🔗 securite360.net/how-long-can...
#ApacheTomcat #Apache #GreyNoise #Vulnerability #CVE202524813

#ApacheTomcat #Apache #GreyNoise #Vulnerability #CVE202524813

🔗 securite360.net/how-long-can...
🔗 securite360.net/how-long-can...
#adint #cybercriminalité #sensibilisation
Merci #LeMonde pour cet excellent article.
www.lemonde.fr/pixels/artic...
#adint #cybercriminalité #sensibilisation
Merci #LeMonde pour cet excellent article.
www.lemonde.fr/pixels/artic...
Shout out to Nino Isakovic, @qutluch.bsky.social and @lukejenx.bsky.social
cloud.google.com/blog/topics/...

Shout out to Nino Isakovic, @qutluch.bsky.social and @lukejenx.bsky.social
cloud.google.com/blog/topics/...
ryan-weil.github.io/posts/LUMMA-...
#malware #infosec #stealer #writeup
ryan-weil.github.io/posts/LUMMA-...
#malware #infosec #stealer #writeup
As soon as the extensions were removed from the VSCode Marketplace, the attacker uploaded similar malicious projects on the npm portal.
www.reversinglabs.com/blog/a-new-p...
As soon as the extensions were removed from the VSCode Marketplace, the attacker uploaded similar malicious projects on the npm portal.
www.reversinglabs.com/blog/a-new-p...

regeringskansliet-se[.]cloud
dep-no[.]cloud
#infosec #apt
microsoft.com/en-us/security/b…
regeringskansliet-se[.]cloud
dep-no[.]cloud
#infosec #apt
microsoft.com/en-us/security/b…
krebsonsecurity.com/2024/05/star...

krebsonsecurity.com/2024/05/star...


The Apple notification looks like this: support.apple.com/en-us/102174
The Security Lab can be contacted here: securitylab.amnesty.org/get-help/
The Apple notification looks like this: support.apple.com/en-us/102174
The Security Lab can be contacted here: securitylab.amnesty.org/get-help/

Newsletter: news.risky.biz/risky-biz-ne...
-US charges five Scattered Spider members
-Apple fixes macOS zero-days
-T-Mobile finally stops a breach
-US takes down PopeyeTools carding portal
-Thailand throws out NSO lawsuit
-Microsoft develops something dumb, part 9,136

Newsletter: news.risky.biz/risky-biz-ne...
-US charges five Scattered Spider members
-Apple fixes macOS zero-days
-T-Mobile finally stops a breach
-US takes down PopeyeTools carding portal
-Thailand throws out NSO lawsuit
-Microsoft develops something dumb, part 9,136

Rejoignez nous pour les "têtards" !
contact@m82-project.org

Rejoignez nous pour les "têtards" !
contact@m82-project.org
The latest Qakbot payload distributed happened to be packed by the Dave crypter. The DLL decrypts a resource containing Dave's encrypted shellcode and executes it! (cf. securityintelligence.com/x-force/tric...)
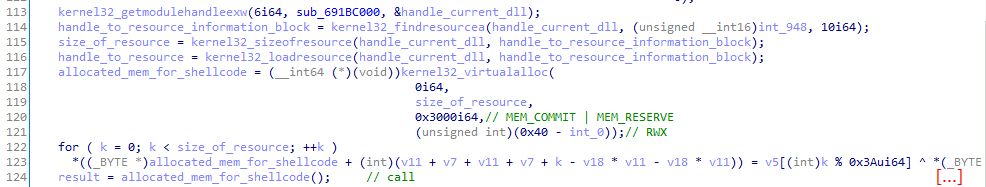
The latest Qakbot payload distributed happened to be packed by the Dave crypter. The DLL decrypts a resource containing Dave's encrypted shellcode and executes it! (cf. securityintelligence.com/x-force/tric...)

This report, initially drafted in July for our client, has been recently updated to include new victims we identified.
www.intrinsec.com/wp-content/u...

This report, initially drafted in July for our client, has been recently updated to include new victims we identified.
www.intrinsec.com/wp-content/u...
Botnet ID : is0210
RC4 key : NEW_BLACK
C2 : g7qf7ew5c[.]life
TTPs : .RAR -> .EXE

Botnet ID : is0210
RC4 key : NEW_BLACK
C2 : g7qf7ew5c[.]life
TTPs : .RAR -> .EXE


