It costs $9.99/mo, which after 3 years, costs about the same as a 3-year DigiCert — all without the antiquated ID verification.
It costs $9.99/mo, which after 3 years, costs about the same as a 3-year DigiCert — all without the antiquated ID verification.
Also, check out that NotAfter and NotBefore, so short!
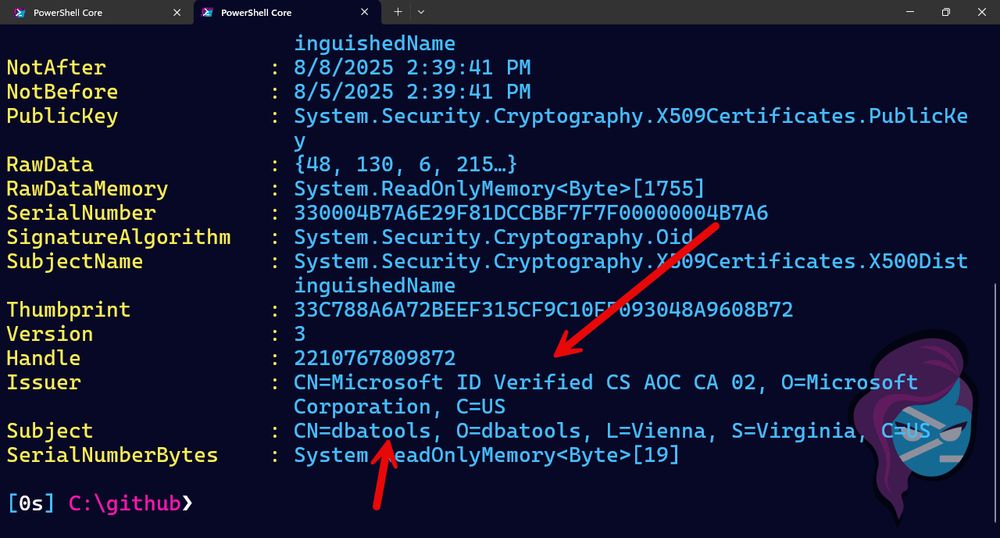
Also, check out that NotAfter and NotBefore, so short!
Oh and going back to Install-Module, if you switch to Install-PSResource, that bypasses the SkipPublisherCheck requirement.
```
Install-Module Microsoft.PowerShell.PSResourceGet
```
Oh and going back to Install-Module, if you switch to Install-PSResource, that bypasses the SkipPublisherCheck requirement.
```
Install-Module Microsoft.PowerShell.PSResourceGet
```
If this sounds concerning to you, the post below should provide you with reassurance. Also, most if not all of us on the dev team set our Execution Policies to Bypass or Unrestricted if we can.

If this sounds concerning to you, the post below should provide you with reassurance. Also, most if not all of us on the dev team set our Execution Policies to Bypass or Unrestricted if we can.
Add this Import-Dbatools function to your profile to auto-trust certs:

Add this Import-Dbatools function to your profile to auto-trust certs:
Azure Trusted Signing provides instant reputation tied to our verified identity & not to a specific cert like the old way. Should finally solve years of false positives.
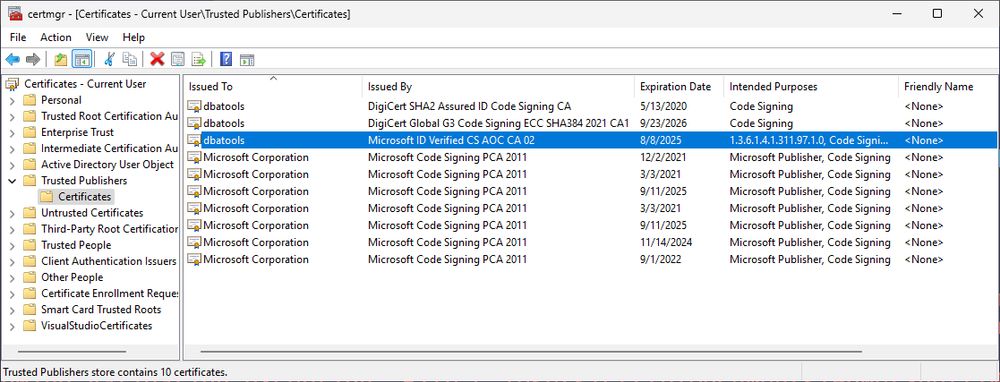
Azure Trusted Signing provides instant reputation tied to our verified identity & not to a specific cert like the old way. Should finally solve years of false positives.
```
Install-Module dbatools -Force -SkipPublisherCheck
```
After that initial transition, you won't need SkipPublisherCheck again since our cert keeps the same subject and root CA for version 2.5.5+ onward.
```
Install-Module dbatools -Force -SkipPublisherCheck
```
After that initial transition, you won't need SkipPublisherCheck again since our cert keeps the same subject and root CA for version 2.5.5+ onward.

