
December 17, 2024 at 6:13 PM
Some recent malware reports
Xloader: sublime.security/blog/xloader...
Bizfum Stealer: www.cyfirma.com/research/biz...
Lumma Stealer: www.cybereason.com/blog/threat-...
CoinLurker: blog.morphisec.com/coinlurker-t...
I2PRAT: www.gdatasoftware.com/blog/2024/12...
Mamont: securelist.com/mamont-banke...
Xloader: sublime.security/blog/xloader...
Bizfum Stealer: www.cyfirma.com/research/biz...
Lumma Stealer: www.cybereason.com/blog/threat-...
CoinLurker: blog.morphisec.com/coinlurker-t...
I2PRAT: www.gdatasoftware.com/blog/2024/12...
Mamont: securelist.com/mamont-banke...
New I2PRAT communicates via anonymous peer-to-peer network https://www.gdatasoftware.com/blog/2024/12/38093-ip2rat-malware
I think it's quite interesting and somewhat novel to see a RAT C2-communication using I2P. While the rat itself is nothing special it's worth noting as a possible trend […]
I think it's quite interesting and somewhat novel to see a RAT C2-communication using I2P. While the rat itself is nothing special it's worth noting as a possible trend […]
Original post on swecyb.com
swecyb.com
December 16, 2024 at 9:26 AM
New I2PRAT communicates via anonymous peer-to-peer network https://www.gdatasoftware.com/blog/2024/12/38093-ip2rat-malware
I think it's quite interesting and somewhat novel to see a RAT C2-communication using I2P. While the rat itself is nothing special it's worth noting as a possible trend […]
I think it's quite interesting and somewhat novel to see a RAT C2-communication using I2P. While the rat itself is nothing special it's worth noting as a possible trend […]

