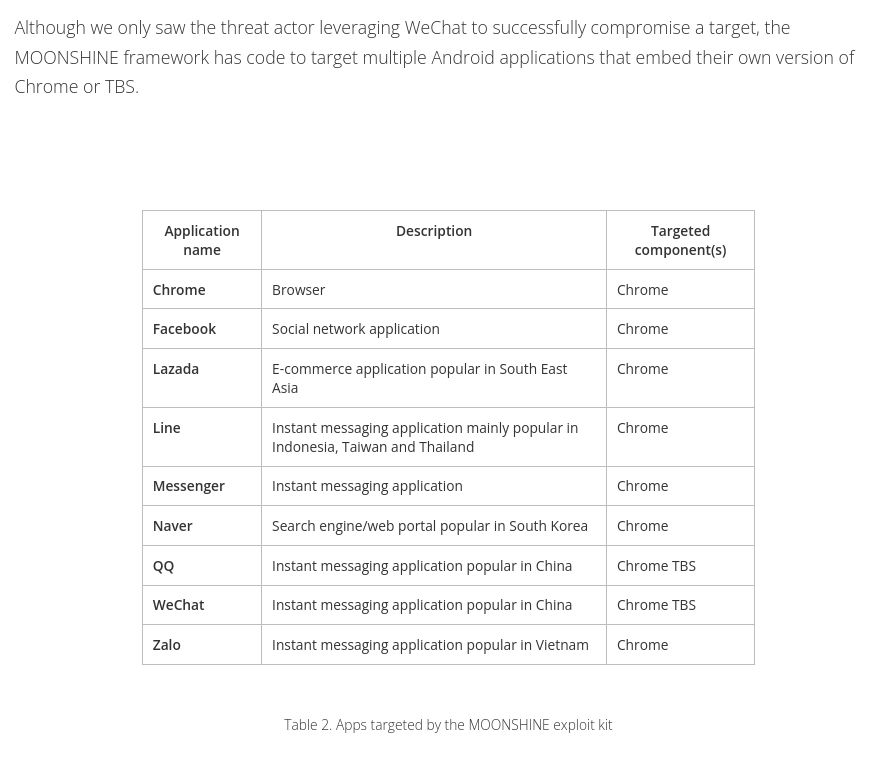
Regarding your question, this is what we wrote about Salt Typhoon in our third Earth Estries blogpost www.trendmicro.com/en_us/resear...

Regarding your question, this is what we wrote about Salt Typhoon in our third Earth Estries blogpost www.trendmicro.com/en_us/resear...




#APT
#APT
@citizenlab.ca
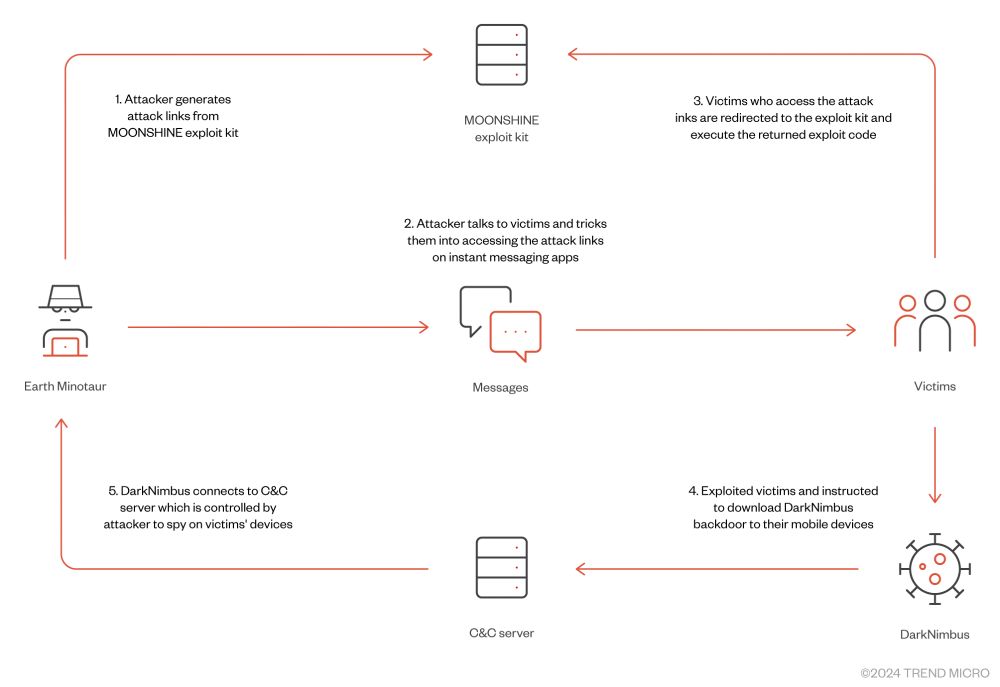
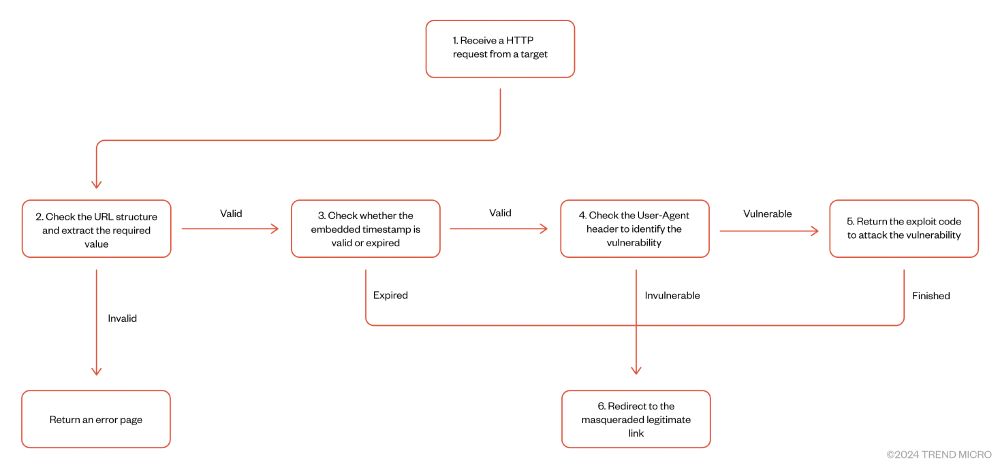
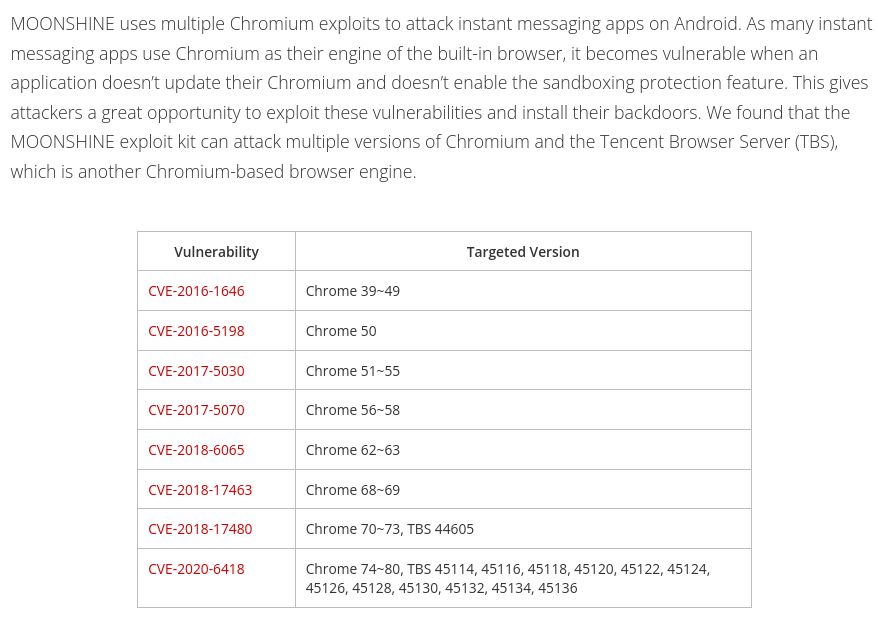
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...

