
intuentis0x0
@intuentis0x0.bsky.social
CTI Analyst | Threat Hunter
based in europe
Opinions are my own
Mastodon: https://infosec.exchange/@intuentis0x0
Reddit: https://www.reddit.com/user/intuentis0x0/
Medium: https://medium.com/@intuentis0x0
X: https://x.com/intuentis0x0
based in europe
Opinions are my own
Mastodon: https://infosec.exchange/@intuentis0x0
Reddit: https://www.reddit.com/user/intuentis0x0/
Medium: https://medium.com/@intuentis0x0
X: https://x.com/intuentis0x0
Reposted by intuentis0x0
thedfirreport.com
September 29, 2025 at 2:49 PM
Reposted by intuentis0x0
Lateral movement getting blocked by traditional methods?
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG

DCOM Again: Installing Trouble - SpecterOps
DCOM lateral movement BOF using Windows Installer (MSI) Custom Action Server - install ODBC drivers to load and execute DLLs
ghst.ly
September 29, 2025 at 7:00 PM
Lateral movement getting blocked by traditional methods?
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
Come over this pretty intersting arcticel about Windows Defender Application Control (WDAC) policies to disable EDR agents. Very interesting. Also the first research regading this is worth a look.
beierle.win/2025-08-28-A...
#threatresearch
beierle.win/2025-08-28-A...
#threatresearch

A Nightmare on EDR Street: WDAC's Revenge
beierle.win
August 29, 2025 at 9:26 AM
Come over this pretty intersting arcticel about Windows Defender Application Control (WDAC) policies to disable EDR agents. Very interesting. Also the first research regading this is worth a look.
beierle.win/2025-08-28-A...
#threatresearch
beierle.win/2025-08-28-A...
#threatresearch
Reposted by intuentis0x0
🚨 Search for software, end up getting ransomware!
SEO-driven #Bumblebee malware campaigns observed throughout July led to domain compromise, data theft & #Akira ransomware. Tools included #AdaptixC2 & #Netscan.
thedfirreport.com/2025/08/05/f...
SEO-driven #Bumblebee malware campaigns observed throughout July led to domain compromise, data theft & #Akira ransomware. Tools included #AdaptixC2 & #Netscan.
thedfirreport.com/2025/08/05/f...
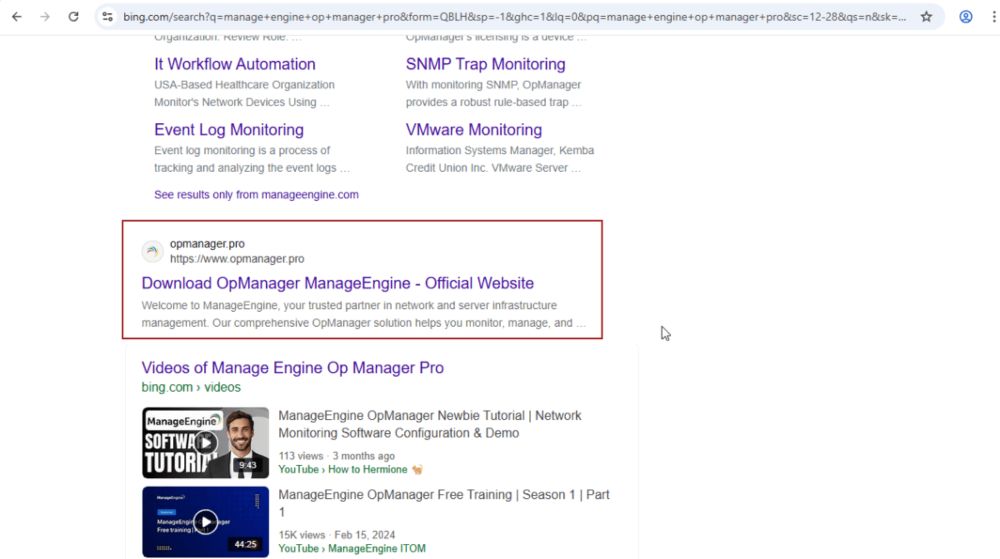
From Bing Search to Ransomware: Bumblebee and AdaptixC2 Deliver Akira
Overview Bumblebee malware has been an initial access tool used by threat actors since late 2021. In 2023 the malware was first reported as using SEO poisoning as a delivery mechanism. Recently in …
thedfirreport.com
August 5, 2025 at 12:39 PM
🚨 Search for software, end up getting ransomware!
SEO-driven #Bumblebee malware campaigns observed throughout July led to domain compromise, data theft & #Akira ransomware. Tools included #AdaptixC2 & #Netscan.
thedfirreport.com/2025/08/05/f...
SEO-driven #Bumblebee malware campaigns observed throughout July led to domain compromise, data theft & #Akira ransomware. Tools included #AdaptixC2 & #Netscan.
thedfirreport.com/2025/08/05/f...
This article does a good job of explaining why CTI isn't just for blue teams and why red teams can also benefit from good CTI analysts. I agree with many (though not all) of the points made here. CTI for red teams is a topic that’s discussed far too rarely.
blog.zsec.uk/offensive-cti/
#cti #redteam
blog.zsec.uk/offensive-cti/
#cti #redteam

Offensive Threat Intelligence
CTI isn’t just for blue teams. Used properly, it sharpens red team tradecraft, aligns ops to real-world threats, and exposes blind spots defenders often miss. It’s not about knowing threats, it’s abou...
blog.zsec.uk
June 27, 2025 at 2:08 PM
This article does a good job of explaining why CTI isn't just for blue teams and why red teams can also benefit from good CTI analysts. I agree with many (though not all) of the points made here. CTI for red teams is a topic that’s discussed far too rarely.
blog.zsec.uk/offensive-cti/
#cti #redteam
blog.zsec.uk/offensive-cti/
#cti #redteam
Ever seen how ransomware groups doing negotiations?
Here is a great site which make the leaked chats easy readable.
ransomch.at/viewer.html
Here is a great site which make the leaked chats easy readable.
ransomch.at/viewer.html
Ransomchat Viewer - Ransomch.at
ransomch.at
June 4, 2025 at 2:46 PM
Ever seen how ransomware groups doing negotiations?
Here is a great site which make the leaked chats easy readable.
ransomch.at/viewer.html
Here is a great site which make the leaked chats easy readable.
ransomch.at/viewer.html
this are good news.
honestly I didn't understand why MS needed its own naming when they started theire Threat Actor profiling. It does make no sense if vendor start using own naming schema and it doesn't make them smart nor make them looking professional.
www.microsoft.com/en-us/securi...
honestly I didn't understand why MS needed its own naming when they started theire Threat Actor profiling. It does make no sense if vendor start using own naming schema and it doesn't make them smart nor make them looking professional.
www.microsoft.com/en-us/securi...

Announcing a new strategic collaboration to bring clarity to threat actor naming | Microsoft Security Blog
Microsoft and CrowdStrike are teaming up to create alignment across our individual threat actor taxonomies to help security professionals connect insights faster.
www.microsoft.com
June 3, 2025 at 6:25 AM
this are good news.
honestly I didn't understand why MS needed its own naming when they started theire Threat Actor profiling. It does make no sense if vendor start using own naming schema and it doesn't make them smart nor make them looking professional.
www.microsoft.com/en-us/securi...
honestly I didn't understand why MS needed its own naming when they started theire Threat Actor profiling. It does make no sense if vendor start using own naming schema and it doesn't make them smart nor make them looking professional.
www.microsoft.com/en-us/securi...
Reposted by intuentis0x0
RedirectThread: Building more evasive primitives to use as alternative for existing process injection techniques
RedirectThread: Building more evasive primitives to use as alternative for existing process injection techniques
github.com
May 19, 2025 at 1:54 PM
RedirectThread: Building more evasive primitives to use as alternative for existing process injection techniques
just found this site which could help you find out the maturatiy of a SOC you maybe working in. That site also provides a SOC Maturity Report which is somehow interesting for Head-Of levels.
www.soc-cmm.com/products/soc...
www.soc-cmm.com/downloads/SO...
#soc #blueteam #cybersecurity #infosec
www.soc-cmm.com/products/soc...
www.soc-cmm.com/downloads/SO...
#soc #blueteam #cybersecurity #infosec
May 9, 2025 at 7:13 AM
just found this site which could help you find out the maturatiy of a SOC you maybe working in. That site also provides a SOC Maturity Report which is somehow interesting for Head-Of levels.
www.soc-cmm.com/products/soc...
www.soc-cmm.com/downloads/SO...
#soc #blueteam #cybersecurity #infosec
www.soc-cmm.com/products/soc...
www.soc-cmm.com/downloads/SO...
#soc #blueteam #cybersecurity #infosec
Eventlogs can be somehow overwhelming. Found this one here which could be helpful for #detectionengineering
eventlog-compendium.streamlit.app
eventlog-compendium.streamlit.app

Eventlog Compendium
is the one-stop shop utility designed to simplify Windows security event log analysis, audit pol...
eventlog-compendium.streamlit.app
April 23, 2025 at 8:54 AM
Eventlogs can be somehow overwhelming. Found this one here which could be helpful for #detectionengineering
eventlog-compendium.streamlit.app
eventlog-compendium.streamlit.app
Reposted by intuentis0x0
I boosted several posts about this already, but since people keep asking if I've seen it....
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration […]
[Original post on infosec.exchange]
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration […]
[Original post on infosec.exchange]

April 15, 2025 at 8:33 PM
I boosted several posts about this already, but since people keep asking if I've seen it....
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration […]
[Original post on infosec.exchange]
MITRE has announced that its funding for the Common Vulnerabilities and Exposures (CVE) program and related programs, including the Common Weakness Enumeration […]
[Original post on infosec.exchange]
Just read this amazing article about #processinjection technique #doppelganger
This one here gives a detailed and understandable inside of this technique for #redteam and #blueteam equally.
vari-sh.github.io/posts/doppel...
This one here gives a detailed and understandable inside of this technique for #redteam and #blueteam equally.
vari-sh.github.io/posts/doppel...
Doppelganger: Cloning and Dumping LSASS to Evade Detection
Technique for cloning and dumping LSASS to evade detection using RTCore64.sys, NtCreateProcessEx and MiniDumpWriteDump.
vari-sh.github.io
April 14, 2025 at 1:58 PM
Just read this amazing article about #processinjection technique #doppelganger
This one here gives a detailed and understandable inside of this technique for #redteam and #blueteam equally.
vari-sh.github.io/posts/doppel...
This one here gives a detailed and understandable inside of this technique for #redteam and #blueteam equally.
vari-sh.github.io/posts/doppel...
Reposted by intuentis0x0
Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

April 8, 2025 at 11:00 PM
Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Reposted by intuentis0x0
🌟New report out today!🌟
Fake Zoom Ends in BlackSuit Ransomware
Analysis and reporting completed by @pigerlin, UC1 and @Miixxedup
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/03/31/f...
Fake Zoom Ends in BlackSuit Ransomware
Analysis and reporting completed by @pigerlin, UC1 and @Miixxedup
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/03/31/f...

Fake Zoom Ends in BlackSuit Ransomware
Key Takeaways The threat actor gained initial access by a fake Zoom installer that used d3f@ckloader and IDAT loader to drop SectopRAT. After nine days of dwell time, the SectopRAT malware dropped …
thedfirreport.com
March 31, 2025 at 11:38 AM
🌟New report out today!🌟
Fake Zoom Ends in BlackSuit Ransomware
Analysis and reporting completed by @pigerlin, UC1 and @Miixxedup
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/03/31/f...
Fake Zoom Ends in BlackSuit Ransomware
Analysis and reporting completed by @pigerlin, UC1 and @Miixxedup
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/03/31/f...
Reposted by intuentis0x0
By making minor changes to command-line arguments, it is possible to bypass EDR/AV detections.
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...

March 24, 2025 at 9:08 AM
By making minor changes to command-line arguments, it is possible to bypass EDR/AV detections.
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...
Great tool to work with sigma rules and conversions to Splunk SPL, Elastics EQL and much more. This should make Detection Engineering comfortable.
#detectionengineering #blueteam #detections #infosec
detection.studio
#detectionengineering #blueteam #detections #infosec
detection.studio

Detection Studio – detection.studio
Design, build and share detection rules for your security tools.
detection.studio
March 12, 2025 at 10:33 AM
Great tool to work with sigma rules and conversions to Splunk SPL, Elastics EQL and much more. This should make Detection Engineering comfortable.
#detectionengineering #blueteam #detections #infosec
detection.studio
#detectionengineering #blueteam #detections #infosec
detection.studio
Found this interesting article about the cyber incident at MITRE last year. Really appreciate the technical explanations and the sharing intention here.
#blueteam #threatreport #mitre
medium.com/mitre-engenu...
#blueteam #threatreport #mitre
medium.com/mitre-engenu...

Technical Deep Dive: Understanding the Anatomy of a Cyber Intrusion
MITRE’s experiences detecting and responding to a nation-state cyber threat actor incident in our research and experimentation network
medium.com
February 26, 2025 at 3:57 PM
Found this interesting article about the cyber incident at MITRE last year. Really appreciate the technical explanations and the sharing intention here.
#blueteam #threatreport #mitre
medium.com/mitre-engenu...
#blueteam #threatreport #mitre
medium.com/mitre-engenu...
Reposted by intuentis0x0
🌟New report out today!🌟
Confluence Exploit Leads to LockBit Ransomware
Analysis & reporting completed by Angelo Violetti, @malforsec, & @teddy_ROxPin
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/02/24/c...
Confluence Exploit Leads to LockBit Ransomware
Analysis & reporting completed by Angelo Violetti, @malforsec, & @teddy_ROxPin
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/02/24/c...

Confluence Exploit Leads to LockBit Ransomware
Key Takeaways The intrusion began with the exploitation of CVE-2023-22527 on an exposed Windows Confluence server, ultimately leading to the deployment of LockBit ransomware across the environment.…
thedfirreport.com
February 24, 2025 at 12:48 PM
🌟New report out today!🌟
Confluence Exploit Leads to LockBit Ransomware
Analysis & reporting completed by Angelo Violetti, @malforsec, & @teddy_ROxPin
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/02/24/c...
Confluence Exploit Leads to LockBit Ransomware
Analysis & reporting completed by Angelo Violetti, @malforsec, & @teddy_ROxPin
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/02/24/c...
Reposted by intuentis0x0
February 21, 2025 at 10:18 PM


